Basic Configuration Commands
This section covers some of the commands that you use to create a basic configuration for your security appliance. Some of these commands are the same or similar to those found on an IOS device; other commands, however, are quite different. In most situations, if you need to undo a configuration command, you will either preface the command with the no (which is what you would do on an IOS-based router) or use the clear configure command (delete all the referenced commands).
Host and Domain Names
The name of your appliance defaults to either ciscoasa if it is an ASA or pixfirewall if it is a PIX. You can change the appliance name with the hostname Configuration mode command:
ciscoasa(config)# hostname name_of_your_appliance
The name that you give your appliance only has local significance. The only visible effect of executing this command is that your prompt will include the new name, like this:
ciscoasa(config)# hostname alina
alina(config)# To assign a domain name to your appliance, use the domain-name command:
ciscoasa(config)# domain-name your_appliance's_domain_name
Domain names are required when you generate RSA encryption keys for functions like SSH or digital certificates.
Device Names
One handy feature of the appliance is that you can use the name command to build a static Domain Name Service (DNS) resolution table:
ciscoasa(config)# name IP_address device_name
ciscoasa(config)# names
The name command performs a similar function as the ip host command does on IOS devices: it maps an IP address to a particular name. However, one major difference between the appliance and IOS devices is that when you’re using names on the appliances, any configuration command that references an IP address used by a name command will be replaced with the name in the name command. To enable the use of the name commands, execute the names command.
| Tip | When using names on the appliances, since they will appear in configuration commands with the corresponding IP address, you’ll want to give the devices descriptive names. For example, “inside_PC” or “web_server” as names are not very descriptive; however, “nikas_PC” or “DMZ_web_server” are more meaningful. Once you execute the names command, any static IP address in your configuration that has a corresponding name will be displayed with the name instead of the IP address. |
Passwords
The appliances support two levels of passwords: one for access to User EXEC mode via telnet and SSH, and one for access to Privilege EXEC. These passwords are automatically encrypted when stored in RAM or flash to protect them from eavesdropping attacks.
User EXEC Password
![]() To configure the User EXEC password, use the passwd command:
To configure the User EXEC password, use the passwd command:
ciscoasa# passwd password
Note that this command is really spelled with the letters “or” missing, like the corresponding UNIX command. The password is case-sensitive and can be any combination of characters and numbers. The limit to the length of the password is 16 characters. The default password is cisco for User EXEC access.
| Security Alert! | The default User EXEC password is cisco—you’ll definitely want to change this! User EXEC access via the console port does not use this password. Actually, there is no password for console access unless you implement AAA, which is discussed in Chapter 26. |
Privilege EXEC Password
![]() To set the Privilege EXEC password, use the enable password command:
To set the Privilege EXEC password, use the enable password command:
ciscoasa# enable password password
![]() It is highly recommended that you configure a Privilege EXEC password because there is no default password. This command is somewhat similar to the one for IOS devices, except that this command automatically encrypts the password. The password is case-sensitive and can be any combination of characters and numbers. The length of the password is limited to 16 characters. Remember that when you access Privilege EXEC mode, you’ll always be prompted for a password, even if one hasn’t been configured.
It is highly recommended that you configure a Privilege EXEC password because there is no default password. This command is somewhat similar to the one for IOS devices, except that this command automatically encrypts the password. The password is case-sensitive and can be any combination of characters and numbers. The length of the password is limited to 16 characters. Remember that when you access Privilege EXEC mode, you’ll always be prompted for a password, even if one hasn’t been configured.
| Security Alert! | |
 Login Banner
Login Banner
![]() You can create login banners that are displayed during the login process to the appliance by using the banner command:
You can create login banners that are displayed during the login process to the appliance by using the banner command:
bigdog(config)# banner banner_type banner_description
![]() Table 3-3 lists the banner types you can create.
Table 3-3 lists the banner types you can create.
| | |
|---|---|
| | |
| | |
| | |
| | |
 Interfaces
Interfaces
![]() Now that you have configured the name, passwords, and login banner on your appliance, you are ready to proceed with the configuration of the appliance interfaces. Before I discuss the configuration of the interfaces, I’ll first discuss the nomenclature used for interfaces.
Now that you have configured the name, passwords, and login banner on your appliance, you are ready to proceed with the configuration of the appliance interfaces. Before I discuss the configuration of the interfaces, I’ll first discuss the nomenclature used for interfaces.
Interface Nomenclature
![]() Interfaces on your appliances have two names to distinguish them:
Interfaces on your appliances have two names to distinguish them:
-
 Physical name, commonly called a hardware name
Physical name, commonly called a hardware name -
 Logical name
Logical name
![]() The following sections will discuss the differences between the two.
The following sections will discuss the differences between the two.
Physical Names
![]() The physical name is used whenever you need to configure the physical properties of an interface, like its speed, duplexing, or IP address. The appliance you have will affect the physical names you use. On the PIX, all the names of the physical interfaces begin with “ethernet,” which can be abbreviated to the letter e and is followed with the interface number, which begins with 0. For example, the first interface on a PIX is ethernet0, or e0 for short.
The physical name is used whenever you need to configure the physical properties of an interface, like its speed, duplexing, or IP address. The appliance you have will affect the physical names you use. On the PIX, all the names of the physical interfaces begin with “ethernet,” which can be abbreviated to the letter e and is followed with the interface number, which begins with 0. For example, the first interface on a PIX is ethernet0, or e0 for short.
![]() The ASAs are different with their nomenclature:
The ASAs are different with their nomenclature:
-
 The 5505 physical interface names are ethernet0/number, where the numbers range from 0 to 7. An example would be ethernet0/0, or e0/0 for short.
The 5505 physical interface names are ethernet0/number, where the numbers range from 0 to 7. An example would be ethernet0/0, or e0/0 for short. -
 The 5510 physical interface names are ethernet slot/number, where the slot number of 0 is the four fixed interfaces on the chassis, and slot 1 refers to the interfaces on the SSM card if it’s installed. For example, ethernet0/0, or e0/0 for short, would refer to the rightmost data interface on the chassis.
The 5510 physical interface names are ethernet slot/number, where the slot number of 0 is the four fixed interfaces on the chassis, and slot 1 refers to the interfaces on the SSM card if it’s installed. For example, ethernet0/0, or e0/0 for short, would refer to the rightmost data interface on the chassis. -
 The 5520s and higher use a physical name of “gigabitethernet”: gigabitethernetslot/number. For example, gigabitethernet0/0, or g0/0 for short, would refer to the rightmost data interface on the chassis.
The 5520s and higher use a physical name of “gigabitethernet”: gigabitethernetslot/number. For example, gigabitethernet0/0, or g0/0 for short, would refer to the rightmost data interface on the chassis.
![]() The 5510s and higher support a management interface (the 5580s support two management interfaces). The nomenclature of this interface is management0/0. The management interface, by default, will not pass traffic through it: only traffic to it or from it. Cisco designed this interface primarily for out-of-band management of the appliance using IP. However, you can override this behavior and use the management interface as a data interface. To use the management interface as a data interface, configure the following:
The 5510s and higher support a management interface (the 5580s support two management interfaces). The nomenclature of this interface is management0/0. The management interface, by default, will not pass traffic through it: only traffic to it or from it. Cisco designed this interface primarily for out-of-band management of the appliance using IP. However, you can override this behavior and use the management interface as a data interface. To use the management interface as a data interface, configure the following:
ciscoasa(config)# interface management0/0
ciscoasa(config-if)# no management-only
![]() Once you have done this, you can treat the management interface as a physical interface and reference it in your policy commands, like ACLs and address translation commands.
Once you have done this, you can treat the management interface as a physical interface and reference it in your policy commands, like ACLs and address translation commands.
Logical Names
![]() Logical names are used in most other commands, like applying an ACL to an interface, or specifying an interface for an address translation policy. Logical names should be descriptive about what the interface is connected to. Two common names used are “inside” (connected to your internal network) and “outside” (connected to the external or public network).
Logical names are used in most other commands, like applying an ACL to an interface, or specifying an interface for an address translation policy. Logical names should be descriptive about what the interface is connected to. Two common names used are “inside” (connected to your internal network) and “outside” (connected to the external or public network).
Security Levels
![]() Each interface has a security level assigned to it that can range from 0 to 100. The least secure is 0 and the most secure is 100. Assuming you are using the name of “inside” for an interface, the security level defaults to 100. All other interface names have the security level default to 0 (the least secure). The security algorithm uses the security levels to enforce its security policies. Here are the rules that the algorithm uses:
Each interface has a security level assigned to it that can range from 0 to 100. The least secure is 0 and the most secure is 100. Assuming you are using the name of “inside” for an interface, the security level defaults to 100. All other interface names have the security level default to 0 (the least secure). The security algorithm uses the security levels to enforce its security policies. Here are the rules that the algorithm uses:
-
 Traffic from a higher to a lower security level is permitted by default, unless you have restricted traffic with an ACL. This is called an outbound connection.
Traffic from a higher to a lower security level is permitted by default, unless you have restricted traffic with an ACL. This is called an outbound connection. -
 Traffic from a lower to a higher level is denied, by default, unless you explicitly permit it by configuring access control lists (ACLs), discussed in Chapter 6, and/or configure Cut-through Proxy (CTP) authentication, discussed in Chapter 8. This is called an inbound connection.
Traffic from a lower to a higher level is denied, by default, unless you explicitly permit it by configuring access control lists (ACLs), discussed in Chapter 6, and/or configure Cut-through Proxy (CTP) authentication, discussed in Chapter 8. This is called an inbound connection. -
 Traffic from the same security level to the same level is denied by default.
Traffic from the same security level to the same level is denied by default.
![]() To allow traffic between interfaces with the same security level, use the following command:
To allow traffic between interfaces with the same security level, use the following command:
ciscoasa(config)# same-security-traffic permit inter-interface
![]() Once you execute this command, all traffic is permitted between interfaces with the same level number; if you want to restrict this traffic, use ACLs, which are discussed in Chapter 6.
Once you execute this command, all traffic is permitted between interfaces with the same level number; if you want to restrict this traffic, use ACLs, which are discussed in Chapter 6.
| Security Alert! | |
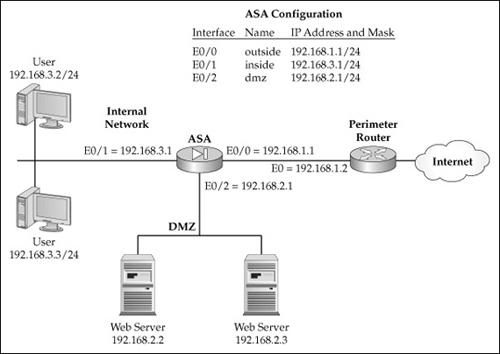
![]() Let’s look at an example to illustrate the use of security levels. Figure 3-1 shows a network that I use throughout the rest of this chapter. In this example, the appliance has three interfaces: an external (connected to the perimeter router and the Internet), an internal, and a DMZ interface. With the appliance security algorithm in action, here are the data connections that are, by default, permitted:
Let’s look at an example to illustrate the use of security levels. Figure 3-1 shows a network that I use throughout the rest of this chapter. In this example, the appliance has three interfaces: an external (connected to the perimeter router and the Internet), an internal, and a DMZ interface. With the appliance security algorithm in action, here are the data connections that are, by default, permitted:
-
 Traffic from the inside interface to the DMZ
Traffic from the inside interface to the DMZ -
 Traffic from the inside interface to the outside
Traffic from the inside interface to the outside -
 Traffic from the DMZ interface to the outside
Traffic from the DMZ interface to the outside
![]() If the traffic originates from any source other than the ones listed here and is going to any other destination through the security appliance, the appliance will automatically deny it.
If the traffic originates from any source other than the ones listed here and is going to any other destination through the security appliance, the appliance will automatically deny it.
Physical Interface Configuration
![]() To configure the properties of a physical interface, access the interface using the interface command, referencing its physical interface name. (This will take you into a subcommand mode where the commands you enter affect only the specified interface.)
To configure the properties of a physical interface, access the interface using the interface command, referencing its physical interface name. (This will take you into a subcommand mode where the commands you enter affect only the specified interface.)
ciscoasa(config)# interface physical_if_name
ciscoasa(config-if)# nameif logical_if_name
ciscoasa(config-if)# ip address IP_address [subnet_mask]
ciscoasa(config-if)# security-level number
ciscoasa(config-if)# speed {10|100|1000|auto|nonegotiate}
ciscoasa(config-if)# duplex {auto|full|half}
ciscoasa(config-if)# [no] shutdown
![]() In version 7.0, Cisco introduced an Interface subcommand mode; in prior versions, global commands were used to configure interface properties. The interface command specifies the name of the physical interface and the interface identifier (slot and port). The nameif command assigns a logical name to the interface. If you assign a name of “inside” to the interface, the security level defaults to 100. Any other logical name defaults the security level to 0. The ip address command assigns a static IP address to the interface; omitting the subnet mask will cause the mask to default to the configured class of the IP address. You can also assign a dynamic address to the interface using DHCP or PPPoE—this is discussed later in the chapter in the “Dynamic Addressing” section. The security-level command assigns a security level to the interface: this can range from 0 (least trusted) to 100 (most trusted). The speed and duplex commands set the speed and duplexing of the interface. By default, interfaces are disabled and need to be enabled with the no shutdown command.
In version 7.0, Cisco introduced an Interface subcommand mode; in prior versions, global commands were used to configure interface properties. The interface command specifies the name of the physical interface and the interface identifier (slot and port). The nameif command assigns a logical name to the interface. If you assign a name of “inside” to the interface, the security level defaults to 100. Any other logical name defaults the security level to 0. The ip address command assigns a static IP address to the interface; omitting the subnet mask will cause the mask to default to the configured class of the IP address. You can also assign a dynamic address to the interface using DHCP or PPPoE—this is discussed later in the chapter in the “Dynamic Addressing” section. The security-level command assigns a security level to the interface: this can range from 0 (least trusted) to 100 (most trusted). The speed and duplex commands set the speed and duplexing of the interface. By default, interfaces are disabled and need to be enabled with the no shutdown command.
VLAN Configuration
![]() Starting in version 6.3, the security appliance operating system supports trunk connections. Of all the appliances, only the PIX 501 lacks support for trunks and VLANs. Only the 802.1Q trunking protocol is supported: Cisco’s proprietary ISL is not.
Starting in version 6.3, the security appliance operating system supports trunk connections. Of all the appliances, only the PIX 501 lacks support for trunks and VLANs. Only the 802.1Q trunking protocol is supported: Cisco’s proprietary ISL is not.
![]() VLANs are implemented by creating a subinterface (a logical interface associated with a physical interface) and by associating the VLAN identifier (the VLAN number) that the subinterface should process. For the physical interface the subinterfaces are associated with, typically only hardware characteristics (speed, duplexing, bringing it up) are configured. IP addresses, security levels, and logical names are configured on the subinterfaces. The one exception to this rule is if you need to use the native VLAN in 802.1Q; in this instance, you configure the IP address, security level, and logical name on the physical interface (the physical interface handles untagged frames).
VLANs are implemented by creating a subinterface (a logical interface associated with a physical interface) and by associating the VLAN identifier (the VLAN number) that the subinterface should process. For the physical interface the subinterfaces are associated with, typically only hardware characteristics (speed, duplexing, bringing it up) are configured. IP addresses, security levels, and logical names are configured on the subinterfaces. The one exception to this rule is if you need to use the native VLAN in 802.1Q; in this instance, you configure the IP address, security level, and logical name on the physical interface (the physical interface handles untagged frames).
![]() Creating a VLAN interface is done the same as it’s done on a Cisco IOS router; however, associating the VLAN tag to the subinterface is different from that on a Cisco router. Here is the configuration to create the subinterface and to identify the VLAN for the subinterface:
Creating a VLAN interface is done the same as it’s done on a Cisco IOS router; however, associating the VLAN tag to the subinterface is different from that on a Cisco router. Here is the configuration to create the subinterface and to identify the VLAN for the subinterface:
ciscoasa(config)# interface physical_name slot_#/port_#.subid_#
ciscoasa(config-subif)# vlan vlan_#
![]() The subid_# is the number of the subinterface. The number you specify here doesn’t have to match the VLAN number the interface will process; however, it is common practice.
The subid_# is the number of the subinterface. The number you specify here doesn’t have to match the VLAN number the interface will process; however, it is common practice.
| Tip | |
![]() Here is a simple example illustrating the use of VLANs on a physical interface:
Here is a simple example illustrating the use of VLANs on a physical interface:
ciscoasa(config)# interface ethernet0/0
ciscoasa(config-if)# no shutdown
ciscoasa(config-if)# exit
ciscoasa(config)# interface ethernet0/0.1
ciscoasa(config-subif)# vlan 10
ciscoasa(config-subif)# ip address 192.168.10.1 255.255.255.0
ciscoasa(config-subif)# nameif dmz1
ciscoasa(config-subif)# security-level 51
ciscoasa(config-subif)# exit
ciscoasa(config)# interface ethernet0/0.2
ciscoasa(config-subif)# vlan 20
ciscoasa(config-subif)# ip address 192.168.20.1 255.255.255.0
ciscoasa(config-subif)# nameif dmz1
ciscoasa(config-subif)# security-level 50
ciscoasa(config-subif)# exit
![]() Notice that the only thing done on the physical interface is to enable it, since in this example the appliance doesn’t need to process traffic for the native VLAN.
Notice that the only thing done on the physical interface is to enable it, since in this example the appliance doesn’t need to process traffic for the native VLAN.
ASA 5505 Interface Configuration
![]() The model 5505 use of interfaces differs from all the other ASAs: the eight interfaces (e0/0 through e0/7) are layer 2 switch ports. Unlike the other ASAs, the 5505 doesn’t use subinterfaces to associate interfaces with VLANs. Instead, a logical layer 3 interface called a VLAN interface is used. As you will see shortly, the configuration is somewhat similar to Cisco’s IOS switches. With a Base license installed, three VLAN interfaces are supported. With the Security Plus license, three VLAN interfaces are supported using the local interfaces, and one interface can be set up as a trunk, supporting a total of 20 VLANs across the physical interfaces and the trunk.
The model 5505 use of interfaces differs from all the other ASAs: the eight interfaces (e0/0 through e0/7) are layer 2 switch ports. Unlike the other ASAs, the 5505 doesn’t use subinterfaces to associate interfaces with VLANs. Instead, a logical layer 3 interface called a VLAN interface is used. As you will see shortly, the configuration is somewhat similar to Cisco’s IOS switches. With a Base license installed, three VLAN interfaces are supported. With the Security Plus license, three VLAN interfaces are supported using the local interfaces, and one interface can be set up as a trunk, supporting a total of 20 VLANs across the physical interfaces and the trunk.
![]() By default, two VLAN interfaces are configured on the ASA 5505. Table 3-4 displays the properties of these two logical interfaces.
By default, two VLAN interfaces are configured on the ASA 5505. Table 3-4 displays the properties of these two logical interfaces.
| | | |
|---|---|---|
| | | |
| | | |
| | | |
| | | |
![]() To change the properties of the two logical VLAN interfaces, or to create a new logical VLAN interface, use the following configuration:
To change the properties of the two logical VLAN interfaces, or to create a new logical VLAN interface, use the following configuration:
ciscoasa(config)# interface vlan vlan_#
ciscoasa(config-if)# nameif logical_name
ciscoasa(config-if)# ip address IP_address [subnet_mask]
ciscoasa(config-if)# security-level number
![]() To associate a physical interface with a logical VLAN interface, use the following configuration:
To associate a physical interface with a logical VLAN interface, use the following configuration:
ciscoasa(config)# interface physical_name
ciscoasa(config-if)# switchport access vlan vlan_#
![]() Here’s an example configuration with three logical interfaces: inside, outside, and dmz:
Here’s an example configuration with three logical interfaces: inside, outside, and dmz:
ciscoasa(config)# interface vlan 1
ciscoasa(config-if)# nameif inside
ciscoasa(config-if)# ip address 192.168.1.1 255.255.255.0
ciscoasa(config-if)# security-level 100
ciscoasa(config-if)# exit
ciscoasa(config)# interface vlan 2
ciscoasa(config-if)# nameif outside
ciscoasa(config-if)# ip address 200.1.1.1 255.255.255.248
ciscoasa(config-if)# security-level 0
ciscoasa(config-if)# exit
ciscoasa(config)# interface vlan 3
ciscoasa(config-if)# nameif dmz
ciscoasa(config-if)# ip address 192.168.2.1 255.255.255.0
ciscoasa(config-if)# security-level 50
ciscoasa(config-if)# exit
ciscoasa(config)# interface ethernet0/0
ciscoasa(config-if)# switchport access vlan 2
ciscoasa(config-if)# no shutdown
ciscoasa(config-if)# exit
ciscoasa(config)# interface ethernet0/1
ciscoasa(config-if)# switchport access vlan 1
ciscoasa(config-if)# no shutdown
ciscoasa(config-if)# exit
ciscoasa(config)# interface ethernet0/2
ciscoasa(config-if)# switchport access vlan 3
ciscoasa(config-if)# no shutdown
ciscoasa(config-if)# exit
![]() Use the show switch vlan command to verify your VLAN configuration on the ASA 5505 (from the preceding configuration):
Use the show switch vlan command to verify your VLAN configuration on the ASA 5505 (from the preceding configuration):
ciscoasa# show switch vlan
VLAN Name Status Ports
---- ------------------ --------- -----------------------------
1 inside up Et0/1, Et0/3, Et0/4, Et0/5,
Et0/6, Et0/7
2 outside up Et0/0
3 dmz up Et0/2
Interface Verification
![]() Now that you have set up your physical and/or logical interfaces, you are ready to verify your settings by using show commands. To examine an interface, use the show interface command:
Now that you have set up your physical and/or logical interfaces, you are ready to verify your settings by using show commands. To examine an interface, use the show interface command:
ciscoasa# show interface
Interface Ethernet0/0 "", is administratively down,
line protocol is down
Hardware is 88E6095, BW 100 Mbps, DLY 100 usec
Auto-Duplex, Auto-Speed
Available but not configured via nameif
MAC address 001f.9e2e.e512, MTU not set
IP address unassigned
0 packets input, 0 bytes, 0 no buffer
Received 0 broadcasts, 0 runts, 0 giants
0 input errors, 0 CRC, 0 frame, 0 overrun, 0 ignored, 0 abort
<--output omitted-->
![]() The format of the output of this command is very similar to the same command used on IOS devices. One important item to point out is the first line of output, where the status is shown for both the physical and data link layers respectively. In this example, the interface is disabled. Here are the status values of the interface:
The format of the output of this command is very similar to the same command used on IOS devices. One important item to point out is the first line of output, where the status is shown for both the physical and data link layers respectively. In this example, the interface is disabled. Here are the status values of the interface:
-
 If you see up and up, both the physical and data link layers are functioning correctly.
If you see up and up, both the physical and data link layers are functioning correctly. -
 If you see up and down, there is a data link layer problem.
If you see up and down, there is a data link layer problem. -
 If you see down and down, there is a physical layer problem.
If you see down and down, there is a physical layer problem. -
 If you see administratively down and down, the interface has been manually disabled.
If you see administratively down and down, the interface has been manually disabled.
![]() The show interface command displays all of the interfaces on the appliance. If you are only interested in seeing the status of a single interface, enter the show interface command followed by the physical name of the interface, like ethernet0/0. You can also display just the status of a subinterface, like ethernet0/0.1, or a VLAN interface on a 5505, like vlan 1.
The show interface command displays all of the interfaces on the appliance. If you are only interested in seeing the status of a single interface, enter the show interface command followed by the physical name of the interface, like ethernet0/0. You can also display just the status of a subinterface, like ethernet0/0.1, or a VLAN interface on a 5505, like vlan 1.
![]() You can use either the show interface or show ip[address] command to view the IP configuration of your appliance interfaces:
You can use either the show interface or show ip[address] command to view the IP configuration of your appliance interfaces:
ciscoasa(config)# show ip
System IP Addresses:
ip address outside 192.168.1.1 255.255.255.0
ip address inside 192.168.3.1 255.255.255.0
ip address dmz 192.168.2.1 255.255.255.0
Current IP Addresses:
ip address outside 192.168.1.1 255.255.255.0
ip address inside 192.168.3.1 255.255.255.0
ip address dmz 192.168.2.1 255.255.255.0
![]() The System IP Addresses are the IP addresses assigned to the active appliance when you have failover configured. If this appliance were the standby unit, it would assume these addresses on the interface when a failover occurred. The Current IP Addresses are the IP addresses currently being used on the interface. Failover is discussed in Chapter 23.
The System IP Addresses are the IP addresses assigned to the active appliance when you have failover configured. If this appliance were the standby unit, it would assume these addresses on the interface when a failover occurred. The Current IP Addresses are the IP addresses currently being used on the interface. Failover is discussed in Chapter 23.
| Tip | |
 Dynamic Addressing
Dynamic Addressing
![]() Besides specifying a static IP address, you can also acquire addressing dynamically by using DHCP (Dynamic Host Configuration Protocol) or PPP over Ethernet (PPPoE). The following two sections will discuss these approaches.
Besides specifying a static IP address, you can also acquire addressing dynamically by using DHCP (Dynamic Host Configuration Protocol) or PPP over Ethernet (PPPoE). The following two sections will discuss these approaches.
DHCP Client
![]() Your appliance can be a DHCP client and obtain its addressing information on interface(s) dynamically from a DHCP server. Here’s the interface syntax for an interface using DHCP to acquire its addressing information:
Your appliance can be a DHCP client and obtain its addressing information on interface(s) dynamically from a DHCP server. Here’s the interface syntax for an interface using DHCP to acquire its addressing information:
ciscoasa(config)# interface physical_name
ciscoasa(config-if)# ip address dhcp [setroute] [retry retry_count]
![]() The setroute parameter causes the appliance to accept the default route from the DHCP server—this is typically done when your outside interface is acquiring its addressing dynamically from the ISP. If you omit this parameter, you’ll need to configure a default route on your appliance (this is discussed in Chapter 4). You can also specify the number of times the appliance should attempt to obtain its addressing.
The setroute parameter causes the appliance to accept the default route from the DHCP server—this is typically done when your outside interface is acquiring its addressing dynamically from the ISP. If you omit this parameter, you’ll need to configure a default route on your appliance (this is discussed in Chapter 4). You can also specify the number of times the appliance should attempt to obtain its addressing.
| Note | |
![]() To verify your addressing information, use the show ip address dhcp command:
To verify your addressing information, use the show ip address dhcp command:
ciscoasa# show ip address outside dhcp lease
Temp IP Addr:200.200.200.2 for peer on interface:outside
Temp sub net mask:255.255.255.0
DHCP Lease server:200.200.199.2, state:3 Bound
DHCP Transaction id:0x4123
Lease:7200 secs, Renewal:1505 secs, Rebind:7000 secs
Temp default-gateway addr:200.200.200.1
Next timer fires after:6809 secs
Retry count:0, Client-ID:cisco-0000.0000.0000-outside
![]() To perform detailed troubleshooting, the appliances support debug capabilities similar to IOS-based devices. Cisco also supports debug commands for troubleshooting the DHCP client on the appliance. Here are the debug commands that you can use:
To perform detailed troubleshooting, the appliances support debug capabilities similar to IOS-based devices. Cisco also supports debug commands for troubleshooting the DHCP client on the appliance. Here are the debug commands that you can use:
-
 debug dhcpc packet Displays the partial contents of DHCP client packets
debug dhcpc packet Displays the partial contents of DHCP client packets -
 debug dhcpc error Displays DHCP client error information
debug dhcpc error Displays DHCP client error information -
 debug dhcpc detail Displays all information related to DHCP client packets
debug dhcpc detail Displays all information related to DHCP client packets
| Tip | |
PPP over Ethernet (PPPoE)
![]() PPPoE is typically used on broadband DSL connections to an ISP. Configuring PPPoE involves these tasks:
PPPoE is typically used on broadband DSL connections to an ISP. Configuring PPPoE involves these tasks:
-
 Creating a PPPoE group
Creating a PPPoE group -
 Specifying the PPP authentication method: PAP, CHAP, or MS-CHAP
Specifying the PPP authentication method: PAP, CHAP, or MS-CHAP -
 Associating a username to the PPPoE group
Associating a username to the PPPoE group -
 Creating a local username account and password assigned by the ISP
Creating a local username account and password assigned by the ISP -
 Enabling PPPoE on the interface
Enabling PPPoE on the interface
| Note | |
![]() Here is the syntax to accomplish the preceding tasks:
Here is the syntax to accomplish the preceding tasks:
ciscoasa(config)# vpdn group group_name request dialout pppoe
ciscoasa(config)# vpdn group group_name ppp authentication
{chap | mschap | pap}
ciscoasa(config)# vpdn group group_name localname username
ciscoasa(config)# vpdn username username password password [store-local]
ciscoasa(config)# interface physical_if_name
ciscoasa(config-if)# ip address pppoe [setroute]
![]() The first vpdn group command specifies a locally significant group name that groups together the appliance PPPoE commands for an interface. The second vpdn group command specifies the PPP authentication method to use. The third vpdn group command specifies the local user account the ISP assigned. The vpdn username command specifies the username and password assigned by the ISP; the store-local parameter causes the appliance to store the username and password in a special place in flash so that a clear configure command will not erase it. Once you have configured your PPPoE parameters, enable PPPoE on the interface with the ip address pppoe command; the setroute parameter performs the same function as with the ip address dhcp command from the previous section.
The first vpdn group command specifies a locally significant group name that groups together the appliance PPPoE commands for an interface. The second vpdn group command specifies the PPP authentication method to use. The third vpdn group command specifies the local user account the ISP assigned. The vpdn username command specifies the username and password assigned by the ISP; the store-local parameter causes the appliance to store the username and password in a special place in flash so that a clear configure command will not erase it. Once you have configured your PPPoE parameters, enable PPPoE on the interface with the ip address pppoe command; the setroute parameter performs the same function as with the ip address dhcp command from the previous section.
![]() Once you have configured PPPoE, use these show commands for verification:
Once you have configured PPPoE, use these show commands for verification:
-
 show ip address logical_if_name pppoe Displays the IP addressing for the outside interface
show ip address logical_if_name pppoe Displays the IP addressing for the outside interface -
 show vpdn [session pppoe] Displays the PPPoE session information
show vpdn [session pppoe] Displays the PPPoE session information
![]() The first show command displays the appliance PPPoE client configuration information. Its output is similar to that of the show ip address dhcp command. The show vpdn command shows a brief overview of the PPPoE sessions:
The first show command displays the appliance PPPoE client configuration information. Its output is similar to that of the show ip address dhcp command. The show vpdn command shows a brief overview of the PPPoE sessions:
ciscoasa# show vpdn
Tunnel id 0, 1 active sessions
time since change 1209 secs
Remote Internet Address 192.168.1.1
Local Internet Address 200.200.200.1
12 packets sent, 12 received, 168 bytes sent, 0 received
Remote Internet Address is 192.168.1.1
Session state is SESSION_UP
<--output omitted-->
![]() This example has one active PPPoE session. You can restrict the output of this command by adding the session pppoe parameters—this will only display PPPoE information, and no VPN information.
This example has one active PPPoE session. You can restrict the output of this command by adding the session pppoe parameters—this will only display PPPoE information, and no VPN information.
![]() For detailed troubleshooting of PPPoE, use the debug command:
For detailed troubleshooting of PPPoE, use the debug command:
 ciscoasa(config)# debug pppoe {event | error | packet}
ciscoasa(config)# debug pppoe {event | error | packet} ![]() The event parameter displays protocol event information concerning PPPoE. The error parameter displays any PPPoE error messages. The packet parameter displays the partial contents of PPPoE packets.
The event parameter displays protocol event information concerning PPPoE. The error parameter displays any PPPoE error messages. The packet parameter displays the partial contents of PPPoE packets.
Dynamic DNS
![]() Dynamic DNS is a feature where the appliance, acting as a DHCP client, obtains its IP address dynamically from a DHCP server. The appliance can then update a DNS server with its name and the dynamic address. Therefore, no matter what dynamic IP address is assigned to the appliance, you can always use the same name to reach it.
Dynamic DNS is a feature where the appliance, acting as a DHCP client, obtains its IP address dynamically from a DHCP server. The appliance can then update a DNS server with its name and the dynamic address. Therefore, no matter what dynamic IP address is assigned to the appliance, you can always use the same name to reach it.
![]() To configure this process, use the following commands:
To configure this process, use the following commands:
ciscoasa(config)# dhcp-client update dns server none
ciscoasa(config)# ddns update method ddns-2
ciscoasa(DDNS-update-method)# ddns both
ciscoasa(DDNS-update-method)# exit
ciscoasa(config)# interface physical_if_name
ciscoasa(if-config)# ddns update ddns-2
ciscoasa(if-config)# ddns update hostname appliance's_FQDN
![]() The dhcp-client update command specifies that the client (the appliance itself), rather than the DHCP server, will update the DNS server with the dynamic addressing information. The ddns update and ddns both commands specify that the appliance will update both the A and PTR DNS records on the DNS server.
The dhcp-client update command specifies that the client (the appliance itself), rather than the DHCP server, will update the DNS server with the dynamic addressing information. The ddns update and ddns both commands specify that the appliance will update both the A and PTR DNS records on the DNS server.
![]() Once you have done this, you need to enable dynamic DNS on the physical or VLAN interface with the ddns update ddns-2 command and to specify the fully qualified domain name (FQDN) being passed to the DNS server with the ddns update hostname command, like “appliance.dealgroup.com”.
Once you have done this, you need to enable dynamic DNS on the physical or VLAN interface with the ddns update ddns-2 command and to specify the fully qualified domain name (FQDN) being passed to the DNS server with the ddns update hostname command, like “appliance.dealgroup.com”.