Overview
In today's computing environment, large organizations routinely store and manage huge volumes of data on multiple servers.
Storing the data is easy enough. But making that data continually available – all while keeping costs down and performance up – is a challenge.
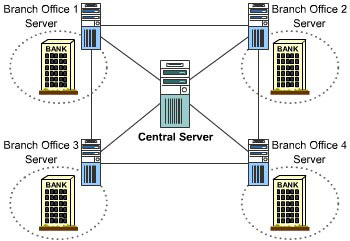
Most Wide Area Networks (WANs) do not address this problem effectively. In the example shown in Figure 1-2-1, a bank’s WAN stores customer account information on four servers, each residing at one of its four branch offices. But to serve customers efficiently, each branch needs continual access to the data on all four servers. Storage Area Networks (SANs) provide an efficient way to make that happen – without having to replicate data.
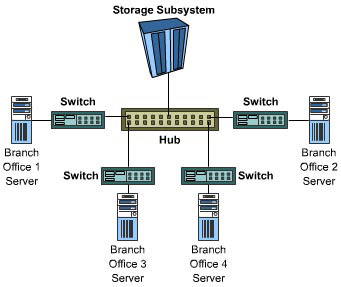
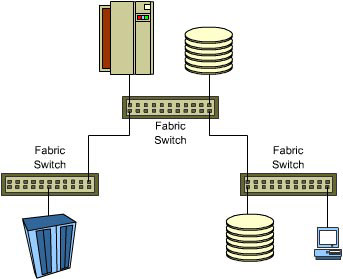
A SAN is a network of networks that separates business applications from business data. The SAN depicted in Figure 1-2-2 consists of a storage subsystem connected to a switch and a hub, which, in turn, are connected to the four servers residing at each of the bank’s branch offices. By storing customer account information at a centralized location, the bank's systems can operate faster and more efficiently. There is no need to replicate data - reducing network traffic significantly.
In SANs, the method used to connect application servers with storage subsystems determines the ease of data storage, data management, and data availability. You can use one of the two connection techniques, a Small Computer Systems Interface (SCSI) or a Fibre Channel.
A SCSI connection is a parallel bus connection in which each network device is connected to a SCSI Host Bus Adapter (HBA). SCSI connections provide high data transfer rates at low cost. However, SCSI connections have the following limitations:
-
When an electrical interruption occurs, the data on a SCSI bus is lost. This places an overhead on the server application, requiring it to retransmit the data.
-
A SCSI connection allows SAN devices to be separated by a maximum distance of 25 meters. To connect remote SAN devices, you need expensive SCSI extenders and repeaters.
-
A single SCSI HBA can be connected to only seven SCSI devices.
Fibre Channel connections overcome the limitations of SCSI. SAN devices connected by Fibre Channel can be arranged using one of the following three topologies:
In a Point-to-Point topology, a dedicated and direct connection exists between two SAN devices. In an Arbitrated Loop topology, the SAN devices are connected in the form of a ring. In a Switched Fabric topology, SAN devices are connected using a fabric switch. The fabric switch allows a SAN device to connect and communicate with multiple SAN devices simultaneously.
Point-to-Point Topology
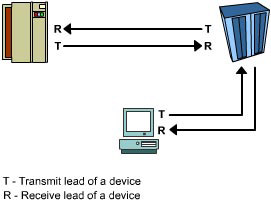
In this topology, the transmit and receive leads of a SAN device are connected to the receive and transmit leads, respectively, of its partner device. As a result, a dedicated link exists between the two devices at any point in time, resulting in high data transfer rates. Figure 1-2-3 shows an example of a Point-to-Point connection.
In this topology, before a source device can communicate with a target device, the source device must log on to the network port of the target device by using a logon name and a password. The logon name and the password are set for a network port during the installation of network services on the target device.
In the Point-to-Point topology, a direct connection exists between the devices, and the bandwidth of that connection is dedicated entirely to that transaction. As a result, transactions are fast and relatively error free. But a SAN based exclusively on this topology is expensive. In addition to cost, Point-to-Point topology has the following disadvantages:
-
Although a two-way communication path exists between two devices, only one path can be used at a time. Devices can either transmit or receive, but they cannot do both simultaneously.
-
SAN devices in a Point-to-Point network must be physically connected to communicate with each other.
Arbitrated Loop Topology
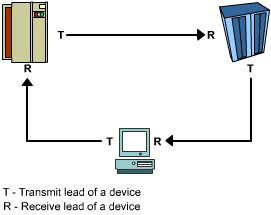
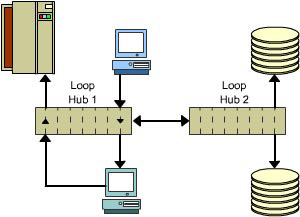
An Arbitrated Loop topology is similar to the ring topology of traditional networks. The transmit lead of one SAN device in an Arbitrated Loop network is connected to the receive lead of its neighboring device. The neighbor’s transmit lead is, in turn, connected to the receive lead of yet another NL_Port and so on, forming a daisy chain, as shown in Figure 1-2-4.
| Note | If a device in an Arbitrated Loop topology is connected to the hub, the port to which the device is connected is known as an N_Port. If an Arbitrated Loop is connected to the hub, the port to which the Arbitrated Loop is connected is known as an NL_Port. |
This topology allows more than two devices to communicate simultaneously over a common communication path and is, therefore, the most commonly used topology. But there are certain disadvantages associated with a daisy chain Arbitrated Loop, which are as follows:
-
Powering off or disconnecting a single node in the daisy chain breaks the chain.
-
The communication path and bandwidth are shared between devices. Sharing communication path is an advantage compared to the Point-to-Point topology, but it slows down performance when the number of application hosts requesting access increases.
You can use Fibre Channel hubs to overcome the disadvantages of daisy chain loops. As depicted in Figure 1-2-5, you can connect the transmit and receive leads of the NL_Ports of all SAN devices to a single hub. A Fibre Channel hub contains the following circuits:
-
A multiplexer circuit that is used to complete the Arbitrated Loop.
-
A bypass circuit that is used to bypass a disabled or disconnected node, without affecting the operations within the loop.
Compared to the traditional ring topology, an Arbitrated Loop topology can support a higher number of nodes. Each Arbitrated Loop can have a maximum of 126 devices and can extend up to 6.21 miles (or 10 kilometers). You can use two or more hubs to build larger cascaded loops, as shown in Figure 1-2-5.
If an Arbitrated Loop is connected to a switch, which is, in turn, connected to several other loops, the formation is known as a public loop. A loop that is not connected to any other loop is known as a private loop.
Arbitrated Port Addressing
A unique port address is used to identify each device on an Arbitrated Loop. An understanding of the concept of port addressing will help you add or remove devices from an Arbitrated Loop.
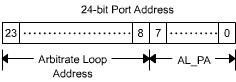
Each device on an Arbitrated Loop is assigned a unique 24-bit port address. The first two bytes represent the loop address in the case of public and private loops. The value of first two bytes is zero in the case of private loops. The third byte represents the address of a particular NL_Port within a loop. Therefore, the first two bytes are referred to as the loop identifier and are same for all NL_Ports within the same loop. The last byte is referred to as Arbitrated Loop Physical Address (AL_PA). Figure 1-2-6 shows the N_Port/NL_Port address components.
The port addressing mechanism can be either static or dynamic. In the case of static port addressing, each NL_Port is assigned a unique port address manually. Static port addressing is difficult to administer because it's easy to inadvertently assign the same port address to two N_Ports, causing port conflicts. Also, it's difficult to remember the port address of all NL_Ports in the case of cascaded loops. As a result, most SANs use dynamic port addressing. In the case of dynamic port addressing, each N_Port and NL_Port is automatically assigned an arbitrary, unique address during the loop initialization process.
The port address is used to set the priority for the SAN devices in an Arbitrated Loop. A device with the lowest port address is serviced first and has the maximum priority within a loop. Normally, valuable SAN resources, such as file servers, fabric loop ports, and switches, are assigned lower AL_PAs.
Arbitrated Loop Operations
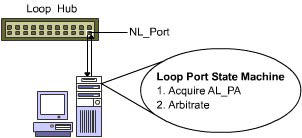
Loop devices in an Arbitrated Loop use Loop Port State Machine (LPSM) to access the network. The LPSM consists of all loop-specific functions that are embedded in silicon or microcode on loop devices. This enables a loop device to:
-
Acquire an AL_PA through the process of loop initialization.
-
Acquire control of the loop path for data transmission through the process of arbitration.
-
Access the loop for transactions.
As shown in Figure 1-2-7, the LPSM interacts with the FC-1 and FC-2 functions. The FC-1 function is responsible for frame management and data flow control. The FC-2 function is responsible for encoding and decoding the data that is transmitted and received over the SAN.
| Note | FC-1 and FC-2 are functions that are embedded in silicon or microcode on loop devices. |
The following sections explain how LPSM is used to perform the following operations in an Arbitrated Loop:
-
Loop initialization
-
Loop arbitration
Loop Initialization
A loop performing a normal loop activity might fail when you add a device to the loop or change the NL_Ports of loop devices. Proper selection of loop devices, such as hubs, storage subsystems, and HBAs, ensures that a loop resumes its normal activity whenever new devices are introduced into the loop. An understanding of the loop initialization process will help you repair loop failures that might occur when you add a device to the loop.
Loop initialization is performed in loops that support the dynamic port addressing mechanism. During this process, an AL_PA is assigned to all devices that are active within a loop. This process is executed whenever any of the following events take place:
-
A new device is added to the loop and requires an AL_PA to be assigned to it.
-
The hub is switched on, and all currently active devices that are connected to the hub require an AL_PA to be assigned to them.
-
The NL_Port of a device is changed.
-
A loop recovers from a failure.
The process of loop initialization takes only a few milliseconds. A loop device circulates one of the byte ordered sets, listed in Table 1-2-1, within a loop when any of the aforementioned events occur. These ordered sets are also referred to as Loop Initialization Primitives (LIPs).
| Ordered Set | Event |
|---|---|
| LIP (F7, F7) | Is circulated by a loop device that is switched on. The first occurrence of F7 indicates that the device is able to recognize itself within the loop. The second occurrence indicates that the device is yet to be assigned an AL_PA. The device circulates this ordered set because it would have lost its AL_PA when it was previously switched off. |
| LIP (F7,AL_PS) | Is circulated when a loop device is moved from one hub port to another. F7 indicates that the loop device is able to recognize itself within the loop. AL_PS specifies the loop address that was previously assigned to the device. The device circulates this ordered set to indicate that a topology change has occurred within the loop. |
| LIP (F8,F7) | Is circulated when the receiver of an HBA to which a loop device is connected fails. F8 indicates a loop-down state, and F7 indicates that the device must be assigned an AL_PA. The device circulates this message when it is switched on. |
| LIP (F8,AL_PS) | Is circulated when the receiver of an HBA to which a loop device is connected fails. F8 indicates a loop-down state, and AL_PS specifies the loop address that was previously assigned to the device. The device circulates this message if it was active when the failure occurred. |
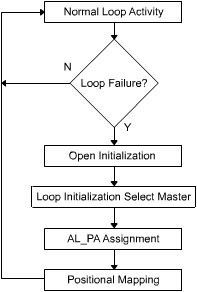
The loop initialization process is triggered when a loop device circulates an ordered set at least 12 times onto the loop. Figure 1-2-8 illustrates the sequence of activities that are performed during the loop initialization process.
Open Initialization
When loop devices receive one of the ordered sets listed in Table 1-2-1, they enter the Open_Init state. The device suspends all current operations and prepares itself for the loop initialization process.
Loop Master Selection
When all devices within the loop reach the Open_Init state, one of the devices needs to be assigned as the temporary loop master. The temporary loop master is responsible for carrying out the rest of the loop initialization process.
A Loop Initialization Select Master (LISM) procedure is used to determine the device that will act as the temporary loop master. The following sequence of steps determine the temporary loop master:
-
Each loop device circulates an LISM frame that contains the port address and the World Wide Name (WWN) of the device.
-
The neighboring loop device picks up the LISM frame from the loop and compares the WWN of the LISM frame with its own WWN. The neighboring device also checks whether the port address on the LISM frame is a valid FL_Port.
-
If the port address on the LISM is greater than its port address, the neighboring device puts the LISM frame back into the loop.
-
If the port address on the LISM is less than its own port address, the neighboring device replaces the port address on the LISM frame with its own port address and puts back the modified LISM frame into the loop.
The preceding sequence of steps is repeated until all devices circulate the same LISM frame within the loop. Therefore, a loop device gets back its own LISM frame, indicating that it has the maximum priority within the loop. This loop device then acts as the temporary loop master. The loop master circulates a special ordered set, ARB (F0), to notify the other devices about the completion of the LISM procedure.
AL_PA Assignment
The purpose of the loop initialization process is to assign an AL_PA to each of the loop devices. The temporary loop master circulates a set of four frames that are used to assign unique AL_PAs to each of the loop devices. Each frame consists of the following:
-
An address map of all possible 4-bit AL_PAs that can be assigned to the devices within the loop
-
A header that defines which of the loop devices are allowed to select an AL_PA from the frame
-
A status bit for each AL_PA that specifies whether or not an address has been assigned to any of the loop devices
The following sequence of steps explains how to assign an AL_PA to a loop device:
-
The loop master circulates a Loop Initialization Fabric Address (LIFA) frame. This frame allows all public loop devices that were assigned an AL_PA during the previous loop initialization process to select an AL_PA from the list. The public loop devices select the AL_PA that was previously assigned to them from the LIFA frame.
-
After the loop master receives the LIFA frame back, it circulates a Loop Initialization Previous Address (LIPA) frame. This frame allows all private loop devices to select the AL_PA that was previously assigned to them from the address map.
-
After the loop master receives the LIPA frame back, it circulates the Loop Initialization Hard Address (LIHA) frame. This frame allows all NL_Ports that have a Dual In-Line Package (DIP) switch or a jumpered address to select an AL_PA from the address map.
-
After the loop master receives the LIHA frame back, it circulates the Loop Initialization Soft Address (LISA) frame. This frame allows all loop devices that are yet to be assigned an AL_PA to select an AL_PA from the address map.
Positional Mapping
According to Fibre Channel standards, the loop initialization process terminates after the AL_PA assignment is complete. Recently, vendors that support Fibre Channel have incorporated an additional positional mapping subroutine in their products. The position mapping subroutine is used to determine how devices are organized within the loop topology. Positional mapping is used for diagnostic purposes and fine-tuning loop configuration.
Positional mapping involves the following steps:
-
The temporary loop master circulates a Loop Initialization Report Position (LIRP) frame within the loop.
-
Each loop device picks up the LIRP frame, appends its own AL_PA to the frame and puts the LIRP frame back onto the loop.
-
After the temporary loop master receives the LIRP frame back, it recirculates the frame within the loop.
-
Each loop device copies the LIRP frame.
The loop initialization process terminates after the positional mapping process is complete. The loop master indicates the completion of the loop initialization process by circulating the close (CLS) and IDLE frames within the loop. When each loop device receives the CLS frame, it moves out of the Open-Init state and resumes normal activity. The IDLE frames are circulated within the loop until a new communication process is triggered.
Loop Arbitration
A loop device must gain access to the loop before it can communicate with another loop device. Arbitration is the process by which a loop device determines if the loop path is free for it to communicate and gain control of the loop. A loop device is allowed to access the loop path according to the following factors:
-
Priority of the loop device’s AL_PA
-
The status of an access variable that is stored in the LPSM of a loop device
Gaining Loop Access Based on Loop Priority
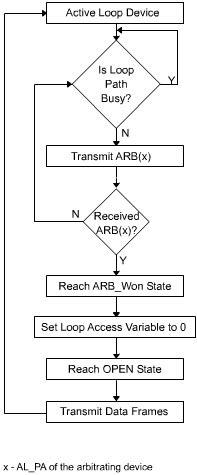
A loop device performs the following sequence of steps to gain access to the loop path:
-
The loop device checks to see if the loop path is busy.
-
If the loop path is not busy, the device transmits an ARB(x) ordered set that contains its own AL_PA. The device transmits an ARB(x) ordered set even if another device currently owns the loop path. However, if frames are currently traversing the loop path, ARB(x) is issued only between two successive frame transmissions.
-
ARB(x) circles the loop and reaches the loop device that arbitrated, indicating that the loop path is free for data transmission. Then, the arbitrating loop device reaches the ARB_Won state and a subsequent OPEN state and is ready for data transmission.
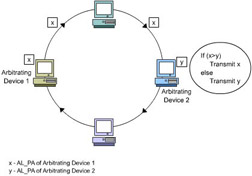
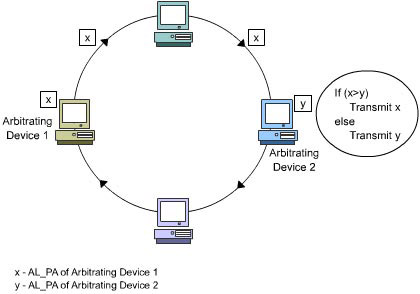
As shown in Figure 1-2-9, if two or more devices arbitrate simultaneously, each of the arbitrating devices receive the ARB(x) ordered set that was sent by its neighboring arbitrating device. The arbitrating devices then compare the AL_PA on the received ARB(x) with its own AL_PA. If the priority of the AL_PA on the received ARB(x) is greater, it puts the ordered set back onto the loop. If the AL_PA on the received ARB(x) has a lower priority, neighboring arbitrating device replaces the AL_PA with its own AL_PA and puts the modified ARB(x) ordered set back onto the loop.
A loop device wins an arbitration process if it receives back the ARB(x) ordered set that it transmitted. In addition, if two or more devices arbitrate simultaneously, an arbitrating loop device that has the greatest priority wins the arbitration. Figure 1-2-10 shows the steps involved in gaining loop access based on loop priority.
| Note | An IDLE frame is transmitted over the loop path if the loop path is not being used by any other device and is free for data transmission. |
Gaining Loop Access Based on the Status of the Loop Access Variable
As mentioned earlier, high priority devices win the arbitration process. This keeps low priority devices from gaining loop access. Loop access variables are used to ensure that low priority devices also gain access to the loop path.
When a loop device wins an arbitration process, the loop access variable on its LPSM is set to zero. The device cannot arbitrate again as long as its access variable is zero. To win a subsequent arbitration, a loop device performs the following steps:
-
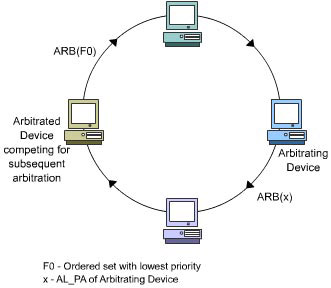
After a loop device wins an arbitration for the first time and completes data transmission, it transmits an ARB(F0) ordered set onto the loop. ARB(F0) has the lowest priority.
-
If no other device is currently arbitrating, the loop device receives back the ARB(F0) that it transmitted. This indicates that the loop path is free, and no other device requires access to the loop path. Then, the state of the loop access variable on the loop device, which is currently competing for a subsequent arbitration, is set to one.
-
On the other hand, if another device starts arbitrating, it picks up the ARB(F0) ordered set from the loop, attaches its own AL_PA, and puts the modified ARB(x) onto the loop. As a result, the loop device, which is currently competing for a subsequent arbitration, does not receive the ARB(F0) that it transmitted.
Figure 1-2-11 depicts the process of gaining loop access based on the status of loop access variables.
Loop Topology: SANs and LANs
In the case of token ring and Ethernet LAN topologies, data is sent over the loop to all devices because all devices share the loop path. Each device that senses that a frame is being transmitted across its loop, picks up the frame and checks to see if the Media Access Control (MAC) address on the frame matches its own MAC address. If the MAC addresses match, the device picks up the data from the frame and puts back an empty frame onto the loop. As a result, transmissions on the loop are visible to all loop devices.
In the case of Arbitrated Loops, transmissions on the loop are not visible to all loop devices. When a loop device wins arbitration, it starts transmitting a series of frames to the destination device. The intervening loop devices in the path between any two communicating devices simply forward the frames onto the loop and do not remove or retransmit the frames. The destination device removes the frames from the loop and puts back a R_RDY or CLS frame onto the loop, which, in turn, is circulated back to the source device. The R_RDY frame indicates to the source device that the destination device is ready to receive the next frame. The CLS frame indicates that the data transmission is complete.
The non-broadcast feature, which does not transmit data to all devices, of SANs provides the following advantages:
-
Transmits data at high speed.
-
Prevents hackers from tampering with the frames that are transmitted over the loop.
-
Removes the frame-handling overhead because separate code must be embedded onto each loop device for processing mismatched MAC addresses.
In case of Ethernet and token ring LANs, where data transmissions are visible to all loop devices, it is easy to identify which network device is the source of network traffic. Plugging a product, such as Network Associates Sniffer, at any position within the ring can help do this. However, in case of Arbitrated Loops, you need to move the Sniffer from one port to another for identifying which NL_Port is the source of the network traffic.
f the three.
The arrangement of network devices in the Switched Fabric topology is similar to that of the Arbitrated Loop topology. But in the Switched Fabric topology, devices do not share the network path. For example, in an Arbitrated Loop network with a functional bandwidth of 100 Mbps and 10 nodes, the functional bandwidth per node is equal to 100/10=10 Mbps. Similarly, in a fabric switch with a functional bandwidth of 100 Mbps and 10 nodes, the functional bandwidth per node is equal to 100 Mbps, and the total functional bandwidth of the Fabric network is equal to 100*10=1,000 Mbps.
In the Switched Fabric topology, you use a fabric switch to connect SAN devices. You can also connect multiple fabric switches to form a meshed fabric connection, as shown in Figure 1-2-12.
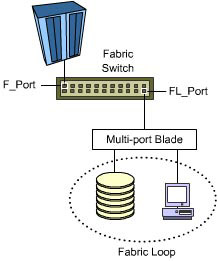
As shown in Figure 1-2-13, you can connect SAN devices to a multiport blade to form a fabric loop. The multiport blade, in turn, is connected to the fabric switch.
| Note | If a device is connected directly to the fabric switch port, the port is referred to as an F_Port. A port that is connected to a fabric loop is referred to as an FL_Port. |
Features of a Fabric Switch
Fabric switches provide various features that help speed up communication within a Fabric network. The following sections explore these features.
Frame Algorithms
Fabric switches use either cut-through or store-and-forward algorithms to route data packets from a source device to a destination device.
The cut-through algorithm is used in fabric switches to speed up packet routing. When a frame enters the fabric switch, the cut-through algorithm examines the destination ID (D_ID) of the frame and routes the frame to the appropriate port. Since the D_ID is present in the frame header, the routing occurs as soon as the frame enters the switch.
In case of switches that use store-and-forward algorithms to route data packets, the entire frame is buffered within the switch before it is routed to the destination device.
Buffering
If a switch receives requests for data transmission from multiple devices simultaneously, regardless of the routing algorithm used, the switch may not be able to route all the data simultaneously. The routing algorithms abandon the frames that they cannot process. In such cases, frames are buffered on the F_Port of the switch to which the transmitting and receiving devices are connected – enhancing the performance of the switch.
Fibre Channel Addressing
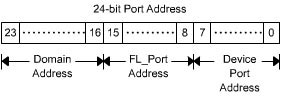
The N_Ports on the fabric switch to which the network devices are connected are assigned a unique 24-bit address. As shown in Figure 1-2-14, the first Most Significant Bit (MSB) refers to the domain address, which is the address of the fabric switch to which the device is connected. The second MSB refers to the FL-Port address, which is the address of the fabric loop on which the device is present. The third MSB refers to the F-Port address, which is the address of the port to which the device is connected.
Support for Alternate Paths
In the meshed topology, multiple paths to a particular destination device might exist. In such cases, the routing algorithm in the switch saves all optimum routes to a particular device. Saving alternate paths within the switch ensures that a frame reaches the destination device even if the primary path fails.
Although fabric switches are costly, the 24-bit addressing mechanism and high-speed data transmission supported by fabric switches enable you to build complex, enterprise wide SANs.
Services Offered by a Fabric Switch
Fabric switches offer the following services to detect and respond to topology changes:
-
Fabric Logon (FLOGI) service
-
Simple Name Server (SNS) service
-
State Change Notification service (SCNS)
The algorithms that implement the above services are programmed within the fabric switch.
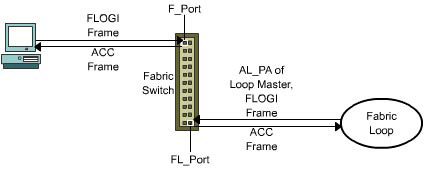
Fabric Logon (FLOGI) Service
A device that is connected to a fabric switch must log on to the fabric to interact with other devices on the fabric network. To perform a fabric logon, the device sends a FLOGI frame to the switch. The FLOGI frame consists of the following information:
-
Node name of the device
-
WWN of the device
-
Services that the device provides to other network devices
-
Services of other network devices that will be utilized by the device
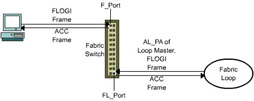
The FLOGI frame is sent to the address xFFFFFE, which is the address of the fabric switch. If the details sent by the device are valid, the switch sends back an acknowledgement (ACC) frame to device. The D_ID field in the FLOGI frame consists of the 24-bit port address assigned to the device by the switch.
In the case of a fabric loop that is connected to a fabric switch, the node that links the loop to the fabric switch is known as the loop master. When the fabric loop initializes, the loop master is assigned a unique AL_PA. The loop master controls all interactions between the nodes in the fabric loop and the nodes connected to the fabric switch. A node in the fabric loop can interact with another node connected to the fabric switch only if the loop master logs on to the fabric switch. The loop master sends its AL_PA before it sends a FLOGI frame to the switch.
Figure 1-2-15 illustrates how fabric logon occurs in the case of F_Ports and FL_Ports.
Simple Name Server (SNS) Service
In the case of Arbitrated Loops, a source device detects the destination device by logging on to the port of the destination device. This process takes a long time when the number of communications within the loop is large. In addition, the source device is unaware of the services offered by the loop devices. Name Server is used in fabric loops to overcome this problem.
Name Server is a database of objects, which contains the following information about the devices connected to the fabric switch:
-
24-bit port address
-
64-bit port names
-
Class IDs of all services offered
-
Protocols supported
-
Port type
-
IP address (in case the device supports IP addressing)
To access the Name Server, the devices connected to a fabric switch transmit a FLOGI frame to the xFFFFFC address. The FLOGI frame contains the values for some or all of the database object parameters listed above. Source devices use this database to identify the location of a destination device or to query the services offered by a particular device.
| Note | The port type can be either N-type or NL-type. The port type is N-type for devices that are connected to the switch directly and NL-type for a fabric loop that is connected to the switch. |
State Change Notification Service (SCNS)
The SCNS is used to track topology changes and notify devices connected to the switch about such changes. The State Change Notification (SCN) and Registered SCN (RSCN) algorithms are used to implement this service. The SCNS is a voluntary service. Network devices must register themselves with these services to be notified of topology changes.
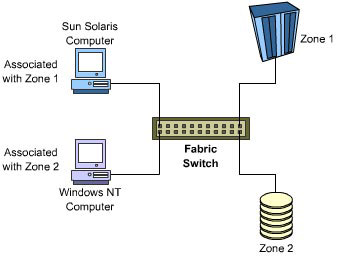
Fabric Zoning
Fabric zoning refers to the process of grouping devices on a Fabric network. It is used to:
Segregate devices that are accessed by a particular operating system. You can group storage devices based on the operating system they access. You can then associate these groups with a computer that hosts the respective operating system by which they are grouped. This will help avoid access conflicts between operating systems.
-
Segregate crucial data. You can group storage devices that contain critical business data and associate these groups with specific servers that modify the data. This will help prevent access to critical data from unauthorized network computers.
Fabric zoning can be implemented in one of the following ways:
-
Port-based zoning: In this, you first assign a group name to the storage devices that you wish to group. Then, you associate the group names with the port addresses of the computers that will access these groups. You perform this association on a router. Figure 1-2-16 depicts a sample port-based zoning.
-
Address-based zoning: In this, you first assign a 24-bit port address to each of the storage groups that you create. Then, you associate the group address with the port address of the computers that will access the groups. This type of zoning requires a dedicated server to be configured to keep track of address associations and monitor group access.
omputing environment, not only most business applications store and manage huge volumes of critical data, they also demand the ability to transmit and retrieve that data at high speeds. Most business applications and virtually all Internet applications rely on SANs to do that. The topology you choose for your company’s SAN plays a key role in carrying out business.
To figure out which topology – Arbitrated Loop or Switched fabric – is best suited to your company’s SAN, you need to take the following factors in account.
Distance Consideration
In Arbitrated Loop networks, the number of devices connected to the loop and the distance between the devices determines the circumference of the loop. With an increase in the circumference of the loop, there is a delay in data propagation and decrease in signal strength. Business applications have reported a 40 percent reduction in performance with an increase in the loop circumference and an increase in the number of communicating devices.
In the case of the Switched Fabric topology, the source and target devices communicate directly and data does not circulate through the entire network. Therefore, the Switched Fabric topology is best suited for enterprise-wide SANs that span remote locations.
Heterogeneous Operating System Environment
Switched Fabric topology offers better support for a heterogeneous operating system environment than Arbitrated Loop. For example, when a Windows NT computer on a SAN is switched on, the Windows NT Disk administrator detects and identifies all storage media available on the network. If a drive is not formatted using Windows NT, the Windows NT Disk administrator prompts you to assign a volume label to it. If you inadvertently choose to assign a volume label, Solaris systems cannot access the drive and all data on the drive is lost. Arbitrated Loops do not address this issue in any way. The Switched Fabric topology supports fabric zoning, which helps you segregate different operating system devices and hosts.
Management Services Offered
Multiple applications hosted across different computers on the network might require data to be simultaneously read and written to a drive. At this point of time, Arbitrated Loop hubs and fabric switches do not provide support for file locking, file access permission auditing, and file encryption. To use these management services, you must install middleware on storage devices that hold these applications. Currently, Arbitrated Loop hubs and fabric switches that support enclosure, multiprotocol, analyzer-type, and enhanced port services have been developed.
Support for Tape Backup Media
Tape drives connected to the network through SCSI ports require backed up data that must be transmitted to the tape device without interruption. An interruption in data transmission to the tape device aborts the backup process. In Arbitrated Loops in which two or more devices communicate simultaneously, interruptions occur in the form of LIPs. However, in fabric switches, multiple paths exit for communication between host servers and backup devices. In addition, intermittent devices between host servers and backup devices do not pick up data packets that pass by their way. Direct communication occurs between two devices in Switched fabric networks.
Private and Public Loops
For SANs that work with a maximum of five to seven servers and several disk arrays, using Arbitrated Loops to build private loops is more economical than using fabric switches. On the other hand, for SANs that need to connect to remote networks and require higher bandwidth, Switched Fabric topology is a better option.
When using the Switched Fabric topology, keep in mind that it is mandatory for HBAs, disks, and other loop devices to support that topology. The private loop devices cannot communicate over the fabric. This is because private loop devices do not log on to a fabric and use LIPs.
Some vendors, such as Brocade and Vixel, have integrated FL_Ports onto their switches. These switches receive and process LIPs from private loop devices without disrupting other devices on the fabric. By using such switches, it is possible to support the hub’s private loop functionality without compromising on the functionality of the fabric switch’s public loop.
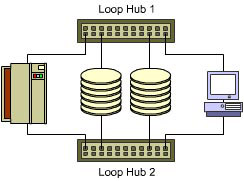
Continuous Data Availability
Most computing environments involve multiple applications accessing data on the same disk drive simultaneously. In that situation, Arbitrated Loop topology is the preferred choice, as shown in Figure 1-2-17. There is more than one path available to access a particular disk drive. Even if one loop fails, data can be routed to the standby loops without disrupting host applications.
A redundant loop configuration in the Arbitrated Loop topology requires redundant transceivers, power supplies, and cables that are costly to implement. Fabric switches contain a routing algorithm that provides support for redundant paths, eliminating the additional cost.
Summary
The key topologies and issues in building a SAN are as follows:
-
Connection techniques: A SCSI connection is a parallel bus connection in which each network device is connected to a SCSI HBA. Fibre Channel connections help you overcome the limitations of SCSI connections, such as the loss of data during electrical interruption and a limit on the number of devices that can be connected to a HBA.
-
Point-to-Point topology: In the Point-to-Point topology, a dedicated link exists between two SAN devices, allowing for high data transfer rates. A SAN that uses only this topology is prohibitively expensive.
-
Arbitrated Loop topology: In an Arbitrated Loop topology, the connection path is shared by the loop devices. Arbitrated Loop hubs that contain multiplexer and bypass circuits are used to connect SAN devices. A unique port NL_Port address is given to each SAN device that is connected to the Arbitrated Loop hub. The loop initialization process is used in this topology to assign an AL_PA to all SAN devices that are active within a loop. Each loop device must arbitrate to determine if the loop path is free for it to communicate and thus gain control of the loop.
-
Switched Fabric topology: In this topology, all the switches that are part of the SAN are interconnected to form a fabric. This topology supports up to 224 nodes. The following features of a fabric switch help in speeding up communications over a Fabric network:
-
Packets are routed by using separate frame algorithms.
-
Frames are queued up to be transmitted in buffers on the F_Port.
-
Alternate paths are supported.
-
-
Fabric switches offer the following services that help detect and respond to topology changes:
-
Fabric Login service
-
Simple Name Server service
-
State change notification service
-
This topology also supports zoning, which is the process of grouping SAN devices.
-
-
Topology comparisons: For SANs that work with a maximum of five to seven servers and several disk arrays, Arbitrated Loop topology is more economical. For SANs that require a high-bandwidth connection to remote networks, Switched Fabric topology offers better performance.