A Storage Area Network (SAN) is a high-speed network of shared storage devices, servers, and clients that help in transferring data. There are various tools, such as NetWisdom and McDATA SANavigator, Xgig Analyzer Suite, and Generators that help in monitoring, analyzing, and testing SAN performance. These tools allow you to maximize SAN performance by reducing the time required for transferring data.
This ReferencePoint describes the features, components, and applications of a SAN. It explains the methods of maximizing SAN performance and discusses the tools available for monitoring, analyzing, and testing SAN performance.
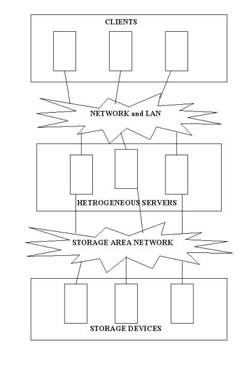
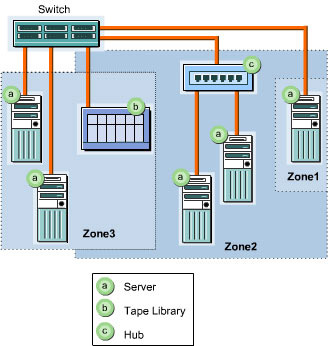
Overview of SANs
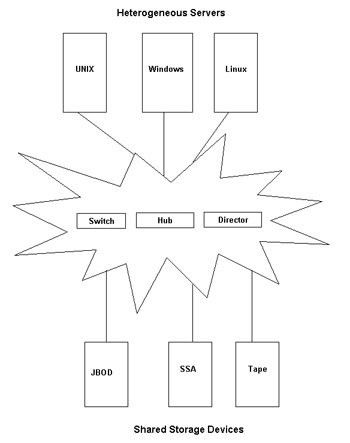
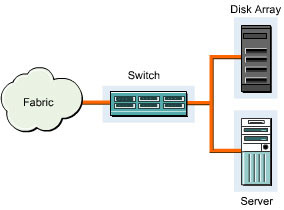
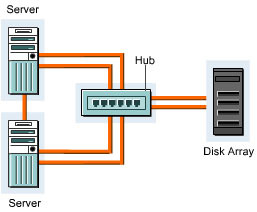
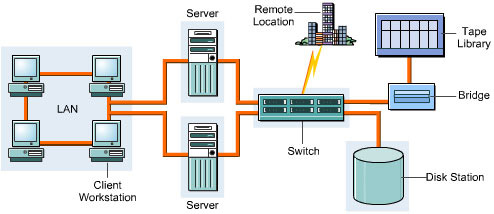
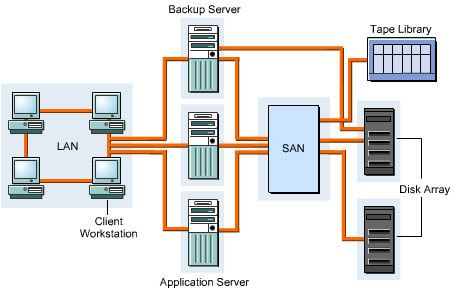
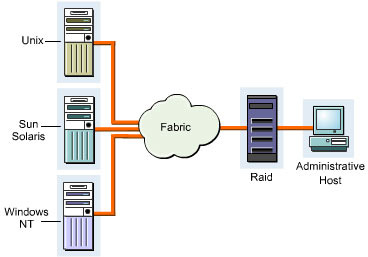
shows the structure of a SAN:
SANs support high-speed data transfer among connected devices, such as servers and storage devices. You can transfer data between servers and storage devices by various ways:
-
Server to Storage: Transfers the data between the servers and storage devices on a SAN.
-
Server to Server: Transfers the data in large volumes between connected servers on a SAN.
-
Storage to Storage: Transfers the data between connected storage devices on a SAN without involvement of the server.
| Note | Multiple servers can access the same storage device on a SAN using parallel data paths. |
Features of SANs
SANs provide various features, such as increased performance, improved and cost effective storage management, and high availability and security of data. A SAN increases the performance of a network by providing the following features:
-
High data bandwidth: Provides high data bandwidth by using devices that can transfer data at the speed of 2 gigabytes per second.
-
Unlimited scalable storage capacity: Helps increase storage capacity by adding unlimited number of storage devices.
-
Improved storage utilization: Helps utilize the storage capacity of storage devices because in a SAN, you can flexibly allocate storage area to different types of data.
-
Globally available storage: Helps all devices to have access to the storage area in the storage devices.
-
Data sharing: Helps multiple devices to access a single file because a SAN provides concurrent reading and writing of data with high-bandwidth data access.
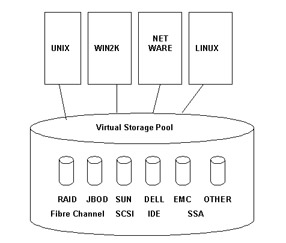
SANs also provide increased and cost effective storage management by using virtual storage management system. In virtual storage management system, servers with different operating systems, such as UNIX, Windows 2000, Netware, and Linux can use the virtual storage pool, which is a collection of different storage devices, such as Integrated Drive Electronics (IDE), Small Computer System Interface (SCSI), Self Storage Association (SSA) and Fibre Channel (FC), to store data
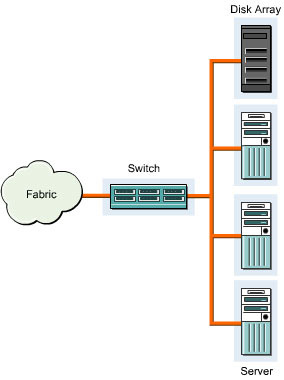
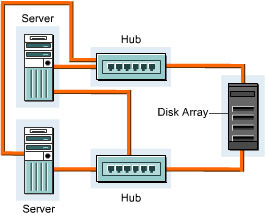
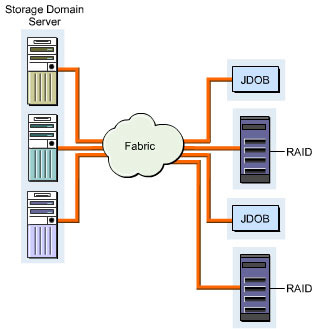
Figure 3-2-2 shows how the virtual storage management system works:
The virtual storage management system allows effective utilization of storage area in a SAN. It also allows you to backup data for storing without connecting to a Local Area Network (LAN). The process of data backup without connecting to LAN increases the speed of data backup and bandwidth available to the client computers.
The storage devices, servers, and client computers in a SAN are configured with multiple data paths, which provide uninterrupted transfer of data in case of hardware failure. SANs also provide integrated real-time backup and recovery to ensure high availability and security of data. In a SAN, you can use FC for greater bandwidth to speed up data backup operations.
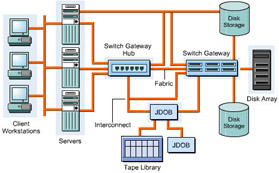
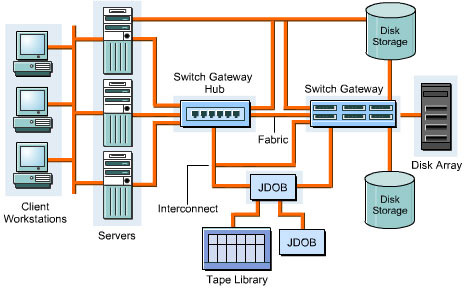
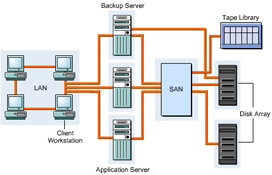
Components of a SAN
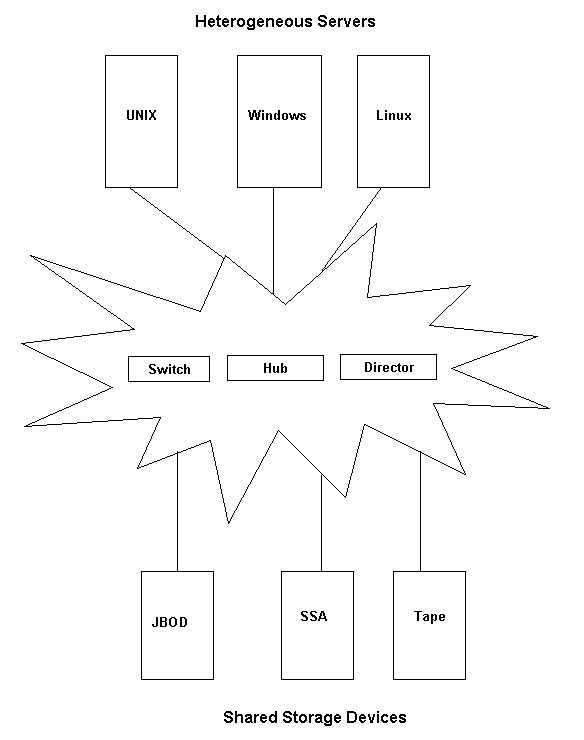
In a SAN, there are various components, such as SAN servers and SAN storage, which are used for data communication. The components used in SAN are based on FC
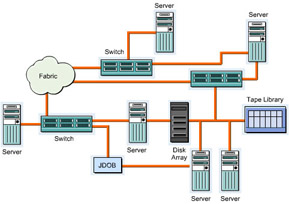
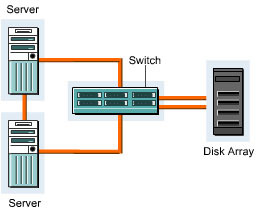
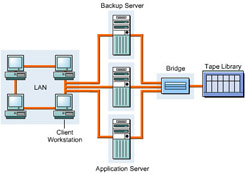
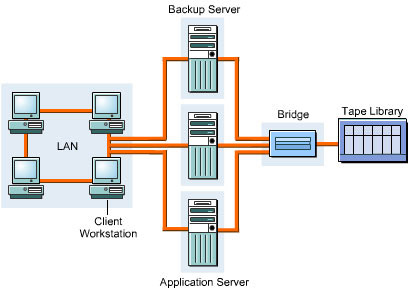
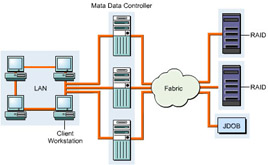
Figure 3-2-3 shows the various components of SAN:
The components used in a SAN are:
-
SAN servers: Include servers with different operating systems, such as UNIX, Windows 2000, and Netware.
-
SAN storage: Includes storage devices that store data.
-
SAN interconnects: Represent components that connect SAN servers and storage devices. The SAN interconnects components are:
-
Cable and connector: Includes Multi-Mode Fiber (MMF) and Single-Mode Fiber (SMF) fiber optic cables and connectors, which help to connect fiber-optic-based adapters in a SAN. The MMF fiber optic cable helps in connecting devices with a distance of 1.2 miles between them. The SMF fiber optic cable allows you to connect devices with a distance of 61.3 miles between them.
-
Gigabit interface converter: Specifies a laser-based, hot-pluggable transceiver that helps in data communication.
-
Host bus adapter: Specifies a device that connects to a server or a storage device and controls the electrical protocol and communications.
-
Extender: Specifies a device that connects servers and storage devices, which are located at long distances.
-
Hub: Specifies a device that connects storage devices, servers, and client computers.
-
Gateway: Specifies a device that helps interconnect one or more storage devices with different protocol support, such as SCSI to FC or FC to SCSI devices.
-
Switch: Specifies a device that helps connect a number of storage devices and servers.
-
Director: Specifies a device that connects Fibre Connection (FICON) or FC devices.
-
SAN Applications
There are various applications in which you can use a SAN to enhance the performance of the network in an organization. They are:
-
Shared repository and data sharing
-
Network architecture
-
Data vaulting and data backup
-
Data interchange
-
Clustering
-
Data protection and disaster recovery
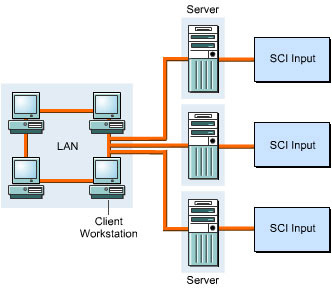
Shared Repository and Data Sharing
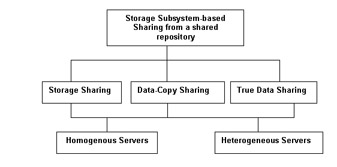
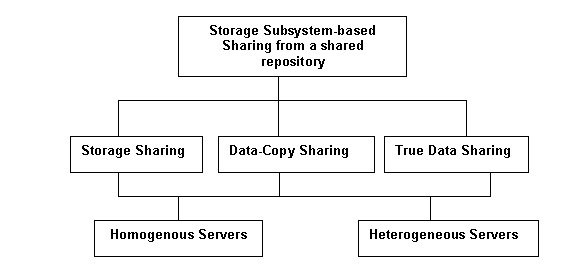
SANs allow you to store data in a shared repository, which is a collection of storage devices shared by various servers. SAN also allows data sharing in which the data stored in the shared repository can be shared between servers for processing.
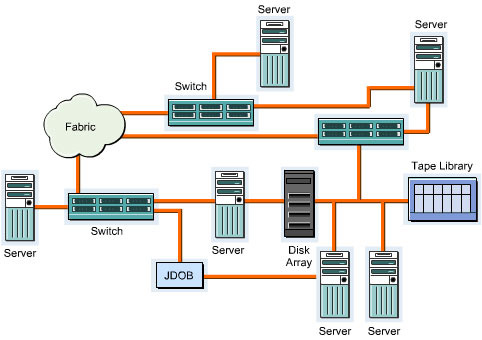
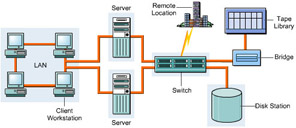
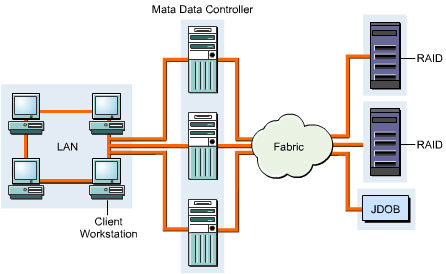
Figure 3-2-4 shows how data is shared between different servers:
In a SAN, data sharing between servers can be of three types, which are:
-
Storage sharing: Allows two or more heterogeneous or homogeneous servers to share data from a single shared repository. The storage area in the repository is partitioned and each partition is allocated to a single server. The server can only access the data stored in the storage area partition, which is allocated to it.
-
Data-copy sharing: Allows one or more homogenous or heterogeneous servers to share data by sending a copy of the data from one heterogeneous or homogeneous server to another heterogeneous or homogeneous server.
-
True data sharing: Allows one or more homogeneous or heterogeneous servers to access a single copy of the data stored in a shared repository.
Network Architecture
SANs allow you to have a network architecture, which is a combination of two networks, messaging network, such as Ethernet, and a SAN as the secondary network. In the network architecture, you can have a centralized storage system by using interconnected devices, such as hubs, switches, and gateways. The network architecture also allows a SAN to be a local or remote network and a shared or dedicated network. The network architecture of a SAN enhances the availability and performance of the storage devices.
Data Vaulting and Data Backup
In a SAN, you can perform data vaulting and data backup processes without the storage devices and servers being connected to each other in a LAN. In a SAN, the data backup process is fast because you need not connect storage devices and servers to each other in LAN to perform data backup process. Data vaulting is a process in which data is stored in storage devices to avoid loss of data due to failures, such as hardware failures. Data backup is a process in which you back up the data stored on a server to a storage device.
Data Interchange
Data interchange refers to transfer of data from one storage device to another. A SAN allows you to interchange data between different storage devices, which help to store and access data using methods, such as data encoding and file structure.
Clustering
The clustering process provides fault tolerance by connecting multiple servers to each other. In clustering, you can use another server if one server fails because clustering allows multiple servers to be connected to each other. SANs allow sharing of storage devices if you are using clustering in a network.
Data Protection and Disaster Recovery
SANs allow you to create duplicate copies of the data that are stored in storage devices to protect and recover data in case of a failure. You can use various methods, such as storage mirroring, remote cluster storage, and Peer-to-Peer Remote Copy (PPRC) to create duplicate copies for protecting data.
Managing SANs
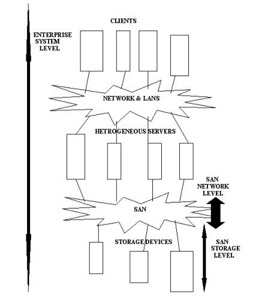
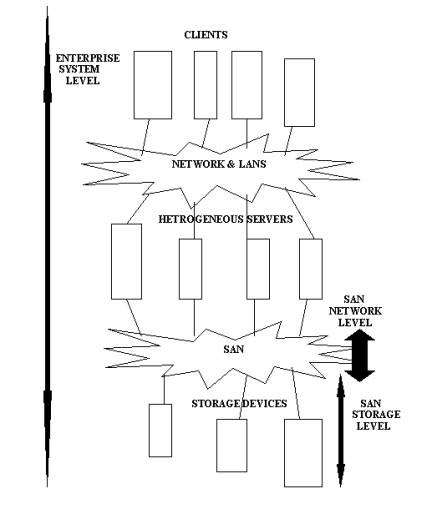
SAN management involves management of servers, storage devices, and network system. A SAN is managed at three levels: storage, network, and enterprise systems. These levels help to simplify management of components used in a SAN, as shown in Figure 3-2-5:
SAN Storage Level
The SAN storage level contains storage devices, such as disks, tapes, and storage subsystems. SAN storage level management involves the management of storage devices and connected servers.
At the storage level, you can use three types of protocols: Small Computer System Interface (SCSI) protocol, SCSI-3 serial protocol, and American National Standard Institute (ANSI) SCSI-3 serial protocol, to manage storage devices. SCSI is a high-level protocol that supports various types of storage devices in a SAN. SCSI-3 serial protocol is higher version of SCSI that supports higher speed of data transfer on a SAN. The ANSI SCSI-3 serial protocol is compatible with FC technology.
The ANSI SCSI-3 serial protocol provides a set of services known as SCSI Enclosure Services (SES) that indicate the status of storage devices on a SAN. SES includes a set of commands, such as DIAGONOSTICS and RECEIVE DIAGONOSTICS RESULTS, for finding the temperature, fan speed, power supply status, and operational parameters from connected storage devices. You can configure the operational parameters of connected storage devices to obtain maximum output from storage devices.
Storage Management Tools
At the storage level, you can use various SAN storage management tools, which help monitor and manage storage devices. These SAN storage management tools are:
-
IBM TotalStorage Enterprise Tape 3494 Library Specialist: Allows you to monitor and centrally manage the IBM Enterprise Storage Server (ESS), including the TotalStorage Virtual Tape Server.
-
IBM TotalStorage LTO Tape Library Specialist: Allows you to monitor and centrally manage all the tape libraries in the LTO Tape Library Family.
-
IBM TotalStorage ETL Expert: Allows you to monitor the status and performance of Tape Library and Virtual Tape Server.
-
FAStT Storage Manager: Allows you to centrally manage the performance of storage devices. It also helps in storage partitioning and error reporting of storage devices.
At the storage level, you can also use IBM StorWatch storage management tool to manage storage devices on a SAN. The IBM StorWatch management tool helps to install, monitor, and configure storage devices. In addition, IBM StorWatch also provides storage management capabilities to storage devices and SAN fabric components, such as logical and physical disk devices, tape drives, FC switch, and FC hub.
IBM Storwatch Storage Management Tool
The IBM StorWatch management tool contains a set of software products and configuration tools for managing storage devices on a SAN. The various software products of IBM StorWatch are:
-
StorWatch Serial Storage Expert: Monitors the Serial Storage Architecture (SSA) network devices for errors or faults. The StorWatch serial storage expert also allows you to organize, configure, and centrally manage SSA networks.
-
StorWatch Versatile Storage Specialist: Allows you to configure, monitor, and centrally manage the IBM versatile storage servers.
-
StorWatch Enterprise Storage Server Specialist: Allows you to configure, monitor, and centrally manage the IBM Enterprise Storage Server (ESS).
-
StorWatch Enterprise Storage Server Expert: Allows you to manage the performance of ESS, keeps track of total capacity, assigned capacity, and free capacity on ESS anywhere in the enterprise, and identify the other servers accessing data from ESS.
-
StorWatch Reporter: Provides capacity and utilization management for server platforms, such as Windows NT, OS/390, OS/400, AIX, and SOLARIS.
-
StorWatch Fibre Channel Redundant Array of Inexpensive Disks (RAID) Specialist: Provides configuration, performance, error handling, and management solutions for FC RAID storage servers.
-
StorWatch Data Path Optimizer: Provides dynamic allocation of paths between various connected storage devices on a SAN. It also provides load-balancing algorithm among connected host devices on a SAN.
SAN Network Level
SAN network level includes the management of various network devices, such as cables, FC switches, FC hubs, routers, and gateways. You can use the features of Simple Network Management Protocol (SNMP) to manage network devices on a SAN. SNMP is an IP-based protocol, which includes a set of instructions for receiving the status and operational parameters of network devices on a SAN. In SNMP based management, an SNMP manager manages all the network devices. All managed network devices are loaded with SNMP based applications. The managed data is arranged in a format called Management Information Base (MIB). The MIB contains the operational parameters of a particular networking device, which you want to measure.
Storage Networking Industry Association (SNIA) has defined standard MIBs for the network devices, such as FC switches, FC hubs, and gateways used in a SAN. SNMP manager obtains the status information of these network devices using the standard MIBs defined by SNIA. The network administrator observes and configures the operational parameters of network devices to manage the network devices in a SAN.
At the network level, you can use various SAN network management tools to monitor and manage network devices in a SAN. These SAN network management tools are:
-
IBM TotalStorage SAN Data Gateway Specialist: Provides configuration, disk copy management, and device monitoring for IBM SAN data gateways.
-
IBM TotalStorage SAN Switch Specialist: Provides configuration, network traffic management, alerts, and device monitoring for IBM SAN 2109 family switches.
-
Fabric Manager: Provides monitoring and management of network devices in a SAN. For example, you can use the Fabric Manager tool to obtain the status of all switches. It also helps create error logs of network devices.
-
Cisco Manager: Allows you to manage multiple switches. It also helps perform various functions, such as topology discovery, monitoring, and fault resolution of network devices.
-
McDATA Enterprise Fabric Connectivity Management: Provides centralized management of multiple, distributed switches and directors. It also allows you to add network devices in a SAN.
-
Emulex HBAnyware Management Software: Provides centralized management of HBAs. It uses driver-based technology for complete management of Emulex HBAs.
-
EZ Fibre: Provides graphical user interface for easy installation and configuration of HBAs in Windows, Macintosh, or Solaris platforms.
-
FINISAR SAN Performance Tool: Provides intelligent testing and monitoring of network device performance in a SAN.
Enterprise System Level
Enterprise system level includes management of the complete network system and host devices in an organization. Enterprise system management applications, such as Common Information Model (CIM), collect the management information of various enterprise network infrastructures, such as host devices, servers, LAN, WAN, and storage devices. Enterprise system management applications integrate the management data of the complete network infrastructure and present consolidated management information.
At the Enterprise System level, you can use various enterprise management tools to monitor and manage the enterprise network infrastructures. These enterprise management tools are:
-
Web Based Enterprise Management: Provides management of enterprise network infrastructures using a Web interface.
-
Common Interface Model: Integrates the management information of host devices and networks distributed over an enterprise.
-
Application Program Interface: Helps write application program for the management of host and network devices in the enterprise.
-
Java Management Application Program Interface: Provides management of Java computing platforms in the enterprise.
-
Desktop Management Interface: Provides management of operating systems, and host and network devices, such as workstations, routers, and hubs.
SAN Topologies
A topology is the physical or logical arrangement of connected host devices on a network. In a SAN, you can use three types of topologies, which are:
-
Point-to-Point topology
-
Arbitrated Loop topology
-
Switched topology
Point-to-Point Topology
Point-to-Point topology is a direct high-speed link between two connected host devices in a SAN.
Figure 3-2-6 shows the connected host devices using point-to-point topology in a SAN:
You use point-to-point topology when you want to transfer data between connected host devices in a SAN at high speed. For example, you can use point-to-point topology to transfer data between central processing units or from a host device to a specialized graphics processor.
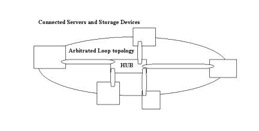
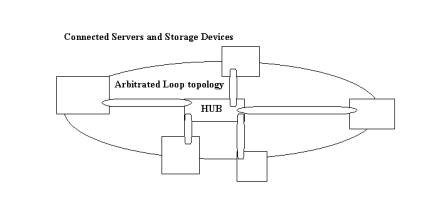
Arbitrated Loop Topology
In Arbitrated Loop topology, you can use up to 126 host devices connected to each other in a single loop in a SAN. This Arbitrated Loop topology helps in data transfer at high bandwidth at a low cost. In Arbitrated Loop topology, the hosts establish a virtual connection with each other. When two hosts establish a virtual connection with each other, the complete bandwidth of the loop is dedicated to that virtual connection. The bandwidth of the loop is dedicated until the data transfer between the connected host devices is complete. You can connect loops to each other through connectors.
Figure 3-2-7 shows the SAN Arbitrated Loop topology:
Switched Topology
Switched topology allows you to increase the bandwidth of a particular network path, distribute the network traffic, and interconnect various host devices using FC switches in a SAN. The Switched topology helps manage networks that have large number of hosts. In a Switched topology, you can use up to sixteen million nodes and data rate of 100 MegaBytes/second between any two connected devices.
You can cascade switched topology by using multiple FC switches. Multiple FC switches help connect servers and storage devices. In cascaded Switched topology, you can interconnect and configure multiple FC switches to form one integrated switch. You need to properly manage the links between the switches so that if any of the switches fail, the functioning of the other switches should not be disrupted.
Optimizing SAN Performance
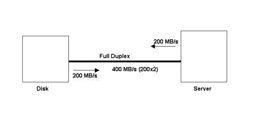
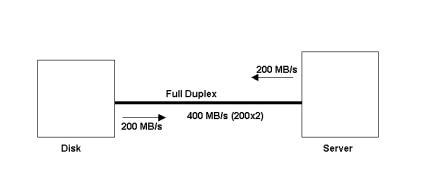
You can optimize SAN performance by planning, monitoring, analyzing, testing, and tuning a SAN. The first step in optimizing SAN performance is to plan what components of a SAN will be used, such as appropriate selection of connectors. In addition, you need to select SAN topologies, which will be used to connect host devices in a SAN. You can also monitor the performance of a SAN using monitoring tools, such as NetWisdom. For example, you monitor data traffic in a SAN and the working of SAN components using the monitoring tools. Analyzing and testing SAN performance helps find the errors that degrade the performance of a SAN. You can also tune the performance of a SAN to remove the errors, which degrade the performance of a SAN.
Planning SAN Performance
In the planning stage, you need to install servers in a SAN and plan for the clustering of servers to reduce the downtime caused due to the unavailability of servers. During planning, you also select connectors, such as hubs, routers, and FC switches that help in maintaining high data transfer rate in a SAN. For example, you can insert 500Mbps switch between two 1Gbps switches to reduce the data transfer rate in a SAN. In case of failure of a data path in a SAN, you need to allocate alternate data paths to FC packets so that the FC packets reach the destination host devices.
If you are implementing low capacity connectors in a SAN, you can use these connectors over less critical data paths and redundant fail over data paths in a SAN. You can also use a number of low capacity components instead of a single high capacity component to safely transmit data in a SAN. Using a number of low capacity components is advantageous because if one component fails, another component can take over the function of the failed component. For example, in RAID application, several low capacity storage devices are used instead of one large storage device for backup operation. In addition, you need to select SAN topologies based on your requirements while planning SAN performance.
After you have implemented a SAN, new storage devices, connected servers, and connectors in the network can change the behavior or performance of network. In addition, there can be a number of end user applications in a SAN that are accessing a single network resource. As a result, you need to provide multiple data paths to reach a single connected device so that multiple end user applications can access the network resources in a SAN at the same time.
Monitoring SAN Performance
Monitoring SAN performance helps in obtaining maximum performance from servers, storage devices, and connectors connected to each other in a SAN. There are various monitoring tools, such as NetWisdom and McDATA SANavigator, which allow you to obtain the status and value of operational parameters, such as data traffic in a SAN. You can also use the monitoring tools to monitor the functions of each connected device and SAN components.
Net Wisdom
NetWisdom is a tool for monitoring SAN performance. It helps obtain information about the SAN operational parameters, which you can use to increase the performance of a SAN. NetWisdom provides various operational parameters for monitoring SAN performance, which are:
-
Comprehensive Monitoring: Compiles and analyzes detailed SAN operational parameters on FC technology.
-
SAN Bandwidth Utilization: Shows an aggregate view of network traffic across the fabric of a SAN. It also shows the data bandwidth over a SAN and its utilization.
| Note | Fabric specifies the network connection in a SAN using various network devices, such as hubs, switches, and gateways. |
-
Measurement of Applications Response Times: Measures the response time of applications between the source and destination hosts.
-
Draw Performance Baselines: Constructs the performance baselines of a SAN and compares performance baselines to the real operating performance of a SAN.
-
Problem Detection: Detects the main source of problem, so that it can be eliminated in real time.
-
Trend Analysis: Prepares a log of performances over a period of time, and compares the performances with the current working of SAN to identify the deviation and root cause of problems.
-
Custom Alarm: Sets user-defined alarms and informs the administrator when performance baselines are not achieved.
-
Event Recording: Records each event that occurs in a SAN. This helps troubleshoot the problems that might occur in a SAN.
-
Workload Balancing: Distributes the workload uniformly across the SAN.
-
Centralized Control: Allows centralized management and monitoring of a SAN.
NetWisdom monitoring tool provides various advantages, such as accurate measurement of SAN performance. NetWisdom also helps maximize SAN performance, which provides reliability and minimizes downtime of data transfer. NetWisdom creates performance baselines to measure the real working performance of a SAN. NetWisdom contains three components, which are:
-
Probes: Collects data through SAN components and calculates the data traffic and the transaction statistics over the SAN. Probes are individual hardware monitoring devices that are connected to the SAN fabric. These hardware devices extract the data rate locally between connected hosts in a SAN.
-
Portal: Collects and stores the data from probes. This auto managed database integrates the transaction statistics over time, stores user-defined instructions, and sets custom alarm in probes.
-
Views: Provides centralized monitoring of how the entire SAN works. You can view colored graphs and cycles through viewer software to analyze and interpret the data. NetWisdom Views help view the data paths and working of networking components. In addition, administrator can allow multiple authorized end users to access this software simultaneously.
McDATA SANavigator Tool
McDATA SANavigator tool helps monitor and manage the storage devices, networking components, and servers in a SAN. The functions of McDATA SANavigator are:
-
Performance Monitoring: Helps measure the performance of each switch port and locate the bandwidth bottlenecks in a SAN. It also helps provide data path throughput and errors generated in a SAN.
-
Event Management: Helps automate the routine tasks, such as error generation and device failure response in a SAN so that you can respond instantly when an error occurs in a SAN.
-
Planning: Helps in planning how to increase storage capacity of a SAN.
-
Improves Efficiency: Identifies the components of a SAN that are under utilized and over utilized so that you can balance the workload in a SAN.
-
Securing Data: Prevents unauthorized access of data stored in the storage devices in a SAN. The zoning feature manages and configures zones for switches in a SAN.
| Note | Zoning allows segmentation of the switched network in a SAN. Only members of the same zone can communicate within that zone, and all other attempts from outside are rejected. |
Analyzing and Testing Tools for SAN Performance
Analyzing and testing tools help to analyze, diagnose, and display SAN performance. These tools identify and resolve the errors, which occur in a SAN. The various analyzing tools for analyzing SAN performance are:
-
Taps: Allows monitoring, capturing, and analyzing of physical errors in a SAN. Fault tolerant and single port full duplex taps maximize the visibility of SAN performance.
-
Xgig Analyzer Suite: Consists of software and hardware package, which analyzes the problem that degrades the performance of a SAN. This suite also helps test and evaluate the performance of a SAN.
-
Expert: Analyzes and explains the network problem in a SAN. Expert also provides an overview of the problem with corrective action recommendations to resolve the problem.
You can use the following testing tools to test the performance of a SAN:
-
Generators: Generate test data that help to test the data traffic of 1 GB/second and 2 GB/second in SAN.
-
Jammers: Insert controlled, repeatable, and system level errors into a SAN. After inserting the errors, jammer checks for the recovery process to recover data lost due to the errors in a SAN.
-
Bit Error Rate Testers: Provide low level testing, such as testing bit error rate of network devices in a SAN. This testing tool also helps verify data integrity by sending worst-case data patterns through network devices.
-
Traffic Check: Monitors the status parameters, error conditions, and performance measures of network devices in a SAN.
-
Bus Doctor: Connects with multiple buses, such as iSCSI and FC of 1GB/s and 2GB/s. Bus doctor can capture up to 256 million events, which occur in a SAN in their dedicated trace buffers.
-
PacketMaker: Generates data traffic for high-speed serial storage buses, such as serial attached SCSI. PacketMaker also allows you to send illegal packet structures, field values, and other errors to test your serial storage device error handling.
Tuning SAN Performance
When tuning SAN performance, you eliminate the errors in the connected device or the single data path in a SAN. In addition, you can set a threshold performance of a SAN. If the threshold performance is not achieved, SAN performance monitoring tools provide alerts for the error in a SAN.
Visual indicators in SAN performance monitoring tools help isolate the degraded performance data path or component of a SAN. If the error is related to the data path and this data path contains various storage devices, servers, and connectors, the error can be related to any connected device in this path. You need to analyze all the connected devices in the degraded performance data path to troubleshoot the error and tune the SAN performance.
You should monitor the performance of all connected devices in the data path and identify whether any of the devices has degraded the performance of the data path. If the data path uses full data bandwidth, you need to provide additional bandwidth capacity in the data path. If the data bandwidth is within limit in the data path and the source device performs well but the destination host device is not responding, the connected device or connection contains an error. You also need to replace the cable or connector, if the performance degrades.