Active Directory is the network-based directory service for Windows Server 2003. You use Active Directory to organize and store large volumes of data on a computer network. Active Directory divides the data into two layers, logical and physical.
The logical layer categorizes data into partitions based on the network objects such as users and computers. The logical layer helps you to monitor and control data access on the network. The physical layer manages data storage on the hard disk of a server.
This ReferencePoint describes the logical and physical layers of Active Directory. It also covers the domain trusts and the Domain Name System (DNS) feature that allows you to access computers and network resources. In addition, this ReferencePoint explains how Active Directory replicates data to different Active Directory partitions.
Introducing Active Directory and its Structural Components
Active Directory is a database for storing information about users, computers, and other network resources. It also contains a set of services that help you to retrieve, modify, and delete data from the Active Directory database.
You can use Active Directory as an:
-
Internal directory for publishing information about users and resources within a company.
-
External directory for storing information about the clients who access specific company information such as a catalog or a client list.
-
Application directory for storing the data of all applications, which exist on the same computer as the Active Directory service.
The components of the Active Directory data structure include:
-
Logical structure: Divides the data in Active Directory into partitions to efficiently distribute and maintain data throughout the network.
-
Schema: Contains the definitions of the Active Directory objects that store information about various network resources, such as the computers, printers, users, and groups in Active Directory. The object definitions in the Active Directory schema consist of data type and syntax of data. Active Directory uses the object definitions to validate the data stored in the Active Directory database.
-
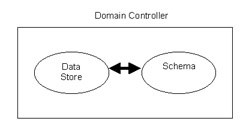
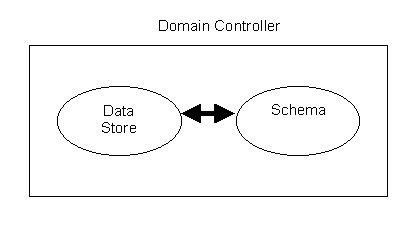
Data store: Manages storage and retrieval of data from the domain controllers. A domain controller is a server that contains a copy of the Active Directory database.
-
Physical structure: Contains a database that helps in the replication and transfer of data in Active Directory.
Logical Structure of Active Directory
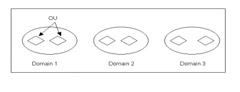
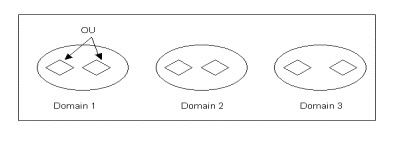
The Active Directory logical structure contains three elements that help you to organize data in the Active Directory database:
-
Domain: Divides the data stored in Active Directory into partitions such that Active Directory can control the data storage on domain controllers. Domains are arranged hierarchically in the form of domain trees.
-
Forest: Represents a self-contained directory that you can use to control access permissions to the data stored in a forest. You can also control access permissions on the domain controller that implements a specific forest.
-
Organizational Unit (OU): Helps you to group user or computer accounts as a single entity for efficient management. You can use OUs to control the access permissions of many users on a single resource simultaneously.
| Note | A domain tree is a contiguous namespace, which means that the child domains form a continuation of the naming hierarchy. For example, stream.College.com represents a child domain of the College.com domain, and semester.stream.College.com represents a child domain of the stream.College.com domain. |
A forest is the highest-level element of the logical structure hierarchy. A forest contains various domains of Active Directory, and each domain consists of a domain controller, which stores the information corresponding to that domain. A domain also contains OUs.
Figure 14-3-1 shows the logical structure of Active Directory:
Directory stores information related to a forest on all domain controllers and transfers the data of a particular forest to all the domain controllers. Active Directory transfers the data of a specific domain only to the domain controllers in that particular domain. To access multiple domains in different domain trees, you need to establish a forest connection. To connect to a forest:
-
Select Settings->Control Panel->Administrative Tools->Active Directory Sites and Services. The Active Directory Sites and Services window appears, as shown in Figure 14-3-2:
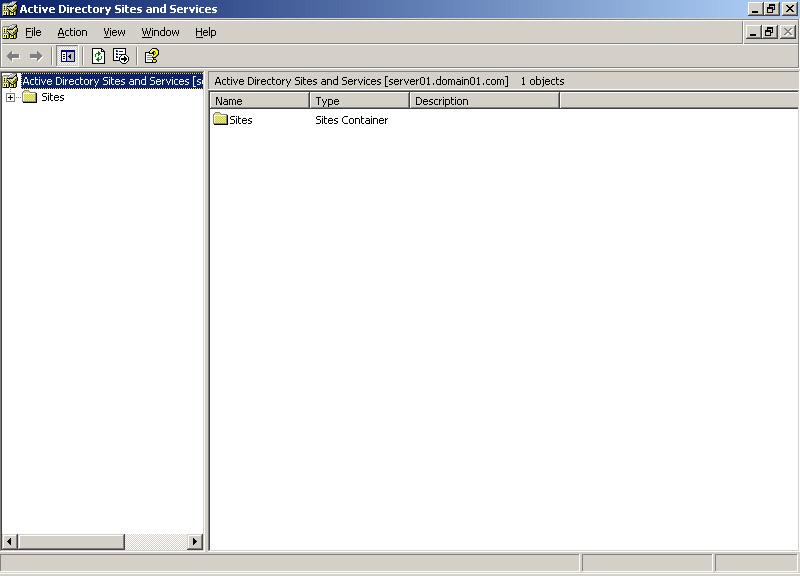
Figure 14-3-2: The Active Directory Sites and Services WindowNote A site is a group of computers in a small network that allows network communication by using the TCP/IP addresses.
-
Right-click the Active Directory Sites and Services icon in the console tree. A shortcut menu appears, as shown in Figure 14-3-3:
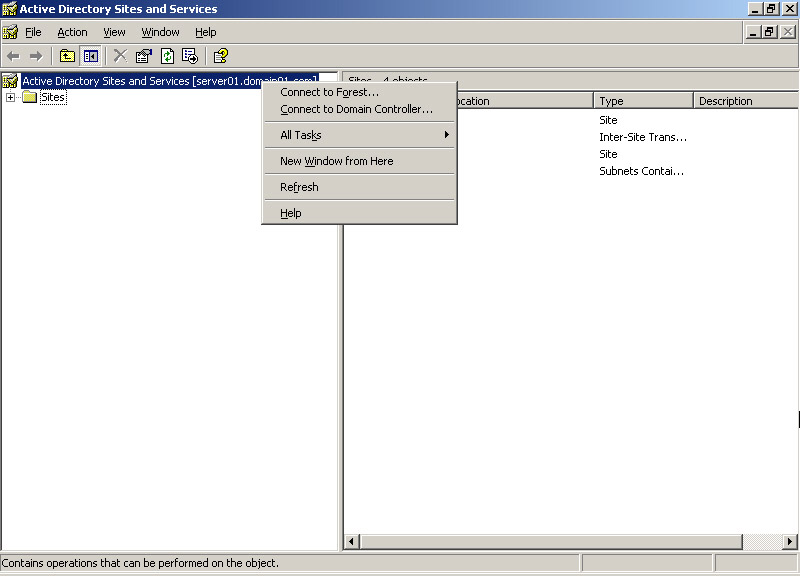
Figure 14-3-3: The Shortcut Menu of Active Directory Sites and Services
-
Select the Connect to Forest option from the shortcut menu. The Connect to Forest dialog box appears, as shown in Figure 14-3-4:
-
Type domain01.com in the Root domain text box to specify the name of the root domain to which you need to make a connection. Click OK to close the Connect to Forest dialog box.
Active Directory Schema
Schema is the element of the Active Directory structure that defines all the objects and attributes in the Active Directory service. Active Directory consists of a schema partition that stores the Active Directory schema.
| Note | In Active Directory, an instance of the Directory Management Domain (DMD) class represents the Active Directory schema partition as an object. |
The three elements that the Active Directory schema defines are:
-
Active Directory objects to store data.
-
Rules that govern the structure of the object definitions present in the Active Directory schema.
-
Structure and content of Active Directory.
The default Active Directory schema contains the object definitions for all types of data stored in Active Directory. The object definitions ensure that the Active Directory objects conform to their standard definitions.
When you use Active Directory to manage data, Active Directory queries the schema for a particular object definition. Based on this object definition, Active Directory creates an object and stores data in the object. If an object definition does not exist in the Active Directory schema, the object cannot store data in the Active Directory database.
An object definition stored in the Active Directory schema contains three elements:
-
Objects: Store the data that controls the structure of the Active Directory objects. For example, the user name object contains the name of a user and the syntax to store the user name.
-
Attributes: Define the information stored in an object. Active Directory uses the syntax attribute to ensure that the information stored in an attribute is a valid data type. The syntax attribute defines a standard format for storing the data in an attribute.
-
Classes: Determine the attributes that should be associated with an Active Directory object. When Active Directory creates a new object, the class of the new object determines the attributes that should be associated with the new object.
Active Directory uses these elements to specify one object definition for all the objects containing a common attribute. For example, some objects contain a security feature attribute that specifies the access permissions associated with various objects. The Active Directory schema then defines only one object definition for all the objects that require the security feature attribute, instead of creating separate object definitions for each object. All the objects can refer to this object definition for specifying the security permissions to access the contents of these objects.
| Note | Active Directory contains some predefined classes that contain the description of all the object types the Active Directory service uses to perform its functions. |
The attributes and classes in Active Directory are stored as directory objects, called schema objects, in the Active Directory schema. There are two types of schema objects:
-
classSchema: Defines the classes in the Active Directory schema. For example, when Active Directory creates a new group, it uses the group class as the object definition. The new group uses the attributes of the group class to retrieve the information stored in this class.
-
attributeSchema: Defines the attributes in the Active Directory schema. For example, a group class can consist of various attributes that store the information related to the group, such as the group name and group ID. An attribute of the class can also contain other attributes that specify the type of data that can be assigned to an attribute, the syntax of the attribute value, and whether the attribute is optional or mandatory. Active Directory uses the attributeSchema object to verify the information stored in a class attribute. An attribute stored in the attributeSchema object can also specify the name of another attribute, its syntax, its range, and the information about the indexing of the attribute.
You can add the attributes to the Active Directory schema by extending the schema. The process of modifying or updating the Active Directory schema is known as extending the schema. To add or modify an attribute or class definition, you need to add or modify the corresponding attributeSchema or classSchema object.
When you change an object or its properties, the Active Directory schema replicates the changes to all the domain controllers in a forest. You should make changes to the Active Directory schema in a restricted manner, because any change to the Active Directory schema affect all the domain controllers in a forest.
| Note | When you install Active Directory, the Schema.ini file creates a default Active Directory schema on the first domain controller in a forest. |
Active Directory Data Store
The Active Directory data store is a database that stores and distributes different types of data, such as user and application data, to the network clients. The Active Directory data store contains database files that store and manage information about the users, services, and applications in an organization. Active Directory data store features include:
-
Lightweight Directory Access Protocol (LDAP) and Messaging Application Programming Interface (MAPI) support to access the data in the data store.
-
Support for the query and index mechanisms to search the data in the data store.
-
Support for a hierarchical or tree model for storing the data.
-
Implementing the Active Directory schema to ensure data consistency.
| Note | The Active Directory data store uses the object definitions stored in the Active Directory schema to provide data integrity. |
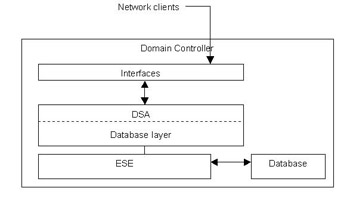
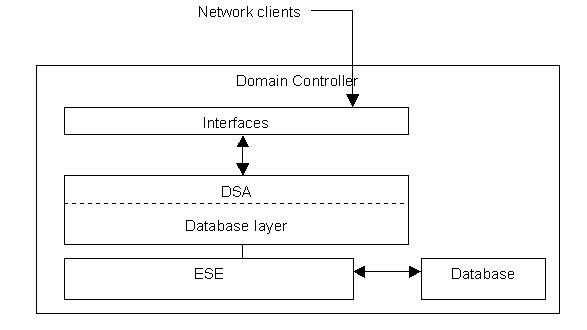
The Active Directory data store consists of various components that provide the directory services to the Active Directory clients. These components consist of four interfaces, three service components, and a directory database that stores data.
Figure 14-3-5 shows the structure of the Active Directory data store:
Directory System Agent (DSA) provides the interfaces that help the network clients to access the Active Directory database. DSA is stored as the Ntdsa.dll file on each domain controller. The four interfaces in the data store are: LDAP, MAPI, Security Accounts Manager (SAM), and REPLication (REPL) and domain controller management interface.
Figure 14-3-6 shows the relationship between the Active Directory schema and data store:
Physical Structure of Active Directory
The physical structure of Active Directory represents the process of data communication and replication by using sites and domain controllers. Sites manage the communication within a network. Domain controllers store and replicate the Active Directory data.
| Note | Active Directory replication is the process by which changes originating on one domain controller are automatically copied to the other domain controllers containing the same data. |
An Active Directory site consists of one or more Internet Protocol (IP) subnets connected to each other. A subnet contains a set of computers connected by a high-speed network, such as Local Area Network (LAN). A site provides a means for rapid data transmission across a network. Active Directory sites functions include:
-
Replication: Stores the up-to-date information within Active Directory.
-
Authentication: Verifies the identity of an Active Directory object.
| Note | An Active Directory site can contain multiple domains. When you install Active Directory, a domain controller is assigned to a specific site. This site retains the domain controller unless you relocate the domain controller. An Active Directory object that represents a set of sites communicating with each other through a transport layer is called a site link object. Active Directory uses the information stored in the site link objects to create a replication topology. Active Directory depends on the site configuration settings to manage and optimize the replication process. To create a site: |
-
Select Settings->Control Panel->Administrative Tools->Active Directory Sites and Services. The Active Directory Sites and Services window appears.
-
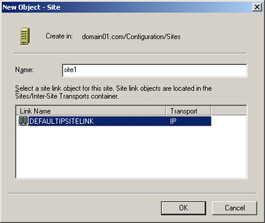
Right-click the Sites folder and select the New Site option from the shortcut menu. The New Object-Site dialog box appears, as shown in Figure 14-3-7:
-
Type site1 as the name of the new site in the Name text box.
-
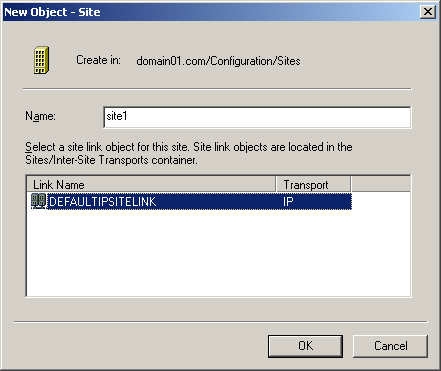
Select a site link object for site1 from the Link Name list and click OK.
Figure 14-3-8 shows the link name selected for the new site, site1:
To improve the network performance in a multiple site environment, you need to add the Global Catalog (GC) domain controller to the sites. The GC contains the partial replicas of the Active Directory objects and the Active Directory schema. Active Directory automatically creates the GC on the initial domain controller in a forest. A GC performs the following two functions:
-
Acts as a domain controller to store the object data and resolve the queries related to the objects and attributes.
-
Provides the data that helps in network logon.
| Note | In the absence of a GC, you can logon only to a local system. |
Replicating Active Directory
Data replication on a domain controller tracks the data changes the domain controller receives, and updates only the changes that occur after the previous replication. This process ensures that the data changes are updated on all the domain controllers.
The process of tracking changes in the domain controllers, called update tracking process, depends on the state of the data at the time of replication. The update tracking process ensures that replication occurs only for data changes that a domain controller does not receive. The update tracking process does not allow you to make simultaneous changes to the same object in two domain controllers.
In the Active Directory replication process, a domain controller requests only for the data changes, which it needs to replicate. The domain controller then forwards these data changes to other domain controllers that need to be updated. The Active Directory replication process uses the sites to perform the functions related to the replication process. The various functions related to the replication process are:
-
Optimizing the replication between the domain controllers.
-
Locating the nearest domain controller for client logon and directory search.
-
Replicating the system volume (Sysvol), which is a collection of folders of each domain controller in a domain.
Understanding the Active Directory Data Replication Model
The Active Directory replication model helps the destination domain controller to store and forward the replicated changes to other domain controllers. This model eliminates the need for a domain controller, on which a change occurs, to communicate with the other domain controllers that need to be updated.
The Active Directory replication model ensures the availability of the domain controllers for updates. This model ensures minimum replication traffic and maximum efficiency to retrieve only the required changes. The replication model also resolves conflict to ensure replication of only a single value to all the domain controllers even if you make simultaneous changes to the same attribute on different domain controllers.
There are two types of replication models:
-
Multimaster: Specifies that Active Directory can make changes to any domain controller. Windows Server 2003 Active Directory uses the multimaster replication model.
-
Single-master: Specifies that one domain controller stores the modifiable copy of the directory and all the other domain controllers store the back up copies of the directory.
Some events on the domain controllers within a forest trigger immediate replication as follows:
-
Prohibiting an end user from logging on after a specified number of failed logon attempts.
-
Changing the Local Security Authority (LSA) secret, which is a secure form in which the LSA API stores private data.
-
Changing the Relative Identifier (RID) manager, which is the domain controller that assigns a unique SID to the objects in a domain.
-
Changing the password on a domain controller computer account.
Understanding Replication Methods
Active Directory uses either the Remote Procedure Call (RPC) or Simple Mail Transport Protocol (SMTP) for communicating with the network entities. RPC consists of an encryption methodology, which is an essential component of replication.
In an RPC transaction, a client makes a function call to the RPC server. If the client has to wait for a long time to obtain a response, the client gets disconnected. Active Directory uses two forms of RPCs, a high-speed form for use in a Local Area Network (LAN), and a low-speed form for use in a Wide Area Network (WAN).
Active Directory can also use SMTP to transfer the replication packets between the domain controllers. SMTP supports asynchronous communication and allows the transfer of replication packets in bulk. The limitations of using SMTP for Active Directory replication are:
-
SMTP transfers the messages in the form of text. The Active Directory replication system automatically encrypts the SMTP messages by using a secure form for messaging. This form of encryption uses certificates issued by a certification authority. As a result, the load on the server increases.
-
SMTP cannot be used to replicate the contents of the Domain naming context because the contents of the system volume, Sysvol, cannot be synchronized. The Domain naming context stores administrative information for Active Directory objects, such as users, computers, and printers.
| Note | Each replicated component of Active Directory database is called a naming context. It is of three types: Domain, Configuration, and Schema. |
Understanding Property Replication
Active Directory does not replicate the entire content of a naming context for each update within a domain controller. Instead, it replicates only the contents that change. Active Directory replicates the individual properties of an object instead of the entire object.
To control property replication, Active Directory uses the property metadata. Property metadata consists of information such as when the property was last modified, where the modification occurred, and the number of revisions applied to the property. Each domain controller contains a property metadata that indicates the status of data changes relative to the other domain controllers.
Active Directory uses a replication mechanism where there is a time gap between the modification of a property in one replica and the replication of the modified property to all other domain controllers in a forest. The time required for Active Directory to replicate a modified property to all the domain controllers is called convergence time. Ideally, the convergence time should be zero. This means that the changes should be instantly updated to all the domain controllers in a forest.
Controlling Replication Parameters
Active Directory uses two methods to control the convergence time, notification and polling.
In the notification method, if a domain controller modifies a property in any of its naming context, the domain controller reports the change to the other domain controllers that need to be replicated. The other domain controllers obtain a copy of the changed property, and apply the changed property to their naming context replica. These domain controllers, in turn, notify their replication partners about the property change. As a result, the property change propagates within a forest.
Replication partners are the domain controllers that need to be updated based on the data changes in Active Directory. By default, the time taken to complete the notification method is 15 seconds. If the time taken to complete the notification method is less, the replication traffic becomes high. Active Directory employs the notification method to replicate the changes on the domain controllers in the same forest.
In the polling method, the domain controllers periodically query their replication partners to check if there is any data change within a forest. By default, the time required to complete the polling method between the domain controllers in the same forest is one hour. If any data change occurs during this time interval, the change is propagated to the domain controllers after one hour.
The time required to complete the polling method acts as a status check to specify if there is a change in any domain controller during this interval. In addition, the default time required to complete the polling method between the domain controllers in different forests is three hours.
| Note | If the time required to complete the polling process is less, the convergence time is reduced. |
In an intra-site replication, a domain controller sends a message regarding the data change to the other domain controllers five minutes after the domain controller receives an update. In the inter-site replication, the time required to complete the polling process controls data replication between the domain controllers.
If a domain controller updates the copy of a naming context, the domain controller notifies its replication partners to obtain a replica of the updated data. The domain controller sends the information about the update to one of the replication partners, and then waits for 30 seconds before notifying this update to the other partners. The registry values control the notification intervals, which are either stored under the HKLM|system or at the CurrentControlSet |NTDS|Parameters directory location. These notification intervals are:
-
Replicator notify pause after modify: Specifies a notification interval of -300 seconds.
-
Replicator notify pause between DSAs: Specifies a notification interval of -30 seconds.
| Tip | To reduce the notification interval, reduce the Replicator notify pause after modify interval. |
Handling Replication Collision
Active Directory replication can lead to simultaneous changes in the same attribute on different domain controllers. These simultaneous changes in the same attribute are called collisions. Various causes of collision between domain controllers in a forest are:
-
Modifying a property on different domain controllers simultaneously.
-
Creating two or more objects with the same name in the same container on different domain controllers.
-
Modifying a property of an object on one domain controller, and moving the object with the modified property to a different container on another domain controller.
-
Modifying a property of an object on one domain controller and deleting the object from another domain controller.
Deleted objects are not immediately removed from the Active Directory database because Active Directory transfers the information about the deletion of the objects to all the replication partners of a domain controller. The domain controller from which you delete the object notifies this change to the replication partners.
The replication partners of the specified domain controller receive a replication packet, which contains the updated information about the deleted objects. The replication partners change the Distinguished Name (DN) of the object, remove the attributes of the deleted object, and move the object to a container called Deleted Objects.
| Note | A DN is an Active Directory object name that uniquely identifies an object. |
Objects in the Deleted Objects container are called tombstones. The time interval for which a tombstone remains in this container is called tombstone interval. In Active Directory, the tombstone interval is 60 days. When the tombstone interval for a particular object ends, the object is removed from the Active Directory database.
Collision also occurs if you change an object property, and at the same time, a member on the other domain controller moves the object to a different container. The domain controller, where the object is moved, receives the update of the object property. The DN associated with the object is changed, but the DN associated with the object property remains the same.
A collision problem can also occur due to the modification of an object property on one domain controller and the transfer of the modified property to a different container on another domain controller. Active Directory overcomes this collision problem by using the Globally Unique Identifier (GUID) of the object, which does not change even if the DN changes. Active Directory performs a lookup for the object GUID, finds the new DN, and updates the object property at the correct location.
| Note | GUID of an Active Directory object is a 128-bit unique number within a forest. |
Troubleshooting Replication Errors
Active Directory replication consists of complex transactions. A failure in any one of the transactions causes errors. Replication errors are caused due to unstable server hardware, poor network connections, and DNS errors. When there is a replication error, an error log message appears. Active Directory contains the following tools that help you to identify the cause of a replication error:
-
Diagnostic traces
-
Command-line replication administration utility, REPADMIN
-
Graphical replication monitor utility, Replmon
You can use the registry values to find the cause of a replication error. The settings for a diagnostic trace are:
-
Minimum reporting: Occurs when the registry value is set to 1.
-
Moderate reporting: Occurs when the registry value is set to 3.
-
Full reporting: Occurs when the registry value is set to 5.
The amount of information that you want to store about the log files of Active Directory depends on the value set in the registry. For example, full reporting stores the entire information about the log files, minimum reporting stores only a little information, and moderate reporting stores average information. You can access the log file using the following path:
HKLM | System | CurrentControlSet | Services | NTDS | Diagnostics
| Note | The log file stores information about the errors, log in attempts, and log off attempts. |
Introducing Domain Trust and DNS
A domain acts as a security boundary that restricts you from accessing the objects in another domain. A domain specifies the permissions for a group containing specific users. A trust relationship between the domains allows the members in one domain to access the resources in another domain, without creating different user accounts in the two domains.
DNS provides a name resolution service for the domain controller location. DNS also provides a domain hierarchical design that Active Directory uses to provide a naming convention for the data structure. DNS responds to your request for a resource by providing the IP address of the server where the requested resource is stored. Active Directory uses DNS to implement an IP-based naming system that helps you to locate the Active Directory services and domain controllers over the standard IP on the Internet and the intranet.
Working with Domain Trust
A trust represents a logical relationship between the domains, which allows the members in one domain to be authenticated by a domain controller in another domain. Windows Server 2003 Active Directory provides various security features to manage the forests and trust relationships.
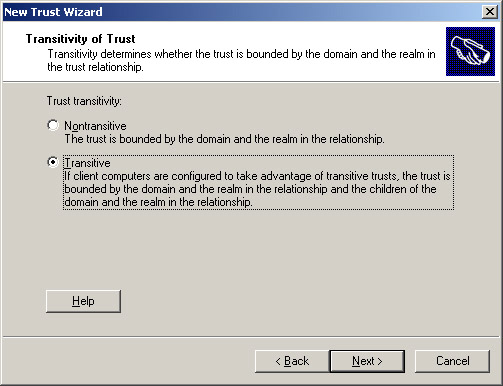
A trust relationship can be either transitive or non-transitive. If a trust relationship exists between a domain and all the other domains that trust that domain, the relationship is called transitive. If a trust relationship exists only between two domains, the relationship is non-transitive. The transitivity of a trust relationship determines whether or not a trust relationship between two domains can be extended outside the two domains.
Active Directory supports two trust relationship models:
-
Two-way trust between two domains, in which both the domains trust each other.
-
One-way trust between two domains, in which only one of the two domains trusts the other domain.
In Windows Server 2003, all trust relationships are of the two-way transitive type. This means that if domain A establishes a trust relationship with domain B, and domain B establishes a trust relationship with domain C, there exists a trust relationship between domain A and domain C.
Active Directory automatically creates two default trust relationships when you add a new domain during the installation of Active Directory. In addition to creating default trust relationships, you can create four other types of trust relationships:
-
Forest trust: Supports the sharing of resources between the forests.
-
External trust: Accesses the resources on a domain that is located in a separate forest and not connected to the trusting domain through a forest trust.
-
Realm trust: Provides a trust relationship between a non-Windows Kerberos environment, such as a UNIX environment, and a Windows Server 2003 domain.
-
Shortcut trust: Provides a trust relationship between two domains in the same forest.
A forest trust manages the security relationship between two forests and forms a trust relationship between every domain in the two forests. The features of a forest trust are:
-
Enabling all the domains in a forest to establish a trust relationship with the domains in another forest through a single trust link between the two forests.
-
Establishing a non-transitive trust relationship between three or more forests. For example, in a non-transitive trust relationship, if forest X trusts forest Y and forest Y trusts forest Z, the forest trust does not establish a trust relationship between forest X and forest Z.
-
Establishing either a one-way or two-way forest trust.
The conditions to create a trust relationship differ for all types of trusts. For example, you create a realm trust to establish cross-platform interoperability with the security features based on the Kerberos V5 version, such as UNIX. To create a realm trust between two domains:
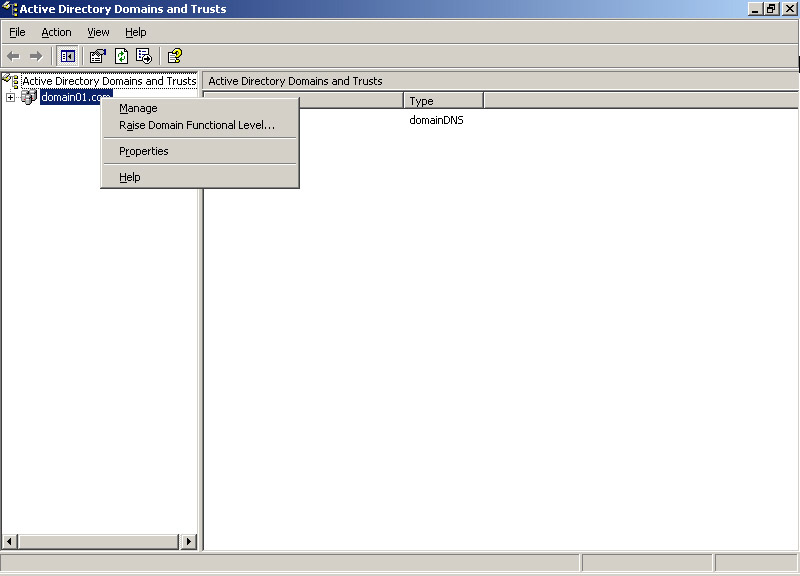
-
Select Settings->Control Panel->Administrative Tools->Active Directory Domains and Trusts. The Active Directory Domains and Trusts window appears, as shown in Figure 14-3-9:
Figure 14-3-9: The Active Directory Domains and Trusts Window
-
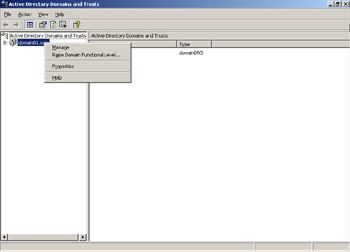
Right-click the domain01.com node to create a trust relationship. A shortcut menu appears, as shown in Figure 14-3-10:
-
Select the Properties option from the shortcut menu. The domain01.com Properties window appears, as shown in Figure 14-3-11:
-
Click the Trusts tab in the domain01.com Properties window and click the New Trust button to start the New Trust Wizard, as shown in Figure 14-3-12:
-
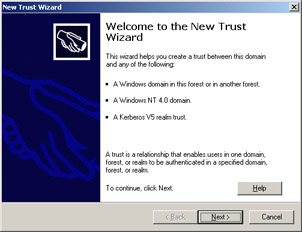
Click Next on the Welcome screen of the New Trust Wizard to open the Trust Name screen, as shown in Figure 14-3-13:
-
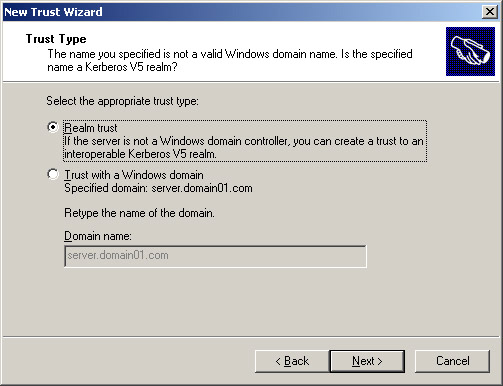
Type the DNS name, server.domain01.com, as the target realm, in the Name text box and click Next. The Trust Type screen appears, as shown in Figure 14-3-14:
-
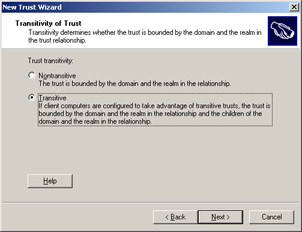
Select the Realm trust option from the Trust Type screen and click Next. The Transitivity of Trust screen appears, as shown in Figure 14-3-15:
-
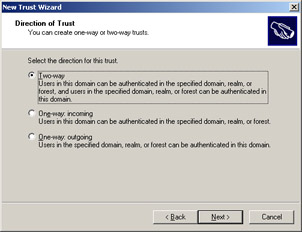
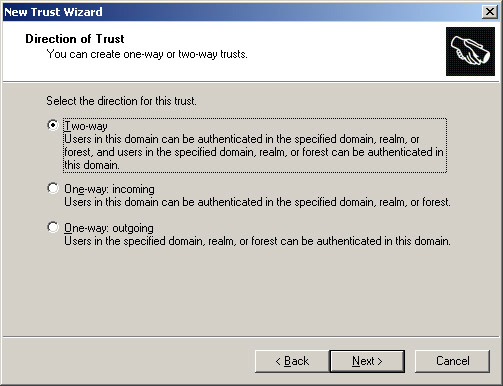
Select the Transitive option to create a trust relationship between the domain01.com and server.domain01.com domains. Click Next to open the Direction of Trust screen, as shown in Figure 14-3-16:
-
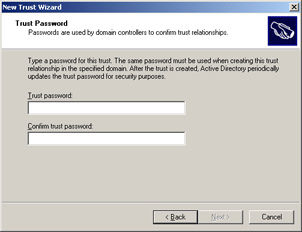
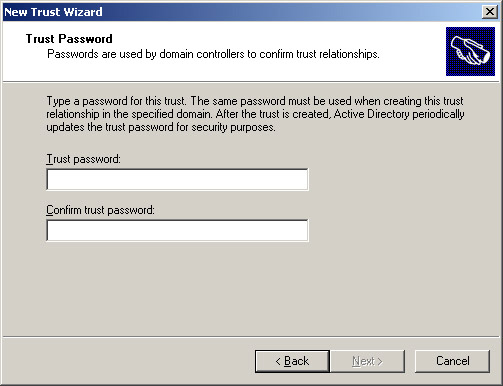
Select the Two-way option in the Direction of Trust screen to establish a two-way realm trust. Click Next to open the Trust Password screen, as shown in Figure 14-3-17:
-
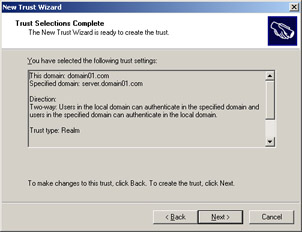
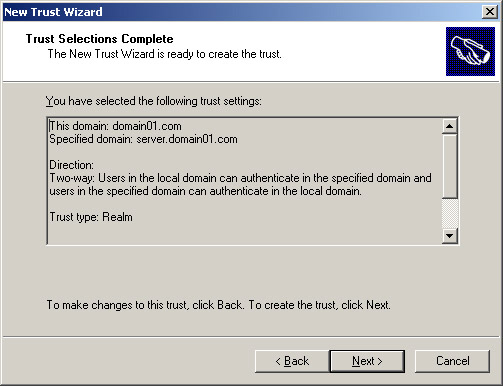
Type a password in the Trust password text box and click Next. The Trust Selections Complete screen appears, as shown in Figure 14-3-18:
-
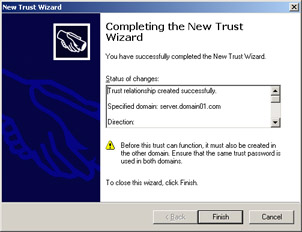
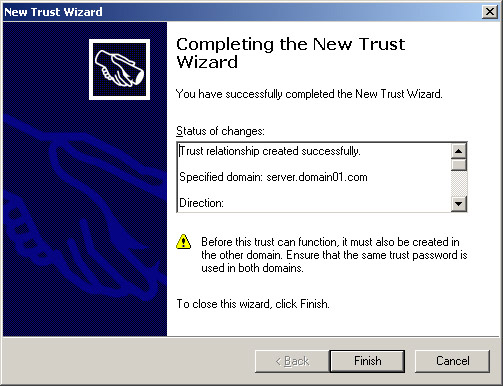
Click Next to open the Completing the New Trust Wizard screen, as shown in Figure 14-3-19:
-
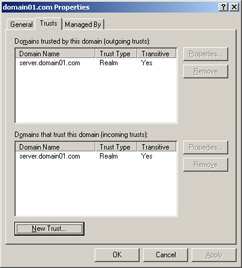
Click Finish to close the New Trust Wizard and open the domain01.com Properties window, which contains the new trust relationship, as shown in Figure 14-3-20:
Figure 14-3-20: The domain01.com Properties Window With a New Relationship
A non-transitive trust relationship can be either one-way or two-way. To create a one-way non-transitive trust relationship with the domains outside a forest, you should establish an external trust relationship. When an external trust relationship exists between two domains, the security principals in the external domain allow its members to access the resources available within the other domain.
For each security principal of an external domain, Active Directory creates a foreign security principal object in the internal domain. Consequently, a foreign security principal exists in a trusted domain in a different forest. Foreign security principals can become the members of an internal domain.
You can create a non-transitive trust relationship only between the following domains:
-
A Windows Server 2003 domain and a Windows Server NT domain.
-
A Windows Server 2003 domain in one forest and a domain in another forest.
Understanding DNS Support for Active Directory
DNS is an Internet service that translates a domain name into its IP address, and vice-versa. When a client uses a DNS name, the DNS server translates the DNS name to its corresponding IP address. For example, a client queries a DNS server for the IP address of a computer with the domain name, domain1.com. The DNS server returns a record that contains the IP address corresponding to the specified DNS domain name.
DNS is based on a hierarchical and logical tree structure of domains, called domain namespace. DNS divides a domain namespace into zones, which store information about one or more domains. A zone contains the zone database file, which contains the domain names and their corresponding IP addresses in the form of records, called resource records. A record in a zone file consists of specific information about a domain or a service in a DNS domain.
Windows Server 2003 supports the following DNS features:
-
Conditional forwarder: Forwards the DNS queries to a DNS server depending on the DNS domain name. For example, you can configure a DNS server to forward the queries, which the server is unable to answer, to the IP address of another DNS server.
-
Stub zone: Represents a copy of a zone, which contains the resource records for identifying the authoritative DNS servers for the particular zone. When a DNS client performs a query operation on a DNS server that hosts a stub zone, the DNS server uses the resource records in the stub zone to resolve the query.
-
Active Directory integrated zone: Stores the DNS resource records in Active Directory. Any domain controller that runs the DNS server can update the resource records.
-
Enhanced DNS security feature: Provides security for the DNS server service, the DNS client service, and the DNS data.
-
Enhanced debug logging: Uses the enhanced DNS server service debug logging settings to troubleshoot DNS problems.
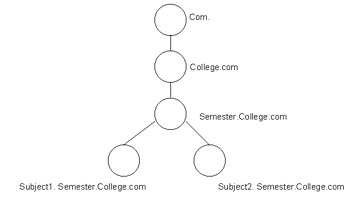
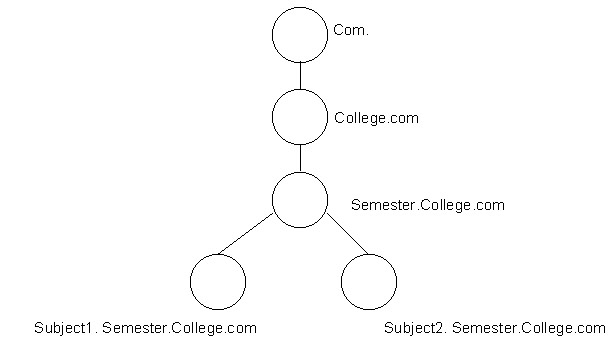
DNS domain namespace is a hierarchy of domains, in which the top level of the hierarchy is called the domain root. In a domain namespace, the domain root is represented by a period (.), which indicates that the domain is located at the highest level of the domain hierarchy. The domain namespace names that you represent by using this method are called Fully Qualified Domain Names (FQDNs).
DNS domain namespace describes a relationship between the hosts. For example, if a host called semester is located in the College.com domain, its FQDN is semester.college.com. You can arrange the domains in a hierarchy based on a contiguous namespace. For example, the semester.college.com domain represents a child domain of the college.com domain.
Figure 14-3-21 shows the DNS hierarchy of the College.com domain:
DNS interprets an FQDN to identify the DNS domain name in a manner similar to that of the file locations at a command prompt. For example, the client.sample.microsoft.com. domain namespace can be specified according to FQDN, and consists of four domain levels. The various domain levels in the FQDN are:
-
sample: Corresponds to the subdomain where the computer named client is registered for use.
-
microsoft: Corresponds to the parent domain of the sample domain.
-
com: Corresponds to the top-level domain that commercial organizations use, and represents the parent domain of the microsoft domain.
-
Period: Represents a standard separator character.
When a DNS client searches for a domain name, the client queries the DNS server to resolve the domain name. When a DNS server receives a query for a resource record, the server executes the query depending on whether or not the server contains a copy of the zone file that contains the resource record. A query message that a DNS client sends to a server consists of three parts:
-
A DNS domain name specified by FQDN.
-
A specific query type, which is either a resource record or a specific type of query operation.
-
A class for the DNS domain name.
The client service that queries the DNS server and handles the responses is called a resolver. When a resolver receives a query response, it stores the query results in the memory. The DNS resolver is a part of the Transmission Control Protocol/Internet Protocol (TCP/IP) driver.
For a specific zone, the DNS server is either authoritative or non-authoritative. A DNS server that contains a copy of a zone file with the specified resource record is called the authoritative DNS server for that zone. A DNS server that does not contain a copy of the zone file is called the non-authoritative DNS server for that zone.
An authoritative DNS server performs the following functions for a resource record lookup:
-
If the DNS server finds a copy of the specified resource record in its zone file, the server returns a copy of the contents in the form of a resource record.
-
If the DNS server has performed a recent lookup on the specified resource record, the server returns a cached copy of the resource record.
-
If the DNS server does not find the specified resource record, the server returns the message string, Record Not Found, to the DNS client.
For example, suppose the client in the college.com domain sends a query to its authoritative DNS server to connect to the DNS server, ser, and retrieve a resource record. The authoritative DNS server handles the query in the following sequence:
-
The Tcpip.sys file creates an Internet Control Message Protocol (ICMP) packet by using the IP address of the ser server. The Tcpip.sys file uses the internal DNS resolver to retrieve the IP address of the ser server.
-
The DNS resolver queries the associated DNS server. The query consists of the following elements:
-
The FQDN of the target computer, represented as ser.college.com.
-
The type of requested resource record. This means that the client requests the DNS server for a domain name.
-
The class of the resource record, which is either the IN class or the Internet class.
-
-
When the authoritative DNS server receives the query, the server parses the host name to find the college.com domain.
-
The authoritative DNS server finds the resource record for the ser server, and returns the contents of the resource record to the DNS client in the form of a query response.
-
The resolver obtains the IP address of the ser.college.com server. The Tcpip.sys file creates an IP packet by using the IP address from the resource record.
-
The Tcpip.sys file provides the IP packet to the Network Driver Interface Specification (NDIS) driver, which specifies a medium to transmit the IP packet to the target server.
A non-authoritative DNS server handles the queries in three ways:
-
The DNS server queries the other DNS servers until it finds the resource record. The DNS server then returns a copy of the resource record to the client.
-
The DNS server provides a reference to a server that contains a copy of the resource record and is located at a higher level in the DNS hierarchy.
-
The DNS server provides a cached copy of the resource record based on a previous lookup.
To access the location, www.books.org, on an external network, such as the Internet, the client queries a non-authoritative DNS server. The non-authoritative server handles the query in the following sequence:
-
The DNS resolver queries the DNS server for retrieving a record for the www.books.org location.
-
The DNS server in the college.com domain does not contain a zone file for the www.books.org location. As a result, the DNS server forwards the request to another DNS server.
-
The DNS server queries the Top-Level Domain (TLD) root server to retrieve the record for www.books.org. The TLD server is authoritative for the .org domain. This means that the TLD server contains the Name Server (NS) records that represent the servers containing the zone file for the .org domain.
-
The TLD server uses the NS records and identifies the servers for www.books.org. The TLD server then returns the NS and the resource record for each identified server.
-
The college.com DNS server queries the identified server to retrieve the resource record for www.books.org.
-
When the college.com DNS server receives the record for www.books.org, the server sends the required record as a query response to the client. The DNS server stores a copy of the query response for a similar client request.