Site-to-Site Verification
Once you’ve configured your Phase 1 and Phase 2 commands, and traffic matches a crypto ACL entry destined for the remote peer, a tunnel is built, barring any misconfiguration or other issues. This section will show you how to view, tear down, and troubleshoot your IPSec connections. Please note that these commands apply to all IPSec connections: L2L and remote access.
| Tip | One common entry to include in a crypto ACL is ICMP traffic associated with the two peers. This way performing a ping from one of the peers will attempt to bring the tunnel up. |
Viewing and Clearing Connections
This section discusses how to view and tear down the Phase 1 management and Phase 2 data connections.
ISAKMP Phase 1—Management Connections
To view the Phase 1 management connections that you have established to remote peers, use the show crypto isakmp sa command:
ciscoasa# show [crypto] isakmp sa [detail] Here is an example of viewing the management connections:
ciscoasa# show crypto isakmp sa
Active SA: 1
Rekey SA: 0 (A tunnel will report 1 Active and 1 Rekey SA during
rekey)
Total IKE SA: 1
1 IKE Peer: 192.1.1.40
Type : L2L Role : responder
Rekey : no State : MM_ACTIVE The State should be MM_ACTIVE (main mode) or AG_ACTIVE (aggressive mode) if the management connection is successfully built.
To tear down management connections, use the clear crypto isakmp sa command:
ciscoasa# clear [crypto] isakmp sa
ISAKMP Phase 2—Data Connections
To view all the IPSec data SAs that you have established to peers, use the show crypto ipsec sa command:
ciscoasa# show crypto ipsec sa [entry | identity | map map_name |
peer peer_IP_addr] [detail] Here’s an example of the use of this command:
ciscoasa# show crypto ipsec sa
interface: outside
Crypto map tag: mymap, local addr: 192.1.1.100
local ident (addr/mask/prot/port): (192.168.2.0/255.255.255.0/0/0)
remote ident (addr/mask/prot/port): (192.168.0.0/255.255.255.0/0/0)
current_peer: 192.1.1.40
#pkts encaps: 4, #pkts encrypt: 4, #pkts digest: 4
#pkts decaps: 4, #pkts decrypt: 4, #pkts verify: 4
#pkts compressed: 0, #pkts decompressed: 0
#pkts not compressed: 4, #pkts comp failed: 0, #pkts decomp
failed: 0
#send errors: 0, #recv errors: 0
local crypto endpt.: 192.1.1.100, remote crypto endpt.: 192.1.1.40
path mtu 1500, ipsec overhead 76, media mtu 1500
current outbound spi: 2ED644AD
inbound esp sas:
spi: 0x76DFE868 (1994385512)
transform: esp-aes esp-sha-hmac
in use settings ={L2L, Tunnel,}
slot: 0, conn_id: 1, crypto-map: mymap
sa timing: remaining key lifetime (kB/sec): (4274999/3586)
IV size: 16 bytes
replay detection support: Y
outbound esp sas:
spi: 0x2ED644AD (785794221)
transform: esp-aes esp-sha-hmac
in use settings ={L2L, Tunnel,}
slot: 0, conn_id: 1, crypto-map: mymap
sa timing: remaining key lifetime (kB/sec): (4274999/3584)
IV size: 16 bytes
replay detection support: Y Every time you execute this command, if you see pkts information incrementing, then you have traffic traversing the tunnel. At the bottom, you see two sections—inbound and outbound esp sas. These are the two data connections built during Phase 2.
To tear down the data SA(s), use the clear crypto ipsec sa command:
ciscoasa# clear [crypto] ipsec sa [counters |
entry {hostname | ip_address} {esp spi |
map map_name | peer {hostname | ip_address}] Troubleshooting Connections
For detailed troubleshooting of ISAKMP/IKE interaction with a remote peer, use the debug crypto isakmp command. This command displays the building of the Phase 1 and 2 connections:
ciscoasa# debug crypto isakmp [1-255] If you omit the number at the end of the command, it defaults to “1,” which displays a single message about the success or failure of the building of the tunnel. Specifying 255 is a complete hex dump of the packets. Specifying a number in the range of 100–150 gives you similar output to what you would find with this command on an IOS router. For troubleshooting of just the Phase 2 processes on the appliance, use the debug crypto ipsec command.
Site-to-Site Example
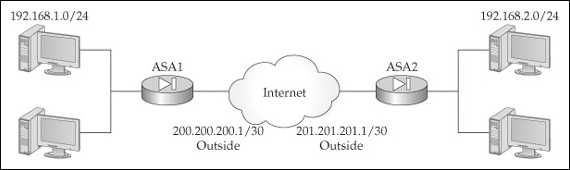
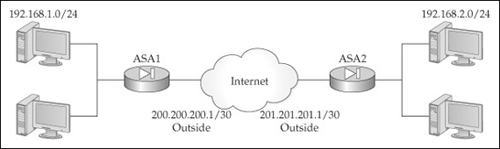
To help understand the configuration of L2L connections, let’s look at an example. I’ll use the network shown in Figure 16-2. I’ve broken the configuration into different parts to make it easier to understand. Here’s the Phase 1 configuration for asa1 in this network:
asa1(config)# sysopt connection permit-vpn
asa1(config)# crypto isakmp policy 100
asa1(config-isakmp-policy)# authentication pre-share
asa1(config-isakmp-policy)# encryption aes
asa1(config-isakmp-policy)# group 2
asa1(config-isakmp-policy)# hash md5
asa1(config)# tunnel-group 201.201.201.1 type ipsec-l2l
asa1(config)# tunnel-group 201.201.201.1 ipsec-attributes
asa1(config-tunnel-ipsec)# pre-shared-key ASA2KEY
The first command exempts inbound IPSec traffic, once verified and decrypted, from ACL processing. The ISAKMP policy specifies the use of pre-shared keys, where the pre-shared key is configured in the tunnel group (case-sensitive). The tunnel group identifier is the IP address of the remote peer (asa2)—remember that the identity type defaults to “address.”
The following is the Phase 2 configuration for asa1:
asa1(config)# access-list MATCH permit ip 192.168.1.0 255.255.255.0
192.168.2.0 255.255.255.0
asa1(config)# nat (inside) 0 access-list MATCH
asa1(config)# crypto ipsec transform-set asa2transform
esp-sha-hmac esp-3des
asa1(config)# crypto map IPSECMAP 100 set peer 201.201.201.1
asa1(config)# crypto map IPSECMAP 100 match address MATCH
asa1(config)# crypto map IPSECMAP 100 set transform-set asa2transform
asa1(config)# crypto map IPSECMAP interface outside
The first part defines an ACL that is used for identity NAT as well as the crypto ACL. The second part creates a transform set. The third part creates and applies a crypto map. Notice that the crypto map entry specifies asa2 as the remote peer, the crypto ACL, and the transform set.
| Tip | : If asa1 has connections to two sites, like asa2 and asa3, and you want traffic to flow from asa2, through asa1, to asa3, then you’ll need to configure the same-security-traffic permit intra-interface command on asa1 to allow traffic to flow into and out of the same interface. |