To protect data, various security resources need to be applied to a network. One of the key resources used to protect a network is a firewall. Just as people secure their homes by building boundary walls around them, firewalls serve as barriers between a local network and an external network. The Linux kernel version 2.2 has built-in firewalling capabilities, which can be configured using the ipchains package. Both the Linux kernel and the ipchains package are open source software products, which can be downloaded free of charge.
A firewall must be properly configured to be effective. This ReferencePoint explains the importance of a firewall in a network, lists the various types of firewalls, and explains how to use ipchains as a packet filtering firewall. It also addresses the steps that you must take to secure a network.
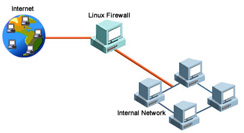
depicts an internal network connected to the Internet using a Linux firewall.
The Firewall System
A firewall is used to implement a security policy. Security policies should be clearly defined before implementing a firewall. The absence of a security policy will hamper a firewall’s ability to secure the network.
When a computer is connected to the Internet as well as to a local network, it has two interfaces. The interface that connects the computer with the Internet is known as the external interface. The interface that connects the local network with the computer is known as the local interface.
An Internet Service Provider (ISP) supplies the IP address of the external interface connected to the Internet. The IP address of the internal network is set to one of the following three private network address ranges:
10.0.0.0 - 10.255.255.255
172.16.0.0 - 172.31.255.255
192.168.0.0 - 192.168.255.255
When a computer connected to the Internet shares bandwidth with computers that are not directly connected to the Internet, hackers may be able to access your network. To prevent that from happening, you need a firewall.
Setting up a firewall involves defining rules that need to be implemented to ensure network security. You need to determine the appropriate number of rules. Too many rules may be difficult to maintain, and too few rules may leave some loopholes.
There are two types of firewalls:
Packet Filtering Firewalls
A packet filtering firewall works at the network level. Data is transferred in the form of packets on a network. A packet filtering firewall consists of a packet filter that allows or denies data to pass through the network, based on the information stored in each packet’s header. The header contains information about the source, destination, packet type, protocol, port number, as well as other details about the packet. The packet filter examines the header of every packet and chooses one of the following options:
-
Deny the packet: Discards the packet as if it had never received it.
-
Reject the packet: Discards the packet, but informs the source of the packet that it has discarded the packet.
| Note | There is a difference between a packet being denied and a packet being rejected. If a packet is denied, no message is sent to the computer that sent the packet. However, if the packet is rejected, the computer that sent the packet is informed that the packets sent by it have been rejected. |
Proxy Server Firewalls
A proxy server connects a local network to the outside network. Some proxy servers can act as a firewall, for example Microsoft Proxy 2.0 or the company's more recent Internet Security and Acceleration (ISA) proxy server. Proxy servers act as firewalls when you specify which packets can or cannot be sent outside the local network. There are two types of proxy server firewalls: application proxies and SOCKS proxies
Application Proxies
An application proxy is also known as an application gateway, or an application-level proxy. In an application proxy, a client computer connects to a proxy server. The proxy server authenticates the client computer, and if access is granted, the server fetches the required data from the external network and delivers it to the proxy server. In addition, the proxy server establishes a connection with the destination computer behind the firewall. The proxy also acts on behalf of the client computer, hiding and protecting individual computers on the network behind the firewall. The application proxy can also cache the retrieved data.
SOCKS Proxies
SOCKS proxies use a computer called the SOCKS server. The SOCKS server acts like a switchboard, enabling a computer within the local network to connect to a computer on the external network.
An Introduction to ipchains
The ipchains package is used to implement firewalls in computers running Linux kernel 2.2. Red Hat Linux 6.x uses ipchains as packet-filtering firewalls.
The ipchains program is written by Paul "Rusty'' Russell. It is based on the ipfwadm software, which was created by Jos Vos jos@xos.nl.
The ipchains software is released under General Public License (GNU). Its source code, along with the executable software, is available with most distributions of Linux and is free of charge.
Installing ipchains
You can download ipchains software from http://netfilter.samba.org/ipchains in the form of either a tar.gz file or an RPM file.
Installing from a Tar Archive
-
To install ipchains from a tar archive, unzip the file ipchains-1.3.10.tar.gz using the following command:
# tar -zxvf ipchains-1.3.10.tar.gz
-
Change the current directory to the directory ipchains-1.3.10 using the cd command:
# cd ipchains-1.3.10
-
Next, compile the program using the make all command.
-
To install the program, type make install at the command prompt.
Installing from RPM
To install ipchains using the RPM package, you must first download it from ftp://ftp.redhat.com or http://rpmfind.net. The rpm package is also available on Red Hat Linux 6.x CDROM.To install ipchains using rpm, execute the following command:
# rpm -ivh ipchains
ipchains ##################################################
To check if ipchains is already installed, execute the following command:
# rpm -q ipchains
How ipchains Works
To understand how ipchains works, it's useful to compare it to a water filter. In a water filter, water is passed through filters. The water filter stops impurities in the water from passing through pure water passes through and suspended particles are filtered out. Similarly, when network packets pass through ipchains, only packets that fulfill the requirements stated by the firewall rules are allowed to pass through. The remaining packets are discarded.
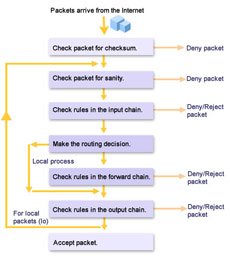
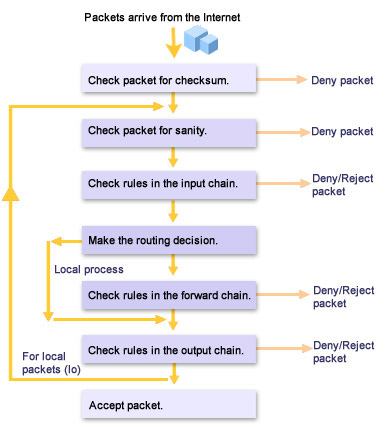
Three chains are defined in the Linux kernel: input, output, and forward. These chains are collections of rules. A packet must meet the requirements mandated by the rules before it is accepted by the system. Each packet contains header information that includes the source address, the destination address, and other information required to transmit the packet. The rule specifies certain restrictions. For example, a rule might specify that the source address for the packets received by a computer should not be 192.168.0.10. If the source address is 192.168.0.10, the packet is denied or rejected; otherwise, it is accepted. Figure 3-1-2 displays the process of packets passing through ipchains.
When a packet arrives from an external network, its checksum is verified to ensure that the packet was received without any errors. Next, a sanity check is performed to ensure that the packet contains valid data. It is then passed to the input chain. If the packet satisfies all the conditions in the input chain, the kernel decides whether to send the packet to the output chain or the forward chain. This decision is based on the packet’s destination.
If the packet is intended for another computer on the network, it is passed to the forward chain. It is passed on to the output chain if the packet satisfies the rules present in the forward chain. If the packet fulfills all the rules in the output chain, it is accepted. Otherwise, the packet is denied or rejected.
If the packet is intended for the computer on which it was received, it is passed to the output chain without being sent to the forward chain. The interface type of these packets is set to the loopback (lo) interface, and a check is made to ensure that the packet satisfies all the rules of ipchains.
Implementing Firewalls Using ipchains
You can use ipchains only if the kernel on the Linux server supports packet filtering. You can determine whether the kernel supports packet filtering by verifying the presence of the file /proc/net/ip_fwchains. If the file exists, the kernel supports packet filtering. If the file does not exist, you need to recompile the kernel.
Before compiling 2.1 or 2.2 series kernels, set the following options:
CONFIG_FIREWALL=y CONFIG_IP_FIREWALL=yFor the steps involved in compiling a kernel, refer to the Kernel-HOWTO document available at the site http://www.tldp.org.
Red Hat Linux 6.x uses the kernel 2.2, which supports packet filtering. Since the appropriate kernel options are already set, there is no need to recompile the kernel present in Red Hat Linux 6.x.
You use ipchains to specify which packets you want filtered. The ipchains program inserts rules into and deletes rules from the packet filtering section of the kernel. These changes are not permanently recorded and are lost when the system restarts. However, you can create a shell script to make these changes permanent.
The kernel starts with three lists of rules . These lists are known as chains or firewall chains. For example, if a packet comes in through the Ethernet interface, the kernel uses the input chain. If this step is successfully completed, the kernel decides where to next send the packet. This is called routing. If it is to be sent to another computer, the kernel consults the forward chain. Finally, just before sending the packet, the kernel consults the output chain. If there is no rule that stops the packet after passing through the various chains, it is accepted.
A chain is a checklist of rules that indicates how a packet is handled. If a rule does not match the packet, the next rule in the chain is consulted. Finally, if there are no more rules to check, the kernel looks at the chain policy to determine what to do with the packet. In a security-conscious environment, this policy usually specifies whether to reject or deny the packet. All chains are assigned a name. You need to use these names while modifying the rules in these chains. The three built-in chains - input, output, and forward, cannot be deleted. You can also create chains with user-defined names. Rules can then be added to or deleted from these chains.
You can create or maintain your own chains by using various options. Table 3-1-1 lists the options that can be used with the ipchains command.
| Option | Usage |
|---|---|
| -N | Creates a new chain |
| -X | Deletes an empty chain |
| -P | Changes the policy for a built-in chain |
| -L | |
| -F | |
| -Z | Zeroes the packet and byte counters on all the rules in a chain |
| -A | Appends a new rule to a chain |
| -I | Inserts a new rule at a specific/specified position in a chain |
| -R | Replaces a rule at a specific/specified position in a chain |
| -D | Deletes a rule at a specific/specified position in a chain |
Listing Rules
The -L option is used to list all the rules in a particular chain. If no arguments are specified, the ipchains -L command displays all the defined chains:
# ipchains –L
Chain input (policy ACCEPT):
Chain forward (policy ACCEPT):
Chain output (policy ACCEPT):
The default policy for the input, forward, and output chains is set to accept all packets. This means that there are no restrictions set on network packets. All packets arriving on the network are accepted and all packets going out of the network are sent or forwarded without restrictions.
Appending Rules
You can use the -A option to append rules. For example, you can use the following command to stop Internet Control Message Protocol (ICMP) packets from reaching your computer from a specific computer:
# ipchains -A input -s 172.17.144.231 -p icmp -j DENY
# ipchains –L
Chain input (policy ACCEPT):
target prot opt source
destination ports
DENY icmp --- 172.17.144.231
anywhere any ->
any
Chain forward (policy DENY):
Chain output (policy ACCEPT):
In the above command:
-
A input specifies that the rule is being appended to the input chain. 172.17.144.231 specifies that the rule applies to a packet whose source address is 172.17.144.231.
-
p icmp specifies that the rule is applicable to packets with the ICMP protocol.
-
j DENY specifies that packets matching the given criteria should not be allowed access to the computer.
As per the command, the computer with the IP address 172.17.144.231 will not be able to ping the computer on which this rule is specified because the ping utility uses the Internet Control Message Protocol (ICMP).
Deleting Rules
To delete a rule, you use the -D option with the ipchains command. You can specify either the rule number or the exact rule that you want to delete:
# ipchains -D input 1
# ipchains -D input -s 172.17.144.231 -p icmp -j DENY
In the above example, the first form of the -D option deletes the first rule.
The second form is identical to the -A option except that instead of appending the rule, it deletes a rule by using the -D option.
Denying TCP Services
You can add a rule using ipchains to block all TCP packets from reaching your computer. You can set this rule for the entire network or for a specific computer on the network. To deny access to any TCP services from a computer with the IP address 172.17.144.231, use the following command:
# ipchains -A input -s 172.17.144.231 -p tcp -j DENY
In the above example, the computer with the IP address 172.17.144.231 is not allowed to use the Telnet command to connect to your computer. This is because Telnet uses the TCP protocol. Other commands that use the TCP protocol to communicate over the network will also not work.
To disable the User Datagram Protocol (UDP) protocol, you specify udp instead of tcp in the above command.
Denying All Services
To set the input chain to DENY for all computers, use the following command:
# ipchains -P input DENY
This command denies access to your computer from any other computer on the network. The -P option is used to set the input policy to DENY.
To prevent specific computers from gaining access to your computer, use the -s option. The following example illustrates this:
# ipchains -A input -s 172.17.144.231 -j DENY
# ipchains –L
Chain input (policy ACCEPT):
target prot opt source
destination ports
DENY all --- 172.17.144.231
anywhere n/a
Chain forward (policy DENY):
Chain output (policy ACCEPT):
In the above example, the first command denies the computer with the IP address 172.17.144.231 access to any service on your computer. The second command, ipchains -L, verifies if the rule has been appended.
Denying Access to the Output Chain
If you deny access to the output chain, your computer cannot access other computers on the IP network.
# ipchains -P output DENY
The above command denies the local computer access to other computers on the IP network.
To deny access to a specific computer, use the following command:
# ipchains -A output -s 172.17.144.231 -j DENY
The above example appends a deny rule to the output chain. The deny rule is added only for the computer with the IP address 172.17.144.231.
| Note | When you deny access to the output chain, other computers on the network are unable to Telnet or ping your computer. This is because to Telnet or ping a computer, data needs to travel both ways. When any other computer attempts to connect to your computer, your computer is unable to send a reply to the computer. This is due to the DENY policy on the output chain. |
Using Inversion in Rules
You can use the ! (not) symbol before the -s or -d option. On using the ! symbol, the rules match those addresses that are not equal to the specified address. Consider the following example:
# ipchains -A output ! -d 172.17.69.36 -j DENY
# ipchains –L
Chain input (policy ACCEPT):
Chain forward (policy ACCEPT):
Chain output (policy ACCEPT):
target prot opt source
destination ports
DENY all --- anywhere
!172.17.69.36 n/a
In the above example, the output rule allows packets to be transmitted to the IP address 172.17.69.36 only. Any packet that has a destination address other than 172.17.69.36 is denied access.
| Note | You must specify a space before and after the ! symbol. |
Specifying the Protocol and the Port Number in ipchains
The -p option is used to specify the protocol. In addition, you can specify a port number. For example, the Simple Mail Transfer Protocol (SMTP) service uses the port number 25.
The following command denies access to any host from accessing the SMTP service on the host with the IP address 172.17.69.36:
# ipchains -A input -s 0/0 -d 172.17.69.36 25 -p tcp -j DENY
# ipchains –L
Chain input (policy ACCEPT):
target prot opt source
destination ports
DENY tcp --- anywhere
172.17.69.36 any -> smtp
Chain forward (policy ACCEPT):
Chain output (policy ACCEPT):
Note that 0/0 in the -s option specifies that the source address of the packet can be any valid IP address.
You can also specify a range of port numbers. For example, the following command blocks ports 21 to 43 on the computer with the IP address 172.17.69.36:
# ipchains -A input -s 0/0 -d 172.17.69.36 21:43 -p tcp -j DENY
In the above command, the range of port numbers is specified as 21:43. Notice that the range is specified using the colon symbol. The value 21 represents the lower limit, and the value 43 represents the upper limit of the range. If you do not specify the lower value of the range, its value is assumed to be zero. If the upper value of the range is not specified, its value is assumed to be 65,535.
For example, if you execute the following command, it takes the range as 0-21:
# ipchains -A input -s 0/0 -d 172.17.69.36 :21 -p tcp -j DENY
You can also specify the port number instead of the name of the service. The list of names that can be used instead of the port number is specified in the /etc/services file. For example, you can execute the following command to block the SMTP service:
# ipchains -A input -s 0/0 -d 172.17.69.36 smtp -p tcp -j DENY
In the above command, smtp is used instead of port number 25.
You can also specify the ! symbol before a port or a protocol. By specifying the ! symbol before a port or a protocol, you negate the specified port or protocol. For example, the following command denies non-TCP packets:
# ipchains -A input -s 0/0 -d 172.17.69.36 -p ! tcp -j DENY
Similarly, you can use the ! symbol next to a port number. For example, the following command denies all packets except SMTP packets:
# ipchains -A input -s 0/0 -d 172.17.69.36 ! smtp -p tcp -j DENY
Specifying Interfaces in ipchains
You can use the -i option to specify an interface to which a rule is to be applied. An interface is a physical device from which a packet is received or from where the packet will be sent. For example, the following command is used to deny all packets coming from interface eth0:
# ipchains -A input -s 0/0 -d 172.17.69.36 -i eth0 -j DENY
Specifying interface name in ipchains is useful when you want to assign different rules to multiple interfaces. If, for example, your computer, with two interfaces, eth0 and eth1, is connected to separate networks, you can use the -i option to restrict access to the computer from both the networks. You can specify different sets of rules for computers using different interfaces to connect to the network.
Resetting Counters in ipchains
You can use the -Z or -zero option to reset counters in ipchains. Assume that you have set the following rule on a Linux computer:
# ipchains -A input -s 0/0 -j DENY
After specifying the above rule, try accessing the computer from another computer on the network by using the ping command. You will not be able to connect to this computer because the above command denies all services.
If you use the -L option along with the -v option to view the rule that have been created, a detailed output of the rules will be displayed:
# ipchains -L -v
Chain input (policy ACCEPT: 40 packets, 3392 bytes):
pkts bytes target prot opt tosa tosx
ifname mark outsize source destination ports
12 1008 DENY all --- 0xFF 0x00 any
anywhere anywhere n/a
Chain forward (policy ACCEPT: 0 packets, 0 bytes):
Chain output (policy ACCEPT: 55 packets, 4652 bytes):
Notice that the number of packets, as specified under the pkts column, is 12. You can reset this value to zero by using the following command:
# ipchains -Z
When you execute the above command, the value of a number of packets will be reset to zero. You can use the -L and -v option to verify that the number of packets has been reset to zero:
# ipchains -L –v
Chain input (policy ACCEPT: 40 packets, 3392 bytes):
pkts bytes target prot opt tosa tosx
fname mark outsize source
destination ports
0 0 DENY all --- 0xFF 0x00 any
anywhere anywhere n/a
Chain forward (policy ACCEPT: 0 packets, 0 bytes):
Chain output (policy ACCEPT: 55 packets, 4652 bytes):
You can combine the -Z option with the -L and -v options and execute the following command:
# ipchains -Z -L -v
The above command displays the existing value of the counter and resets it to zero. The advantage of using the option -Z along with the -L and -v options is that the command displays the current number of packets and then resets these counters to zero. Therefore, no packets are missed. There are chances of packets being missed if these commands are given separately.
Blocking Connection Requests
A connection between a source computer and a destination computer that use the TCP/IP protocol can be set by performing the following steps:
-
The source computer sends a synchronize (SYN) packet to the destination computer. SYN packets are packets that have the SYN bit set in the TCP header.
-
When the destination computer receives the SYN packet, the destination computer sends a SYN + Acknowledgement (ACK) packet back.
-
In response, the source computer sends an ACK packet to the destination computer and a connection is established.
This is known as a three-way handshake to set up a connection. If SYN packets are blocked, a connection is not established. To secure your computer, you can block all packets between your computer and another computer. But when you do that, you cannot access resources on the other computer. To enable your computer to access resources on other computers and prevent other computers from connecting to your computer, you use the ipchains option -y or -syn. You must specify the protocol by using the -p option while using the -y option. For example, the following command blocks packets from the computer with the IP address 172.17.69.114 from connecting with the computer with the IP address 172.17.69.36:
# ipchains -A input -s 172.17.69.114 -d
172.17.69.36 -y -p tcp -j DENY
Blocking TCP Fragments
When the size of a packet is large, the packet is broken down into fragments. These fragments are then transmitted and are reassembled by the receiving computer. When a packet is fragmented, only the first fragment contains all the information about the packet. The subsequent fragments do not contain all the information. Therefore, if a rule is set, only the first fragment can be checked.
To overcome this problem, you can set the always defragment option to Y and recompile the kernel. Alternatively, you can use the -f option and specify a rule for fragments. For example, the following command blocks all fragments from reaching the computer with the IP address 172.17.69.36:
# ipchains -A input -s 0/0 -d 172.17.69.36 -f -j DENY
Blocking Common Attacks
You can protect your network from the following types of attacks:
-
Ping of Death: This term is used when an ICMP packet of unusual size is sent to a computer. The unusual size of ICMP packets causes the buffer maintained by the destination computer to overflow. This can cause problems for certain computers because these computers cannot work after receiving ping of death. To avoid ping of death, you should block ICMP fragments. When ICMP fragments are blocked, large ICMP packet cannot reach the target computer. However, normal ICMP packets will still reach the destination because of their small size.
-
Teardrop and Bonk: In a teardrop attack, a malicious user sends overlapping IP fragments that the target system cannot reassemble. A bonk attack is a variation of a teardrop attack. In a bonk attack, the attacker sends a malformed UDP header to the target system. Both these types of attacks can cause system failure. These types of attacks are mainly targeted against Windows NT. Configuring a Linux server as a router between the local network and the external network can help prevent this type of attack. The Linux server should be configured in such a manner that it defragments all the packets it receives before sending them to the local network. You can also set a rule on the Linux server that prevents any fragments from traveling across a local network.
-
Fragment bombs: When a packet is large, it is split into fragments. At the destination computer, the fragments are reassembled to recreate the packet. If the destination computer does not receive all the fragments, it discards the received fragments. In certain implementations of TCP/IP, the destination computer is not able to discard the packet if all fragments are not received. This problem can be solved if the Linux server acts as a router between the local and external networks, with the always de-fragment option on. Another option is to set rules that filter packets with fragments. By applying such a filter, fragmented packets will not be sent over the network making the network secure.
Blocking IP Spoofing Using ipchains
In IP spoofing, a computer sends packets to another computer with the IP address of another computer. Packet filtering firewalls depend on IP addresses to make decisions. As a result, if the address of an IP packet is incorrect, a firewall can make an incorrect decision. Attackers use false addresses to hide the identity of the computer launching the attack.
To protect your network from IP spoofing attacks, you use Source Address Verification. This needs to be turned on when the computer is switched on. By switching on Source Address Verification, the router checks that the packets that are transmitted have the correct IP address specified. You can enable source address verification by using the following script:
for name in /proc/sys/net/ipv4/conf/*/rp_filter
do
echo 1 > $name
done
The above script changes the file rp_filter from zero to one. The for loop is used to set this value for all the interfaces. This shell script should be executed when the system starts.
You can also use ipchains to set rules for protection against IP spoofing. Say, for example, you have a network connected to the eth0 interface with the IP address 192.168.0.0 and the network mask 255.255.255.0. This computer is connected to a modem that is used to connect to an external network. In this case, you can create rules to protect your computer and any other computer on your local network from IP spoofing by using the following commands:
# ipchains -A input -i eth0 -s ! 192.168.0.0/255.255.255.0 -j DENY
# ipchains -A input -i ! eth0 -s 192.168.0.0/255.255.255.0 -j DENY
The first rule specifies that any packet that is received on the interface eth0 should only originate from the network segment with the network address 192.168.0.0. The second rule specifies that any other interface, such as ppp0, which is used by the modem, should not allow packets with the local address 192.168.0.0 to pass through.
Of the two methods, using the Source Address Verification method is better than using the ipchains command. This is because whenever the network address is changed, you need to modify the rules specified using ipchains.
Denying Access to a Site
If you have a proxy server running on your computer and you want to deny access to specific sites, you can do so by using the ipchains command. Since a Web page is downloaded from the Web server to your computer, you can set a rule in the input chain to deny access to that Web site.
The following command denies access to the Web site www.notallowed.com:
# ipchains -A input -s www.notallowed.com -j DENY
Since no input is allowed from the host www.notallowed.com, no user can access this site through the proxy server.
Setting Type of Service
Type of Service (TOS) is specified using 4 bits in the IP header. Only one of these 4 bits can be set at a time. These bits are used to represent the following service types:
-
Minimum Delay
-
Maximum Throughput
-
Maximum Reliability
-
Minimum Cost
You can set these bits for the FTP and Telnet protocols. For Telnet, you set the service type to Minimum Delay, and for FTP, set it to Maximum Throughput. You can use the -t option to specify these bits. The -t option takes two parameters. Both the parameters are hexadecimal numbers. The first number is ANDed with the packet type of service bits, and the second number is XORed with the packet type of service bits.
For example, you can use the following commands to specify the TOS bits for the Telnet service:
ipchains -A output -p tcp -d 0.0.0.0/0 telnet -t 0x01 0x10
Table 3-1-2 displays values of TOS that can be used to configure various services.
| TOS | Value | Service name |
|---|---|---|
| Minimum Delay | 0x01 0x10 | FTP, Telnet |
| Maximum Throughput | 0x01 0x08 | FTP-data |
| Maximum Reliability | 0x01 0x04 | SNMP |
| Minimum Cost | 0x01 0x02 | NNTP |
Saving and Restoring Settings
The changes that you make using the ipchains command are not permanent. If you restart your system, the settings are lost. If you are not using shell scripts to maintain the firewall system, you can use the ipchains-save command to save the settings. These settings can be restored later:
# ipchains-save > my_firewall
Saving 'output'
The above command saves the current settings of the firewall in the file, my_firewall. The file is stored in the current working directory. Notice the output of the above command. The command displays that it is saving the output chain. This is because only the output chain has defined rules.
You can view the file by using the following cat command:
# cat my_firewall
:input ACCEPT
:forward DENY
:output ACCEPT
-A output -s 172.17.55.242/255.255.255.255 -d
0.0.0.0/0.0.0.0 -j DENY
To restore the settings, use the ipchains-restore command:
# ipchains-restore <>The above command will restore the settings saved in the file, my_firewall.
Creating User-defined Chains
You can create user-defined chains by using the -N option. For example, the following command creates a chain called mychain:
# ipchains -N mychain
# ipchains –L
Chain input (policy ACCEPT):
Chain forward (policy ACCEPT):
Chain output (policy ACCEPT):
Chain mychain (0 references):
You can add a new rule to the user-defined chains. For example, the following command adds a new rule to the user-defined chain called mychain:
# ipchains -A mychain -s 172.17.68.130 -d 172.17.69.36 -j DENY
# ipchains –L
Chain input (policy ACCEPT):
Chain forward (policy ACCEPT):
Chain output (policy ACCEPT):
Chain mychain (0 references):
target prot opt source
destination ports
DENY all --- 172.17.68.130
172.17.69.36 n/a
You can delete user-defined chains by using the -X option. Before deleting a user-defined chain, you must ensure that it is empty. The chain you are about to delete should not be a target for any other rule.
To delete mychain, you first delete the rule assigned to the chain. The following command uses the -F option to delete the rule assigned to mychain:
# ipchains -F mychain
# ipchains –L
Chain input (policy ACCEPT):
Chain forward (policy ACCEPT):
Chain output (policy ACCEPT):
Chain mychain (0 references):
After deleting the rule, you can delete mychain using the following command:
# ipchains -X mychain
# ipchains –L
Chain input (policy ACCEPT):
Chain forward (policy ACCEPT):
Chain output (policy ACCEPT):
| Note |
Assume that you use the following ipchains commands to restrict access to the FTP (port 21), SMTP (port 25), HTTP (port 80), x11 (port 6000), and Telnet (port 23) services on a server:
# ipchains –F
# ipchains -A input -s 0/0 -d 172.17.69.36 21 -p tcp -j DENY
# ipchains -N mychain
# ipchains -A input -s 0/0 -d 172.17.69.36 -j mychain
# ipchains -A mychain -s 0/0 -d 172.17.69.36 80 -p tcp -j DENY
# ipchains -A mychain -s 0/0 -d 172.17.69.36 6000 -p tcp -j DENY
# ipchains -A mychain -s 0/0 -d 172.17.69.36 23 -p tcp -j DENY
# ipchains -A input -s 0/0 -d 172.17.69.36 25 -p tcp -j DENY
After executing the above commands, the ipchains -L command is executed. The -L command displays a list of rules that have been created:
# ipchains –L
Chain input (policy ACCEPT):
target prot opt source
destination ports
DENY tcp --- anywhere
172.17.69.36 any -> ftp
mychain all --- anywhere
172.17.69.36 n/a
DENY tcp --- anywhere
172.17.69.36 any -> smtp
Chain forward (policy ACCEPT):
Chain output (policy ACCEPT):
Chain mychain (1 references):
target prot opt source
destination ports
DENY tcp --- anywhere
172.17.69.36 any -> http
DENY tcp --- anywhere
172.17.69.36 any -> x11
DENY tcp --- anywhere
172.17.69.36 any -> telnet
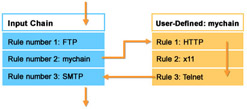
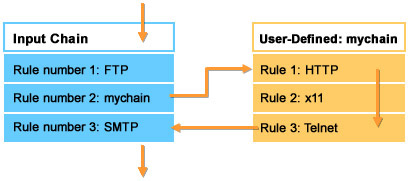
Figure 3-1-3 displays the sequence in which packets are checked for various rules. The rules will be checked in the following sequence:
-
Rule number 1 of the input chain checks for FTP packets.
-
Rule number 2 of the input chain passes the control to a chain called mychain.
-
Rule number 1 of mychain checks for HTTP packets.
-
Rule number 2 of mychain checks for x11 packets.
-
Rule number 3 of mychain checks for Telnet packets. After all the rules in mychain are checked, the control returns to the input chain.
-
Rule number 3 of the input chain checks for SMTP packets.
If any of the above rules match, the packet is denied. Otherwise, the packet is accepted.