Hierarchical Model
-
Fault-tolerant Model
-
Security Model
While designing networks, the first task is to collect and analyze customer’s current needs and future requirements. After a thorough study of the customer’s requirements is performed, the next task is to select the appropriate network topology. There are three different types of network topology models: the hierarchal, fault-tolerant, and secure models. An organization should select an appropriate topology model to help optimize various network concerns such as scalability, efficiency, adaptability, security, and dependability.
Hierarchical Model
A hierarchy helps you to summarize a complex collection of details in an understandable structure. All of us have encountered the meaning of hierarchy in our lives—at home or work. The hierarchical system at work directs you to follow the instructions of your boss or give instructions to your subordinates.
For example, any larger organization has a CEO at the top of the hierarchy. The Sales, Operations, and HR managers function at the second level of the hierarchy. These managers delegate responsibility to their individual teams. This results in smooth functioning of the entire organization. As a result, the organization has the CEO as the strategic head, the Sales, Operations, and HR managers to organize workflow, and the remaining employees involved in day-to-day operations of their respective departments.
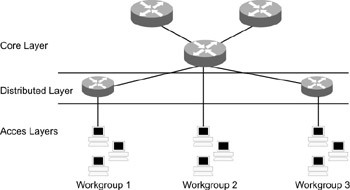
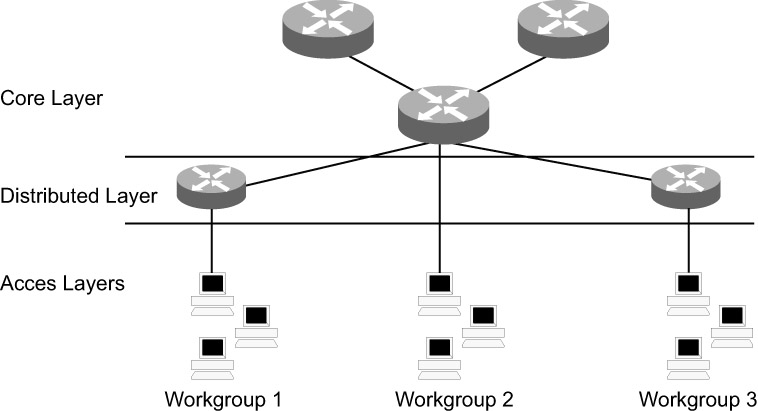
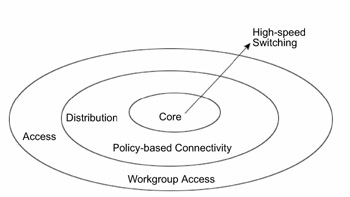
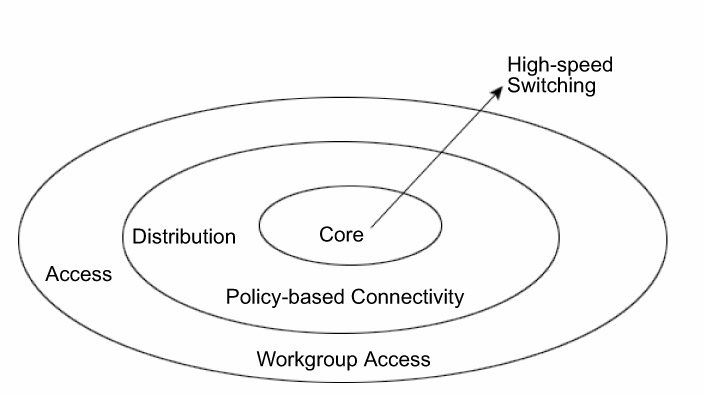
The three layers of the Cisco hierarchical model are core, distribution, and access. The core layer is the topological center of the network and provides high-speed switching, redundancy, high availability, and bandwidth to traffic passing through it. It does not process or route any packets. The distribution layer is responsible for packet filtering and routing. The core layer provides high density and processing capacity-per-interface for packet manipulation. The access layer is the outermost layer and enables end users of the network to connect to each other.
This segmentation of the network into layers is logical, not physical. Each layer performs a specific set of tasks. The functions of these layers may overlap during a physical implementation of a hierarchical network.
The hierarchical model has been designed on the premise that the volume and patterns of network traffic impact network performance. As a result, the three layers have been designed to efficiently manage network traffic, reduce the network load, and increase scalability.
A hierarchical model is designed to enable high-speed data transmission. For example, a financial organization that provides speedy money transfers to its customers opts for the hierarchical model. If you need to wait a half an hour to complete an online transaction with your bank, you will consider that poor service. Therefore, banks and other financial organizations adopt the hierarchical model.
When designing and implementing the network, ensure that the layers are placed such that the traffic is efficiently forwarded between layers. This is because the network rejects any unnecessary packet that a lower layer forwards to an upper layer; that decreases the upload time. Figure 3.1 depicts the core, distributed, and access layers of the Cisco hierarchical model.
The Core Layer
The core or backbone layer is at the top of the hierarchical model and forms the crux of the entire network. This layer is a high-speed switching backbone that transports large volumes of traffic reliably and quickly. It provides wide area connections and moves large payloads between geographically distant sites. The traffic transported across the core is between end users and enterprise services. The links in the core layer are point-to-point.
| Note | Examples of enterprise services are the Internet and e-mail. |
The core layer is responsible only for providing high-speed transport. As a result, there is no room for latency and complex routing decisions pertaining to filters and access lists. These are implemented at the distribution layer. Therefore, protocols with fast convergence times are implemented at this layer. Quality of Service (QoS) may be implemented at this layer to ensure higher priority to traffic that may otherwise be lost or delayed in congestion.
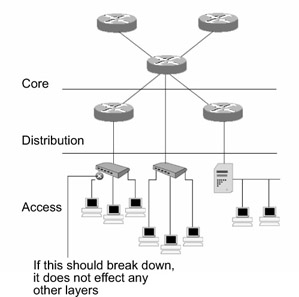
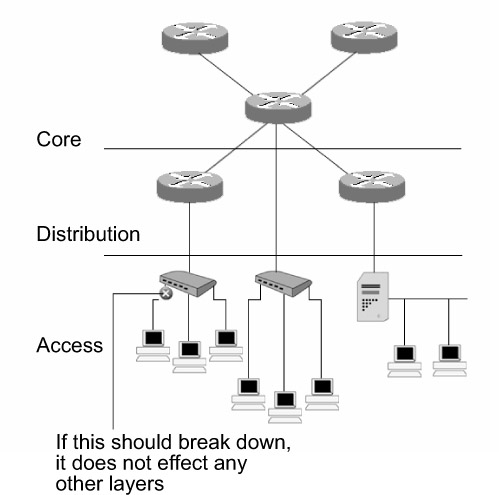
The core layer should have a high degree of redundancy. This is because if there is a breakdown in the core layer, it will adversely affect the entire network. For example, referring to Figure 3.1, if the core layer router fails, the routers in the distribution layer and the workgroups in the access layer will be affected. If redundancy is incorporated, an alternate path is used to transport data in case of any failure in the active path.
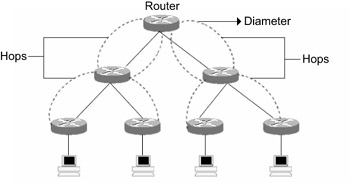
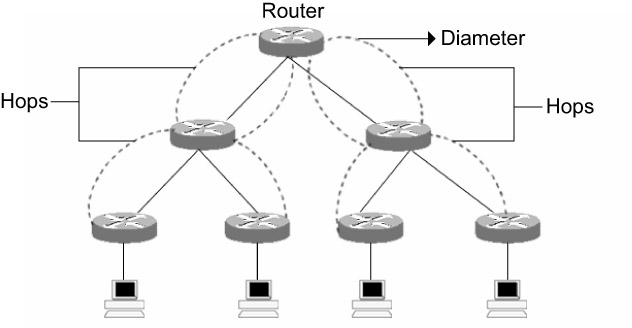
The performance of the core layer also depends on the diameter of the network design. The number of hops from one edge router to another edge router is called the diameter. The diameter within the hierarchical network should remain consistent for good performance of the core layer. This means that the distance from any end station to another station should be equal. Any changes in the diameter would result in irregular movement of data, which results in problems such as over-utilization of a few nodes, frame delays, and data loss. Therefore, the overall performance of the core and hierarchical layers deteriorates. The consistency of the diameter in the core layer is depicted in Figure 3.2.
The core layer implements the following functions:
-
High-speed switching of large volumes of traffic
-
High network availability and reliability
-
Load sharing
-
Rapid convergence
-
High bandwidth availability
-
Low latency
Table 3.1 depicts the do’s and don’ts to be kept in mind when implementing the core layer.
| Do | Don’t |
|---|---|
| Use Fast Ethernet, Asynchronous Transfer Mode (ATM), and Fiber Distributed Data Interface (FDDI) | Use Access Control Lists (ACLs) |
| Use routing protocols with lower convergence time | Implement Virtual Local Area Network (VLAN) routing and packet filtering |
| Use fast and redundant data link connectivity | Expand the layer |
| Maintain consistent diameter | Implement work group access |
The Distribution Layer
The distribution or policy layer is placed between the access and core layers. This layer implements network policies and controls network traffic and data movement. In addition, it performs complex, CPU-intensive calculations pertaining to routing, filtering, inter-VLAN routing, ACLs, address or area-aggregation, and security, and identifies alternate paths to access the core. The distribution layer also determines the best possible path to forward end-user requests to the core layer. The core layer then transports end-user requests and responses to and from enterprise services.
Members of this layer include most local servers on the LAN, routers, and backbone switches. Various features are associated with the distribution layer, as follows:
-
Access lists and QoS
-
Packet filtering and queuing
-
Redistribution of routing protocols
-
Inter-VLAN routing
-
Broadcast and multicast domain definition
-
Address or area aggregation
-
Departmental or workgroup access
-
Redistribution between routing protocols
-
Load balancing
-
Router summarization and route filtering
-
Security and network policies
-
Address translation and firewalls
-
Controlled access to core layer resources
The Access Layer
The access or workgroup layer is the outermost layer of the Cisco hierarchical model. On this layer, all end users are connected to the LAN. The end-user workstations and local resources such as printers are placed at this layer. Routers serve as gatekeepers at the entry and exit to this layer and ensure that the local server traffic is not forwarded to the wider network. The access layer controls user and workgroup access to internetwork resources. Other functions performed on this layer are sharing and switching of bandwidth, MAC-layer filtering, and micro segmentation.
The features associated with the access layer are:
-
Access control lists
-
Traffic filtering
-
Segmentation
-
Workgroup connectivity with the distribution layer
-
Creation of separate collision domains
-
Static routing
-
MAC-layer filtering
-
Switching and sharing of bandwidth
-
Dial-on-Demand Routing (DDR) and Ethernet switching
Table 3.2 shows the functions of the three layers of the hierarchical model.
| Layer | Functions |
|---|---|
| Core layer |
|
| Distribution layer |
|
| Access layer |
|
Figure 3.3 depicts the three layers of the hierarchical model along with their key functions.
Benefits of the Hierarchical Model
An ideal network should provide optimal bandwidth utilization, efficient management of network traffic, and maximum uptime. Keeping these factors in mind, Cisco introduced the hierarchical design model. This model enables you to design a scalable, reliable, and cost-effective hierarchical internetwork. The benefits of a hierarchical model of network topology are in the following areas:
-
Manageability
-
Performance
-
Cost
-
Scalability
-
Speed
Manageability
Networks based on the hierarchical model are easy to manage, troubleshoot, and support. The functions of the three layers are exclusive to their individual layer, and as a result, it is easy to determine and isolate problems within each layer. If there is an error in the functioning of a workstation or network device at any of the three layers, it is easy to diagnose and troubleshoot without disturbing the other layers. For example, if a workstation placed at the access layer fails, you can easily troubleshoot without disturbing other layers. Figure 3.4 depicts the manageability of a hierarchical design.
Performance
Networks based on a hierarchical model are efficient in performance because of the use of advanced routing features such as route summarization. This feature enables availability of small routing tables and faster convergence in large networks, thereby improving network service.
Cost
Because of its simple design, the hierarchical model offers benefits such as cost efficiency and ease of manageability. Bandwidth sharing with the layers of a WAN results in a decrease in costs and also requires less administration.
Scalability
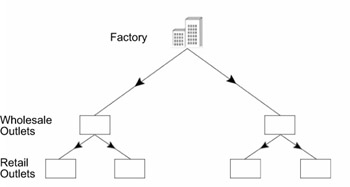
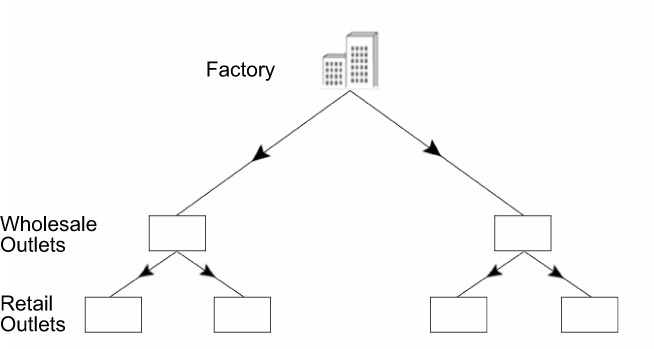
The hierarchical model is easy to scale as compared to other network architecture models because it is divided into modules. As a result, modular expansion is easy and does not affect the rest of the internetwork. The hierarchical model can be compared to a production-based organization, ABCD Company, at which the manufacturing unit is connected to two wholesale outlets, which are connected to four retail outlets. Figure 3.5 depicts the hierarchical structure of the organization.
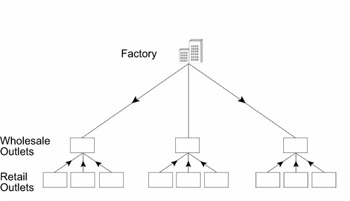
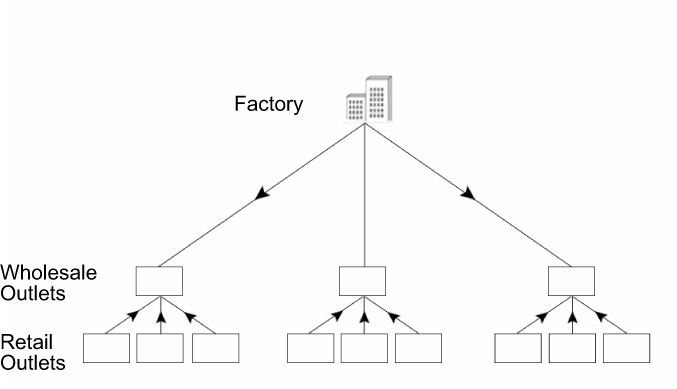
Now, ABCD Company is planning to expand its setup. The hierarchical structure has made it easy to expand the setup at any layer. Figure 3.6 depicts the structure of ABCD after it has undergone expansion.
Similarly, in the hierarchical model, you are not required to change the entire network topology. It is easy to scale and does not require any reconfiguration.
Speed
The hierarchical model makes it possible to provide high-speed switching of data between workstations and internetwork services. This is because all local traffic is resolved at the access layer, and only requests for enterprise services are forwarded to the core layer.
In addition to modularity, route summarization and fast-converging protocols increase the overall speed of network services.