In this exam we will encounter:
+ 3 Drag and Drop Questions
+ Some Multiple Choice Questions
+ 12 Troubleshooting Tickets (check them at the right-side menu)
Below is a summary of 12 Tickets you will see in the exam:
| Device | Error Description |
| ASW1 | 1. Access port not in VLAN 10 |
| 2. Port Channel not allowing VLAN 10 | |
| 3. Port Security | |
| DSW1 | 1. HSRP track 10 |
| 2. VLAN filter | |
| R1 | 1. Wrong IP of BGP neighbor |
| 2. NAT – Access list mis-configured | |
| 3. Redistribute access-list | |
| 4. OSPF Authentication | |
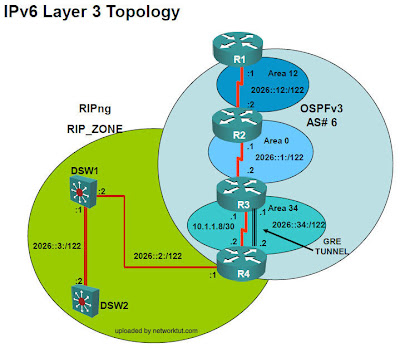
| R2 | 1. IPv6: enable OSPF |
| R4 | 1. EIGRP – wrong AS |
| 2. Redistribute (“to” & -> ) |
Notice that in the exam, the tickets are randomly given so the best way to troubleshooting is to try pinging to all the devices from nearest to farthest from the client until you don’t receive the replies.
In each tickets you will have to answers three types of questions:
+ Which device causes problem
+ Which technology is used
+ How to fix it
One more thing to remember: you can only use “show” commands to find out the problems and you are not allowed to make any changes in the configuration. In fact, in the exam you can not enter the global configuration mode!
Screenshots for your reference:
You can see bigger images below:
Luckily we have a link to download this lab (open it with Packet Tracer v.5.3+) (Thanks Ali and many people for sharing this)
http://www.networktut.com/download/TSHOOT_LAB.pkt
Below is the screenshot of this file
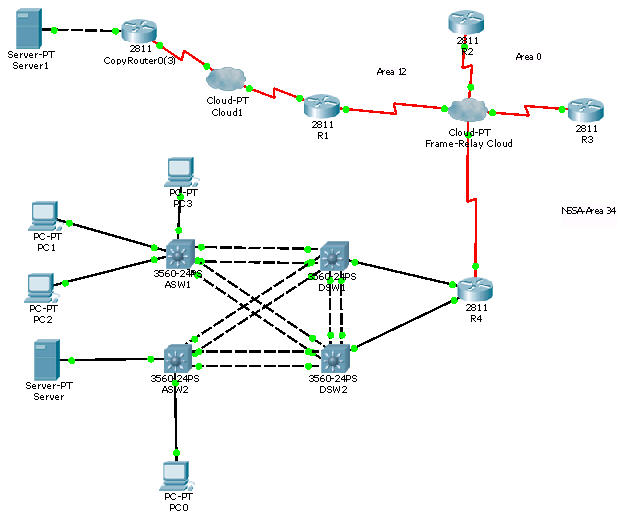
If you have any new information about this exam, please share with us!
Best wishes to those who are going to take this exam!
TO ALL WHO WANT FRESH EXAM INFO,
I PASSED CCNP AND AM SHARING THIS INFO WHICH I APPLIED AND WORKED WELL WITH ME I SCORED 982.
1 > MUST MUST MUST UNDERSTAND ALL THE 3 TOPOLOGIES, THE PROTOCOLS USED AND LOCATIONS OF THE PROTOCOLS, THIS HELPS ALOT DURING EXAM ANS SAVES YOU GR8 AMOUNT OF TIME.
2 > ALWAYS FROM CLIENT THE FIRST THING TO TYPE IS , THEN “PING”. THIS GIVES YOU A CLEAR PICTURE OF WEATHER YOUR SWITCH’S ARE PROPERLY CONFIGURED OR NOT.
3> MUST MUST MUST GO TO CISCO.COM AND PRACTICE 3 – 5 TIMES THE TSHOOT exam DEMO, THIS REALLY REALLY HELPS ALOT AND GIVES YOU A BETTER PICTURE OF HOW YOUR EXAM ENGINE WILL BE, IT EVEN BOOST CONFIDENCE.
4> DONT DONT DONT, WASTE YOUR TIME ON TT’S WHEN YOU ARE STUCK, JUST ABORT THE TICKET AND GO TO THE NEXT TT, ONCE YOU ARE DONE WITH REST OF TT’S THEN GO BACK TO THE ABORTED TT, THIS SAVES YOU TIME, IT WORKED PERFECT WITH ME.
5> ALL TT’S ARE THE SAME AS HERE, WITH MINOR CHANGE’S TO CONFUSE YOU ONLY NOT MORE.
BELOW IS SUMMARY OF TT I ADVICE ALL TO READ AND UNDERSTAND.
1TT has ipv6 proof of concept.
R2 OSPFv3 fault, “ipv6 ospf 6 area 0″ is not enabled on int s0/0/0/0.23
1TT tells DSW1 does not become active
Ans1) R2
Ans2) OSPFv3
Ans3) on the serial interface of R2, enter the command ipv6 ospf 6 area 0 (notice that it is “area 0″, not “area 12″)
DSW1 HSRP fault, int vlan 10 should have “standby 10 track 10 decrement 60″ instead of
“standby 10 track 1 decrement 60″
Ans1) DSW1
Ans2) HSRP
Ans3) delete the command with track 1 and enter the command with track 10 (standby 10 track 10 decrement 60).
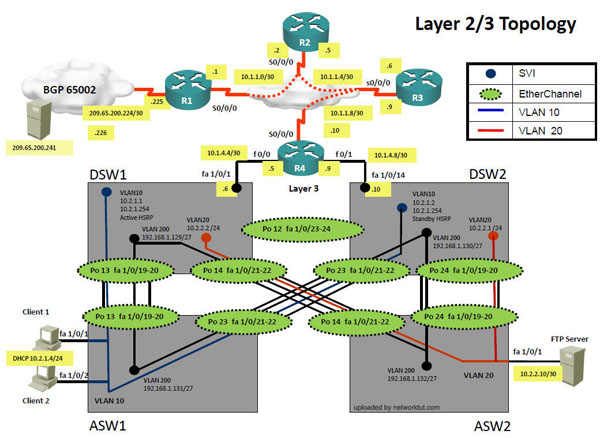
10TTs out of 12TTs tell Client 1 cannot ping Web Server 209.65.200.241
1. Check Client 1, if IP is 169.x.x.x, then ASW1 fault.
1a. Check ASW1, if “port-security mac address” enable on int f1/0/1 -2.
Then port-security fault
Ans1)ASW1
Ans2)Port security
Ans3)issue “no switchport port-security mac-address 0000.0000.0001 command followed by shutdown & no shutdown commands on port fa1/0/1 on ASW1
1b. Check ASW1, if “port-channel 13 and 23″ does not have sw tr allowed vlan 10,200
Then switch-to-switch connectivity fault
Ans1)ASW1
Ans2)Switch to switch connectivity
Ans3)int range portchannel13,portchannel23
switchport trunk allowed vlan none
switchport trunk allowed vlan 10,200
1c. Check ASW1, if int f1/0/1 -2 do not have “sw acc vlan 10″
Then vlan access fault
Ans1)ASW1
Ans2)Vlan
Ans3)give command: interface range fa1/0/1-/2 & switchport access vlan 10
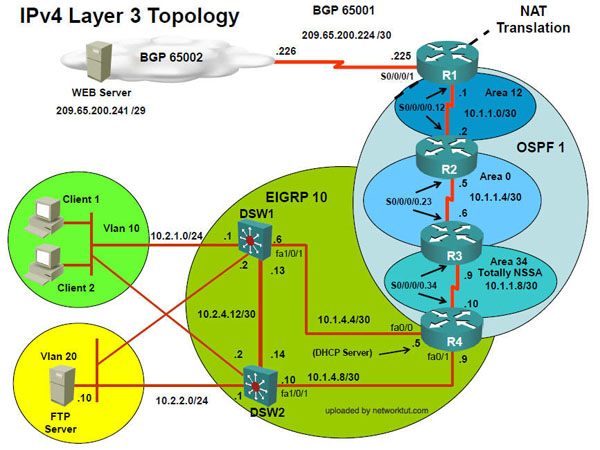
2. Check Client 1, and Client 1 has IP address 10.2.1.x
Faults can be DSW1, R4, R1. Want to know how to check ???
2a. Client 1 ping 10.2.1.1 failed
Check DSW1: VACL configuration, “vlan filter test vlan-list 10″ deny Client 1 IP to DSW1.
Ans1) DSW1
Ans2) Vlan access map
Ans3)Remove vlan filter test1 from DSW1
2b. Client1 ping 10.2.1.1 success
Client1 ping 10.1.4.5 failed
Check R4: EIGRP AS 1 fault
Ans1) R4
Ans2) EIGRP
Ans3) Change EIGRP AS number from 1 to 10
2c. Client 1 ping 10.2.1.1 success (VACL is not configured in DSW1)
Client 1 ping 10.1.4.5 success (R4′s EIGRP nei with DSW1 is ok)
Client 1 ping 10.1.1.9 failed (R4 Route Redistribution from OSPF_to_EIGRP fault)
Check R4, route-map wrong spelling
Ans1) R4
Ans2) Route redistribution
Ans3) Change the name of the route-map under the router EIGRP or router OSPF process from ‘EIGRP_to_OSPF’ to ‘EIGRP->OSPF’.
2d. Client1 ping 10.2.1.1 success (no DSW1 VACL fault)
Client1 ping 10.1.4.5 success (R4 EIGRP nei and routing exchange wt DSW1 is ok)
Client1 ping 10.1.1.9 success (R4 route redistribution from OSPF to EIGRP is ok,
therefore DSW1 has default route via 10.1.1.9)
Client1 ping 10.1.1.2 success
Client1 ping 10.1.1.1 failed (R1 OSPFv2 authentication no configured)
Check R1, OSPFv2 authentication no configured
Ans1) R1
Ans2) OSPF
Ans3) ip ospf authentication message-digest command must be given on s0/0/0/0.12
2e. Client1 ping 10.2.1.1 success (no DSW1 VACL fault)
Client1 ping 10.1.4.5 success (R4 EIGRP nei and routing exchange wt DSW1 is ok)
Client1 ping 10.1.1.9 success (R4 route redistribution from OSPF to EIGRP is ok,
therefore DSW1 has default route via 10.1.1.9)
Client1 ping 10.1.1.2 success
Client1 ping 10.1.1.1 success (R1 OSPFv2 authentication is configured, sh ip ospf nei)
Client1 ping 209.65.200.226 failed (Can be NAT ACL or edge_security ACL on s0/0/0/1)
R2 ping 209.65.200.226 success (Must be R1 NAT-ACL fault that permit only 10.1.1.0/24 )
Check R1, NAT-ACL need to permit 10.2.0.0/16
Ans1) R1
Ans2) NAT
Ans3) Add the command permit 10.2.0.0 in the nat_pool access-list
2f. Client1 ping 10.2.1.1 success (no DSW1 VACL fault)
Client1 ping 10.1.4.5 success (R4 EIGRP nei and routing exchange wt DSW1 is ok)
Client1 ping 10.1.1.9 success (R4 route redistribution from OSPF to EIGRP is ok,
therefore DSW1 has default route via 10.1.1.9)
Client1 ping 10.1.1.2 success
Client1 ping 10.1.1.1 success (R1 OSPFv2 authentication is configured, sh ip ospf nei)
Client1 ping 209.65.200.226 failed (Can be NAT ACL or edge_security ACL on s0/0/0/1)
R2 ping 209.65.200.226 failed (Must be R1 edge_security ACL on s0/0/0/1)
Check R1, ACL need to permit 209.65.200.224/30
Ans1) R1
Ans2) IP Access list
Ans3) Add permit 209.65.200.224 0.0.0.3 to R1′s ACL
2g. Client1 ping 10.2.1.1 success (no DSW1 VACL fault)
Client1 ping 10.1.4.5 success (R4 EIGRP nei and routing exchange wt DSW1 is ok)
Client1 ping 10.1.1.9 success (R4 route redistribution from OSPF to EIGRP is ok,
therefore DSW1 has default route via 10.1.1.9)
Client1 ping 10.1.1.2 success
Client1 ping 10.1.1.1 success (R1 OSPFv2 authentication is configured, sh ip ospf nei)
Client1 ping 209.65.200.226 success (Not a NAT-ACL or edge-security ACL fault)
Client1 ping 209.65.200.241 failed (R1′s BGP fault)
Check R1, can’t find 209.65.200.240/28 route
These are steps that I use to score 1000/1000. All the best to everyone.
Ans1) R1
Ans2) BGP
Ans3) delete the wrong neighbor statement and enter the correct neighbor address in the neighbor command (change “neighbor 209.56.200.226 remote-as 65002″ to “neighbor 209.65.200.226 remote-as 65002″)
Hope it fill help you guys…