Making Rules Available at System Startup
Assume that you need the following rule activated each time the Linux server starts:
# ipchains -A input -s 172.17.68.224 -d
172.17.69.36 21 -p tcp -j DENY -l
You can save the rules in a file. When the Linux server starts, the rules are restored from the file. For example, you can save rules in a file, ipchainrules.conf, by using the following command:
# ipchains-save > /root/ipchainrules.conf
The contents of the file are displayed below:
:input ACCEPT
:forward ACCEPT
:output ACCEPT
-A input -s 172.17.68.224/255.255.255.255 -d
172.17.69.36/255.255.255.255 21:21 -p 6 -j DENY -l
When the system boots, you need the rules to be automatically loaded. To automatically load the rules, create a shell script called /root/startipchains containing the following commands:
#!/bin/bash
ipchains –F
ipchains-restore < /root/ipchainsrules.conf
echo 1 > /proc/sys/net/ipv4/ip_forward
The script clears all the existing rules. It then restores all the rules that are stored in the /root/ipchainsrules.conf file. It also enables IP forwarding using the echo command.
You can then use the following command to create a link to the file:
# ln -s /root/startipchains /etc/rc.d/rc5.d/S09startipchains
The rules are loaded when the Linux server starts in the run level 5. To activate the rules when the Linux server starts in the run level 3, you use the following command:
# ln -s /root/startipchains /etc/rc.d/rc3.d/S09startipchains
Alternatively, you can add the following line at the end of the /etc/rc.d/rc.local file:
#!/bin/sh
#
# This script will be executed *after* all the other init scripts.
# You can put your own initialization stuff in here if you don't
# want to do the full Sys V style init stuff...
..
..
# Other details not shown
..
..
/root/startipchains
After the Linux server starts, if you execute the ipchains -L command to view the existing rules, you obtain the following output:
# ipchains –L
Chain input (policy ACCEPT):
target prot opt source
destination ports
DENY tcp --l- 172.17.68.224
172.17.69.36 any -> ftp
Chain forward (policy ACCEPT):
Chain output (policy ACCEPT):
Using the symbolic link method to load ipchains during system startup should be preferred over editing the rc.local file. This ensures that the firewall rules are in place prior to starting any of the network services.
Log Format Used by ipchains
You can use the following command to block FTP packets:
# ipchains -A input -s 0.0.0.0/0 -d
172.17.69.36 21 -p tcp -j DENY -l
In the above command, the IP address of the Linux server is 172.17.69.36. Therefore, the command disables port 21 used by FTP from any source. In addition, the -l option logs the packets into the file /var/log/messages.
You can use the ipchains -L option to view the rule. The output of the ipchains -L command is:
# ipchains –L
Chain input (policy ACCEPT):
target prot opt source
destination ports
DENY tcp --l- anywhere
172.17.69.36 any -> ftp
Chain forward (policy ACCEPT):
Chain output (policy ACCEPT):
You can execute the following command to view the contents of the /var/log/messages file:
# tail -f /var/log/messages
If you try to connect to a Linux server from another computer by using an FTP client, such as WS-FTP, ipchains denies the request. In addition, a log is generated and stored in the /var/log/messages file. A sample output in the /var/log/messages file is displayed below:
Apr 26 08:56:19 localhost kernel: Packet log: input
DENY eth0 PROTO=6 172.17.68.224:2324
172.17.69.36:21 L=48 S=0x00 I=24194 F=0x4000 T=128
SYN (#1)
Table 3-1-3 explains various parts of the generated log.
| Log file output | Description |
|---|---|
| Apr 26 | Date when the message was logged in /var/log/messages file. |
| 08:56:19 | Time when the message was logged. |
| Localhost | Host name that reported the message. |
| kernel: Packet log: | Packet logged by the kernel. |
| Input | Name of the chain that caused the packet to be logged. |
| DENY | Action taken by ipchains. In this case, the packet is dropped without any notification being sent to the computer that sent the packet. |
| eth0 | Interface used by a packet. |
| PROTO=6 | Protocol of the packet. The number 6 specifies the TCP packet. |
| 172.17.68.224:2324 | IP address of the source computer, along with the port number. |
| 172.17.69.36:21 | IP address of the destination computer, along with the port number. |
| L=48 | Length of a packet in bytes. |
| S=0x00 | Type of Service (TOS). |
| I=24194 | IP-ID present in the IP packet. |
| F=0x4000 | Flags (3 bits) and fragment offset (13 bits) present in the packet. |
| T=128 | Time To Live (TTL) value of the packet. The TTL value specifies the number of hosts a packet can go through before timing out. |
| (#1) | The rule number that caused the packet to be logged. |
Future of ipchains: netfilter/iptables
In Linux, kernel 2.4.x netfilter/iptables is used for packet filtering. The ipchains package used for kernel 2.2.x has been redesigned and improved to create netfilter/iptables.
Table 3-1-4 displays some of the differences between ipchains and iptables.
| Features of iptables | Features of ipchains |
|---|---|
| Packets coming into the server go through the INPUT chain, and packets going out of the server go through the OUTPUT chain. | Packets that are forwarded have to go through both the INPUT and OUTPUT chains. |
| Use the DROP option to restrict packets. | Use the DENY option to restrict packets. |
Checking Rules Specified with ipchains
You can check the rules that have been enabled by using the ipchains command. For example, when the following command is used to deny FTP access to a computer:
# ipchains -A input -s 172.17.68.224 -d
172.17.69.36 :21 -p tcp -j DENY -l
The rules present on the Linux server are:
# ipchains –L
Chain input (policy ACCEPT):
target prot opt source
destination ports
DENY tcp --l- 172.17.68.224
172.17.69.36 any -> 0:ftp
Chain forward (policy ACCEPT):
Chain output (policy ACCEPT):
You use the -C option along with the ipchains command to check if the source host 172.17.68.224 can connect using FTP. When you execute the following command, the message denied is displayed on the screen. This indicates that the packets from the host 172.17.68.224 port 2223 to 172.17.69.36 port 21 are not granted access:
# ipchains -C input -p tcp -s 172.17.68.224 2223 -d
172.17.69.36 21 -i eth0
denied
To check for another host, for example, 172.17.68.223 with port 2223, you use the following command:
# ipchains -C input -p tcp -s 172.17.68.223 2223 -d
172.17.69.36 21 -i eth0
accepted
The message accepted indicates that the packets from 172.17.68.223 port 2223 will be accepted by 172.17.69.36 at port 21.
You can also use the -v option to obtain more details about the command:
# ipchains -C input -p tcp -s 172.17.68.223 2223 -d
172.17.69.36 21 -i eth0 -v –b
- tcp opt --- tos 0xFF 0x00 via eth0
172.17.68.223 -> 172.17.69.36 2223 -> 21
accepted
- tcp opt --- tos 0xFF 0x00 via eth0
172.17.69.36 -> 172.17.68.223 21 -> 2223
accepted
In the above command, the -b option checks the transfer of packets in both directions.
Tips on Setting Rules
While setting rules, you must always set DENY for all the packets for the input, forward, and output chains. This needs to be done so that no packet passes through the firewall while the rules are being set. After the rules are set, you can remove the deny rule for the input, forward, and output chains. For example, you can use the following script, called changerules, to set ipchains rules:
echo "Deny packets for all the chains"
ipchains -I input 1 -j DENY
ipchains -I output 1 -j DENY
ipchains -I forward 1 -j DENY
echo "All the packets are now blocked so changes can be made now"
echo "Current rules are: "
ipchains –L
Set rules here
# For example, Assuming the ip address of server is 172.17.69.36
# The telnet service on port 23 is blocked
ipchains -A input -s 0/0 -d 172.17.69.36 23 -p tcp -j DENY
echo "Removing restriction on the packets"
ipchains -D input 1
ipchains -D output 1
ipchains -D forward 1
# Removing rule number 1 from input, output and forward chain
echo "The effective rules are: "
ipchains -L
In the above script, all the packets are denied access. New rules are then set. After that, a rule to block the Telnet access on the server with the IP address 172.17.69.36 is added. After the new rule is added, the restrictions on the packets are removed and the rules that were created in the beginning of the script are deleted. You can execute the changerules shell script shown above as follows:
# sh changerules
The output of the above shell script is as follows:
Deny packets for all the chains
All the packets are now blocked so changes can be made now.
Chain input (policy ACCEPT):
target prot opt source
destination ports
DENY all --- anywhere
anywhere n/a
Chain forward (policy ACCEPT):
target prot opt source
destination ports
DENY all --- anywhere
anywhere n/a
Chain output (policy ACCEPT):
target prot opt source
destination ports
DENY all --- anywhere
anywhere n/a
Removing restriction on the packets
The effective rules are:
Chain input (policy ACCEPT):
target prot opt source
destination ports
DENY tcp --- anywhere
172.17.69.36 any -> telnet
Chain forward (policy ACCEPT):
Chain output (policy ACCEPT):
IP Masquerading Using ipchains
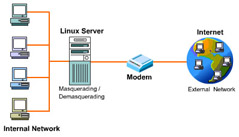
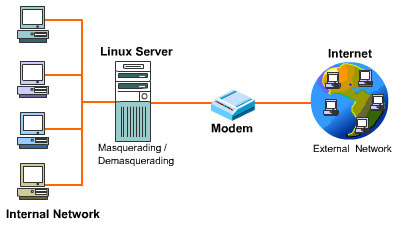
You can use masquerading to connect a computer in a network to an external network, such as the Internet.
In the Figure 3-1-4, multiple computers are interconnected in the internal network. Only the Linux server that is connected to a modem can dial up to the Internet. After a connection is made, the interface ppp0 is used to transmit data to the Internet. You can enable IP Masquerading on the Linux server so that all the packets that are sent by the computer in the internal network to the external network appear to be sent from the Linux server. The computers in the internal network can be running under any operating system, such as Windows 95/98/NT or Linux. The computers in the internal network should have their default gateway set to the address of the Linux server that provides access to the external network. When the external network sends a reply, the Linux server demasquerades the packets and sends them to the computers in the internal network. You can use the following three commands to enable IP masquerading:
# ipchains -P forward DENY
# ipchains -A forward -i ppp0 -j MASQ
# echo 1 > /proc/sys/net/ipv4/ip_forward
When the Linux server receives a packet from the internal network, destined for the external network, it rewrites the header information. After the Linux server rewrites the header, to the external network all packets will appear to originate from the Linux server. When the external network sends a reply to the Linux server, it again writes the header information and sends these replies to the computers in the internal network. Internal network hosts are unaware that the header information was changed using IP masquerading.
Securing a Linux Server
A computer is never considered absolutely secure or absolutely insecure. You can enhance the security of a server by using various tools. Which ones you use depends on how valuable the data you want to secure is. If it’s valuable, you need to increase security by using additional software. You need to calculate the cost of beefing up security as well as the cost of losing the data you are trying to secure. In addition, the use of certain software can make it more difficult for a hacker to break into the system.
You can use the ipchains package as a firewall to increase security in a network. In addition to applying ipchains rules, you should check for extra services that are running on your Linux server. If there are services that you do not need, you should disable them. You can use the following netstat command to check the services that are running on your computer:
# netstat -a -p
You should also regularly check the log files to check for any security attacks. You can use software, such as Tripwire (www.tripwire.com), to check if any file has changed. You can also use auditing software, such as Security Administrator's Integrated Network Tool (SAINT) to check for vulnerabilities in your computer. SAINT is a software program that is available on the Internet. You can download it from www.saintcorporation.com. You must also keep constant watch on security advisories that are posted on various security sites. Useful security sites include the CERT Coordinating center (www.cert.org), SecurityFocus (www.securityfocus.com), and Red Hat's Errata page (www.redhat.com/corp/support/errata/index.html).
This is important as new vulnerabilities are detected daily. You may have secured your computer today. However, with new vulnerabilities discovered everyday, it may not remain secure in the future. You should log packets that violate firewall rules because these can help you detect intrusion attempts.
Depending on your requirements, you can secure various services. Some of the services and port numbers that you should secure are listed in Table 3-1-5.
| Name of the Service | Port Number | Description |
|---|---|---|
| Echo | 7 | This service is used to echo packets back to the sender. Because it can be misused to perform denial of service attacks, it should be disabled when not in use. To increase security, you should block packets that are sent to port number 7. |
| FTP | 21 | This service is used to transfer files. You should restrict hosts that can connect to your FTP server to download files. |
| DNS | 53 | DNS is used to resolve host names with IP addresses. You should restrict access to valid secondary name servers only. This is essential since malicious users may try to steal information stored in the DNS server. |
| finger | 79 | The finger service is used to share information about users. It should be restricted to computers that have a valid IP address. |
| HTTP | 80 | The HTTP service is used to serve pages to Web sites. You can block those computers from viewing Web sites present on the Web server. |
| POP-3 | 110 | This service is used to retrieve mail messages. You can use ipchains so that only computers with valid IP addresses can retrieve mail messages. |
| IMAP | 143 and 220 | The IMAP service is used to view e-mail messages on the server. Like the POP3 service, only valid hosts should be allowed to access IMAP. |
| rexec | 512 | This service is used to execute commands on a remote computer. It is not considered secure and should be disabled. |
| rlogin | 513 | The rlogin service is used to start a session on a remote computer on the network. It is insecure and should be blocked. |
| NFS | 2049 | NFS (Network File Systems) is used to share files between multiple computers. Since it is not considered a secure protocol, if the files on a network are not being shared, this service should be disabled. If you are using this service, you should restrict its use to valid IP addresses only. |
| X-Windows | 6000-6063 | This protocol is used to run graphical applications. It can also be used to run graphical applications over the network. It uses unencrypted communication between computers. This service should be allowed only for computers with valid IP addresses. |
To block any of these services, you can use the following syntax of the ipchains command:
# ipchains -A [Name of the rule] \
-s [IP address of the source computer] \
-d [IP address of the destination computer] \
[port number] -p [protocol] -I [Interface Name] \
-j DENY -l
Table 3-1-6 explains the various options used along with the ipchains command:
| Option | Description |
|---|---|
| -A [Name of the rule] | Specifies the name of the rule. It can be input or output. |
| -s [IP address of the source computer] | Specifies the source IP address. It should be the address from where the packet has been sent. |
| -d [IP address of the destination computer] | Specifies the destination IP address. It should be the address to which the packet has been sent. |
| [port number] | Specifies the port number that is to be blocked. |
| -p [protocol] | Specifies either TCP or UDP, depending on the type of protocol used by the service. |
| -I [Interface Name] | Specifies the name of the device from where packets are being transmitted or received. For example, its value can be eth0 if the first network adapter is being used to transmit the packets. |
| -j DENY | Specifies that the packets needs to be blocked. |
| -l | Specifies that the packet should be logged so that an analysis can be done on the log files. |
For example, to block HTTP access to a computer with the IP address 172.17.69.36 from a computer with the IP address 172.17.68.224, you can use the following command:
# ipchains -A input -s 172.17.68.224 -d
172.17.69.36 110 -p tcp -i eth0 -j DENY -l
You can refer to the ipchains man pages on the Internet for the syntax of ipchains command.
You can get more information about firewalls from the following documents:
IPCHAINS-HOWTO
Firewall-HOWTO
IP-Masquerade-HOWTO