Notice: In the exam, some Drag and Drop Questions may be represented as multiple-choice questions.
Question 1
On the basis of the description of SSL-based VPN, place the correct descriptions in the proper locations.
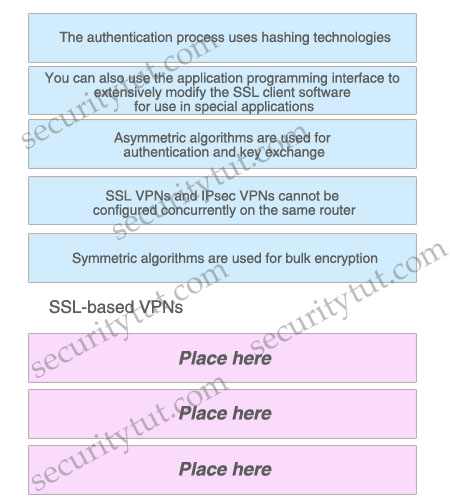
Answer:
+ The authentication process uses hashing technologies.
+ Asymmetric algorithms are used for authentication and key exchange.
+ Symmetric algorithms are used for bulk encryption.
Question 2
Which three common examples are of AAA implementation on Cisco routers? Please place the correct descriptions in the proper locations.
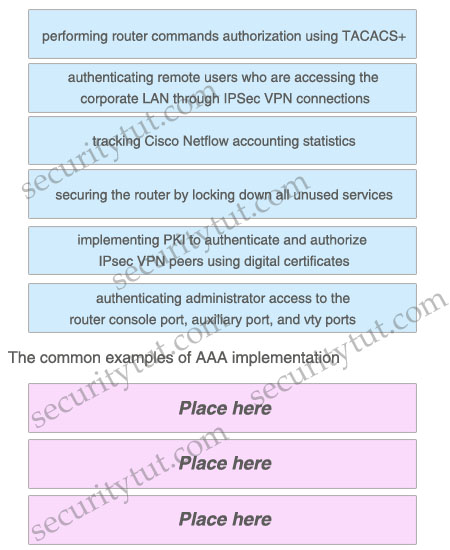
Answer:
+ performing router commands authorization using TACACS+
+ authenticating remote users who are accessing the corporate LAN through IPSec VPN connections
+ authenticating administrator access to the router console port, auxiliary port, and vty ports
Question 3
Drag two characteristics of the SDM Security Audit wizard on the above to the list on the below.
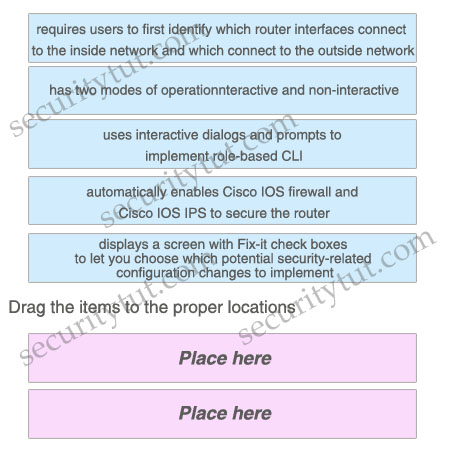
Answer:
+ requires users to first identify which router interfaces connect to the inside network and which connect to the outside network
+ displays a screen with Fix-it check boxes to let you choose which potential security-related configuration changes to implement
Question 4
On the basis of the Cisco IOS Zone-Based Policy Firewall, by default, which three types of traffic are permitted by the router when some interfaces of the routers are assigned to a zone?
Drag three proper characterizations on the above to the list on the below.
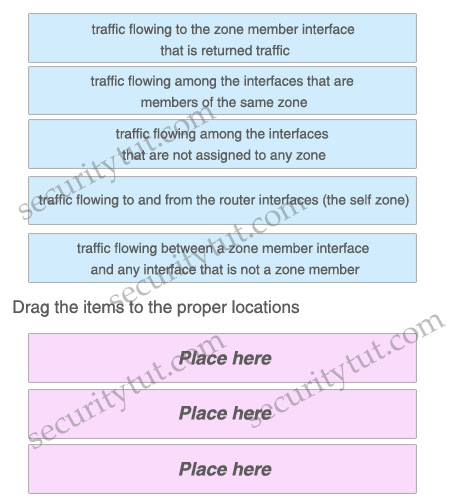
Answer:
+ traffic flowing among the interfaces that are members of the same zone
+ traffic flowing among the interfaces that are not assigned to any zone
+ traffic flowing to and from the router interfaces (the self zone)
Question 5
Drag three proper statements about the IPsec protocol on the above to the list on the below.
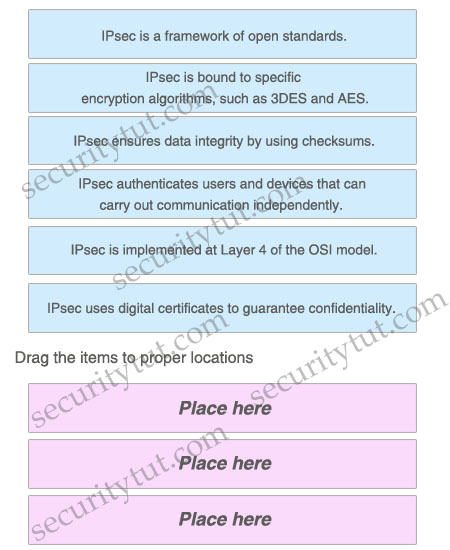
Answer:
Three correct statements are:
+ IPsec is a framework of open standards.
+ IPsec ensures data integrity by using checksums.
+ IPsec authenticates users and devices that can carry out communication independently.

